Why Network Security Monitoring is Critical for New Jersey Businesses
Network security monitoring nj services have become essential for protecting businesses from cyber threats that can compromise operations within minutes. Here’s what New Jersey business owners need to know:
Key Components:
• Real-time threat detection – Monitors network traffic 24/7 for suspicious activity
• Log analysis – Reviews security logs to identify early warning signs
• Automated response – Blocks threats before they cause damage
• Compliance support – Helps meet HIPAA, PCI DSS, and other regulatory requirements
Critical Benefits:
• Reduces Mean-Time-to-Detect (MTTD) cyber threats
• Prevents the 60% of small businesses that close within six months of a breach
• Maintains business continuity and customer trust
• Provides audit trails for regulatory compliance
When your network goes down, the financial consequences happen in real time. Internal communication stops, orders can’t be placed or tracked, and your online reputation suffers. This is why proactive monitoring has evolved from a competitive advantage to a business necessity.
The threat landscape is particularly challenging for New Jersey businesses. With cybercrime rates higher than ever due to increased cloud adoption and remote work, attackers can compromise and exfiltrate data within minutes if networks aren’t properly monitored.
I’m Paul Nebb, founder of Titan Technologies, and I’ve spent over 15 years helping New Jersey businesses implement network security monitoring nj solutions that protect against evolving cyber threats. My experience includes speaking at major venues like the Nasdaq podium and West Point Military Academy about cybersecurity risks and protection strategies.
Network security monitoring nj vocab to learn:
– Managed IT services Elizabeth
– Network solutions Elizabeth NJ
Network Security Monitoring NJ: Why It Matters
Let’s be honest about something that keeps business owners up at night: cyber threats aren’t going away, and they’re getting worse. For New Jersey businesses, network security monitoring has shifted from “nice to have” to “absolutely essential for survival.”
The numbers tell a stark story. 60% of small businesses close their doors forever within six months of a major cybersecurity breach. We’re not talking about just losing some data here—we’re talking about losing everything you’ve worked to build.
The financial devastation goes way beyond the initial attack. Regulatory fines can crush smaller operations overnight. HIPAA violations alone can cost anywhere from $100 to $50,000 per exposed patient record. But here’s what really hurts: the damage to your reputation. Once customers lose trust in your ability to protect their information, winning them back becomes an uphill battle.
Network security monitoring nj solutions address a harsh reality—your business has more ways to get attacked than ever before. Remote employees working from coffee shops, cloud applications storing sensitive data, and digital transactions happening around the clock have created countless entry points for cybercriminals.
The key metric that can make or break your business is Mean-Time-to-Detect (MTTD). Think of it this way: the faster you spot trouble, the less damage it can do. Professional monitoring dramatically reduces MTTD, giving you a fighting chance to stop attacks before they destroy your operations.
Local Threat Landscape for NJ Firms
New Jersey businesses face some unique challenges that make us particularly attractive to cybercriminals. Our location near major financial centers, combined with our concentration of healthcare, manufacturing, and professional services companies, puts a big target on our backs.
Phishing attacks remain the most common way criminals get their foot in the door. We’ve seen attackers do their homework, researching local business relationships and crafting emails that look like they came from your trusted partners. These aren’t the obvious “Nigerian prince” scams anymore—they’re sophisticated, personalized attacks that can fool even tech-savvy employees.
Ransomware has become a serious nightmare for businesses across our region. Recent attacks on critical infrastructure like water treatment facilities and transportation systems show that cybercriminals view New Jersey as a high-value hunting ground. When one business gets hit, the attack often spreads to connected partners and suppliers.
Supply-chain attacks represent a growing threat that many business owners don’t see coming. When criminals compromise a vendor or service provider you trust, they automatically gain access to your network too. This domino effect is particularly concerning for businesses in areas like Trenton and Newark, where many companies share infrastructure and services.
The state and federal government have taken notice, implementing new regulations that require improved monitoring for businesses supporting critical infrastructure. This includes not just obvious targets like utilities, but also companies providing IT services, financial processing, or healthcare support.
Business Benefits & Risk Reduction
Implementing comprehensive network security monitoring nj solutions delivers benefits that go far beyond just stopping hackers. Lower MTTD means less business disruption and faster recovery when something does go wrong.
Proactive maintenance capabilities built into modern monitoring systems help prevent equipment failures before they shut down your operations. By continuously tracking device health and performance, we can schedule maintenance during off-hours instead of dealing with emergency outages that cost thousands of dollars per hour.
Customer trust has become a major competitive advantage. Businesses that can demonstrate robust security monitoring often win contracts over those that can’t provide the same peace of mind. This is especially important for professional services and healthcare organizations throughout Central New Jersey.
The competitive edge you gain from reliable network operations is huge. While your competitors deal with outages, security incidents, or compliance failures, your business keeps running smoothly and serving customers effectively. That’s the kind of reliability that builds long-term success.
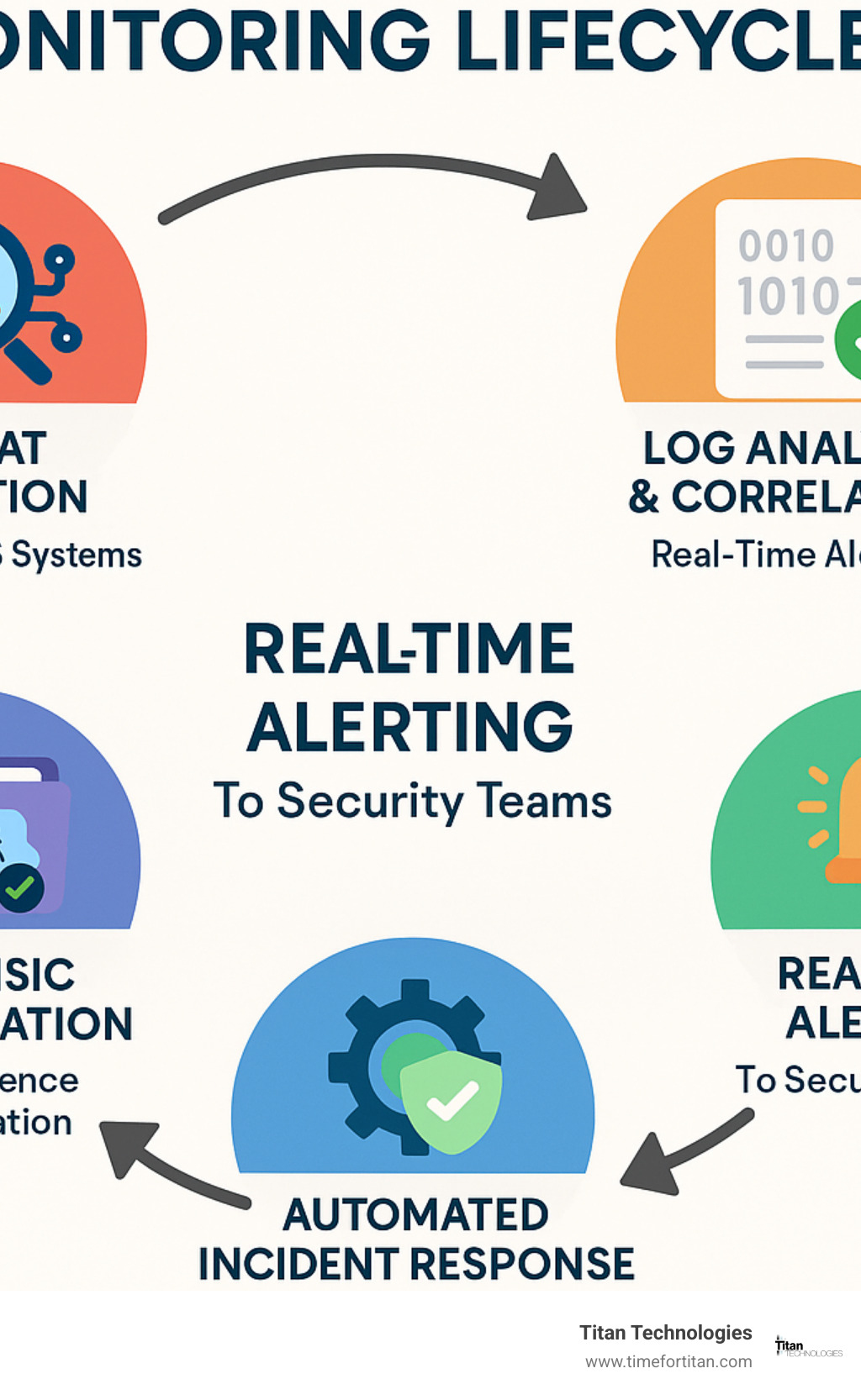
How Monitoring Works: Components, Threats & Detection
Modern network security monitoring relies on multiple integrated components working together to provide comprehensive threat detection and response capabilities. At the foundation sits the Security Information and Event Management (SIEM) system, which centralizes and normalizes log data from all network-attached devices.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) monitor network traffic in real-time, analyzing packet flows for known attack signatures and suspicious behavior patterns. These systems can automatically block malicious traffic while alerting security teams to investigate potential threats.
Endpoint agents deployed on workstations, servers, and mobile devices provide visibility into user activities and system behaviors that might indicate compromise. These agents collect detailed telemetry data that helps security analysts understand the full scope of potential incidents.
Threat intelligence feeds improve detection capabilities by providing real-time information about emerging threats, known bad IP addresses, malicious domains, and attack indicators observed in the wild. This intelligence helps monitoring systems identify threats that haven’t been seen before in your specific environment.
A 24/7 Network Operations Center (NOC) staffed by security experts provides the human intelligence necessary to interpret alerts, investigate incidents, and coordinate response activities. Automated systems generate alerts, but experienced analysts determine which threats require immediate action and how to respond effectively.
Anomaly detection capabilities use machine learning and behavioral analytics to identify unusual network activity that might indicate compromise. These systems establish baselines of normal behavior and alert when deviations suggest potential security incidents.
Our Network Operations Center Services provide the 24/7 monitoring and response capabilities that keep New Jersey businesses protected around the clock.
Real-Time Alerting & Automated Response
Real-time alerting systems form the nervous system of effective network security monitoring. Deep packet inspection analyzes network traffic at the application layer, identifying threats that might bypass traditional perimeter defenses. This technology can detect encrypted malware communications, data exfiltration attempts, and command-and-control traffic.
Behavior analytics systems learn normal patterns of user and system activity, then generate alerts when deviations suggest potential compromise. For example, if an employee’s account suddenly begins accessing sensitive files outside normal business hours or from unusual locations, the system can trigger immediate investigation.
Automated response playbooks enable immediate containment actions when specific threat types are detected. These playbooks can isolate infected systems, block suspicious IP addresses, disable compromised user accounts, and initiate backup procedures—all within seconds of threat detection.
Containment capabilities prevent lateral movement of threats within your network. Modern monitoring systems can automatically segment network traffic, preventing attackers from moving from one compromised system to others. This rapid containment significantly reduces the potential damage from successful attacks.
The key to effective real-time response is balancing automation with human oversight. While automated systems can respond to clear threats immediately, complex incidents require human analysis to determine the appropriate response strategy and coordinate recovery efforts.
Log Analysis & Forensics
Centralized log collection and analysis provide the foundation for both real-time threat detection and post-incident forensics. Modern monitoring systems collect logs from firewalls, servers, workstations, applications, and network devices, creating a comprehensive record of all system activities.
Correlation rules analyze relationships between different log events to identify complex attack patterns that might not be obvious from individual events. For example, multiple failed login attempts followed by successful authentication from an unusual location might indicate a successful brute-force attack.
Audit trails maintained through comprehensive logging support regulatory compliance requirements and provide evidence for incident investigations. These trails help organizations understand exactly what happened during security incidents and demonstrate due diligence to regulators and auditors.
Incident evidence preservation ensures that forensic data remains intact and admissible for legal proceedings or insurance claims. Proper log management includes secure storage, chain of custody procedures, and retention policies that meet legal and regulatory requirements.
Advanced analytics capabilities help security teams identify trends and patterns that might indicate emerging threats or vulnerabilities. By analyzing historical data, organizations can improve their security posture and prevent similar incidents in the future.
Network Security Monitoring NJ Compliance Hooks
Network security monitoring nj solutions play a crucial role in meeting various regulatory compliance requirements that affect businesses throughout our state. Understanding these requirements helps organizations implement monitoring systems that serve both security and compliance objectives.
HIPAA requires covered entities to implement administrative, physical, and technical safeguards to protect patient health information. Network monitoring supports multiple HIPAA requirements, including access controls, audit controls, integrity controls, and transmission security. The audit logs generated by monitoring systems provide the documentation necessary to demonstrate compliance during assessments.
PCI-DSS mandates comprehensive monitoring for any organization that processes, stores, or transmits credit card information. Requirement 10 specifically addresses logging and monitoring, requiring organizations to track and monitor all access to network resources and cardholder data. Real-time monitoring helps detect and respond to potential breaches before they impact cardholder data.
CMMC (Cybersecurity Maturity Model Certification) requirements apply to organizations that work with the Department of Defense. These requirements include continuous monitoring, incident response, and security assessment capabilities that network monitoring systems provide.
GDPR affects any organization that processes personal data of EU residents, including many New Jersey businesses with international operations. The regulation requires organizations to implement appropriate technical and organizational measures to ensure data security, including the ability to detect and respond to data breaches within 72 hours.
Mandated Log Retention Periods:
– HIPAA: 6 years from creation or last effective date
– PCI-DSS: Minimum 1 year, with 3 months immediately available
– SOX: 7 years for public companies
– GDPR: Varies by purpose, typically 6 years maximum
– CMMC: 3 years minimum for audit logs
Choosing & Deploying Monitoring Solutions
Making the right choice for network security monitoring nj solutions can feel overwhelming, but it doesn’t have to be. After helping hundreds of Central New Jersey businesses steer this decision, I’ve learned that the key is starting with an honest assessment of where you are today and where you want to be tomorrow.
Your needs assessment should begin with mapping your current network infrastructure. This includes everything from your main office servers to that employee working from their kitchen table in Toms River. We look at your on-premises systems, cloud services, remote workers, and mobile devices to understand the full scope of what needs protection.
Don’t forget about your existing security tools. Many businesses have invested in firewalls, antivirus software, or backup solutions that can integrate with comprehensive monitoring systems. Budget considerations go far beyond the sticker price—you need to think about ongoing operational costs, staff training, and what happens when your business grows.
Scalability planning is crucial, especially for the growing businesses we serve in Lakewood and Freehold. I’ve seen too many companies outgrow their security solutions within a year because they didn’t plan for success. Your monitoring solution should grow with you, not hold you back.
Hybrid cloud environments present unique challenges that require specialized expertise. As more New Jersey businesses adopt cloud services while keeping some systems on-premises, your monitoring needs to work seamlessly across both environments. This isn’t just about technology—it’s about maintaining consistent security policies everywhere your data lives.
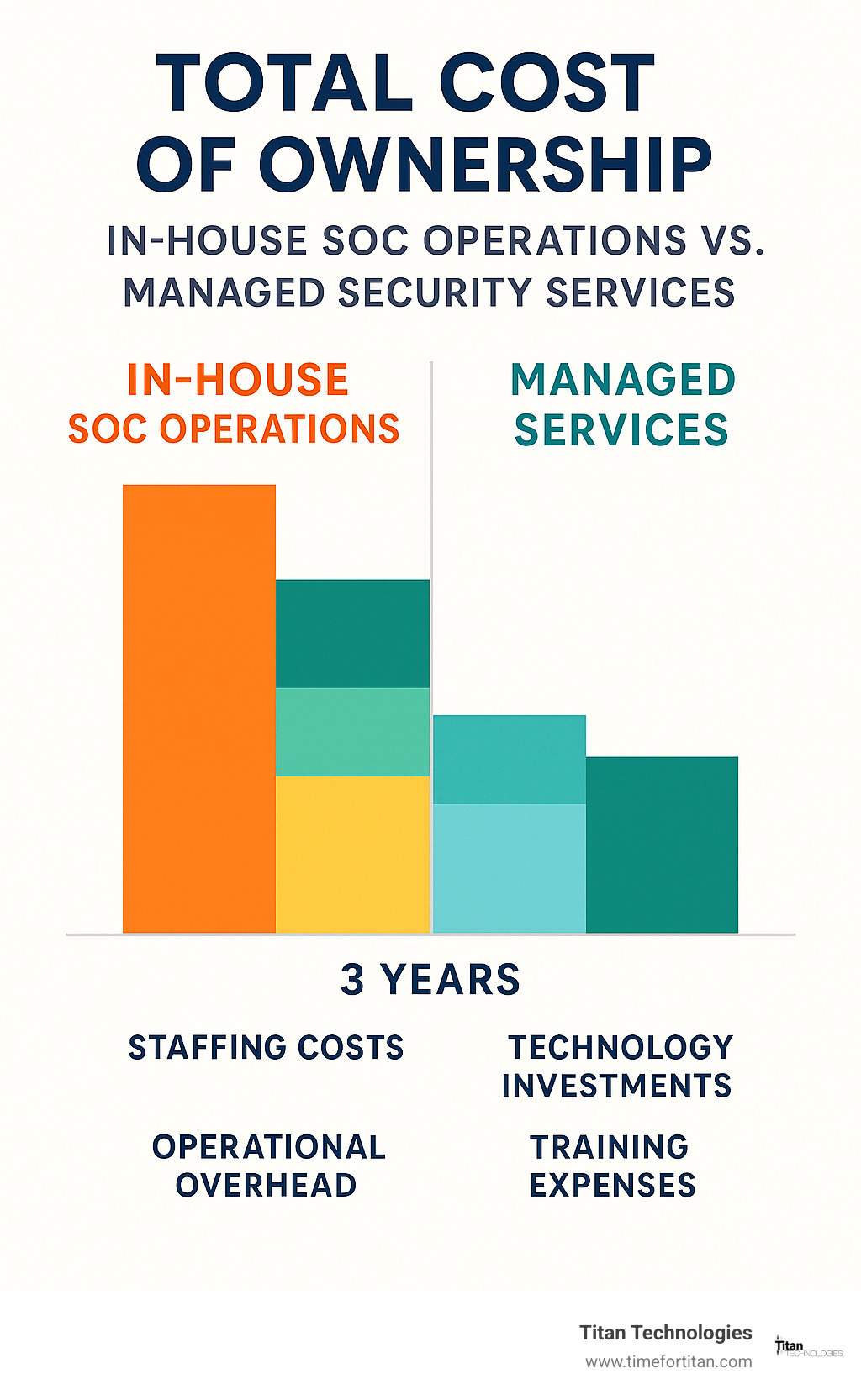
The biggest question most business owners face is whether their team has the expertise to manage complex monitoring systems effectively. This honest self-assessment often determines whether in-house or managed services make more sense for your organization.
| Aspect | In-House Monitoring | Managed Monitoring |
|---|---|---|
| Initial Investment | High CAPEX for hardware/software | Low startup costs |
| Staffing Requirements | 24/7 SOC team (8-12 FTEs) | Included in service |
| Expertise Level | Must hire/train specialists | Access to expert team |
| Scalability | Limited by infrastructure | Easily scalable |
| Technology Updates | Manual upgrades required | Automatic updates |
| Compliance Support | Internal responsibility | Included expertise |
| Response Time | Depends on staff availability | Guaranteed SLAs |
In-House Build-Out
Building your own security monitoring operation sounds appealing until you start adding up the real costs. The hardware CAPEX alone can be staggering—SIEM platforms, network monitoring tools, endpoint detection systems, and threat intelligence feeds all require significant upfront investment before you can even begin monitoring.
Then comes the challenge of hiring SOC talent. Qualified security analysts are expensive and hard to find. You’ll need multiple shifts to provide true 24/7 coverage, which typically means 8-12 full-time employees with specialized skills. In today’s competitive job market, these professionals command premium salaries and often have multiple job offers.
Alert fatigue becomes a real problem when your team lacks the experience to properly tune monitoring systems. I’ve seen organizations become so overwhelmed by false positives that they start ignoring alerts altogether. That’s like having a smoke detector that cries wolf so often you take out the batteries.
Tool sprawl happens when businesses buy multiple security products without thinking about how they’ll work together. Instead of a coordinated defense system, you end up with a collection of isolated tools generating separate alerts that nobody has time to investigate properly.
The ongoing complexity of maintaining current threat intelligence, updating security signatures, and fine-tuning detection rules requires expertise that many organizations underestimate. It’s not just about the initial setup—it’s about staying current with an changing threat landscape.
Managed Service Path (vSOC)
The managed service approach eliminates most of the headaches of in-house monitoring while providing enterprise-grade protection through a subscription model. Virtual Security Operations Centers (vSOC) give you access to 24/7 monitoring and response capabilities without the infrastructure investment or staffing challenges.
SLA guarantees of 99.9% uptime and response times measured in minutes rather than hours provide the reliability that most organizations couldn’t achieve internally. When a critical alert comes in at 2 AM on Sunday, you have experienced security professionals responding immediately instead of hoping someone on your team checks their phone.
Rapid onboarding means you can be protected within days rather than waiting months for internal implementations. Managed service providers have standardized deployment processes and pre-configured monitoring tools that get you protected quickly while your business continues operating normally.
The ability to focus on your core business while security experts handle monitoring represents tremendous value. Instead of diverting your IT team to manage security infrastructure, they can concentrate on projects that directly support business growth and customer service.
Our Network Monitoring and Management services provide comprehensive monitoring capabilities that scale with your business needs while maintaining consistent security standards across all your locations.
Scaling for Growth & Multi-Site NJ Operations
Cloud sensors enable comprehensive monitoring coverage for distributed operations without requiring hardware deployment at each location. These sensors monitor network traffic, endpoint activities, and cloud services from centralized platforms while providing local response capabilities wherever your business operates.
Bandwidth planning becomes critical as your monitoring systems collect and analyze increasing amounts of data from growing networks. You need to balance comprehensive coverage with network performance, especially for locations with limited internet connectivity. Nobody wants their security system to slow down their business operations.
Micro-segmentation strategies help contain threats within specific network segments while enabling detailed monitoring of traffic flows between different areas of your network. This approach works particularly well for organizations with multiple locations or business units that need different security policies.
Zero-trust architecture assumes that no network traffic should be trusted by default, requiring continuous verification and monitoring of all communications. This approach provides improved security for distributed operations while giving you detailed visibility into all network activities across your organization.
Geographic distribution of monitoring capabilities ensures effective security coverage even if primary monitoring centers experience outages or attacks. This redundancy is especially important for businesses with operations across multiple New Jersey locations who can’t afford security blind spots.
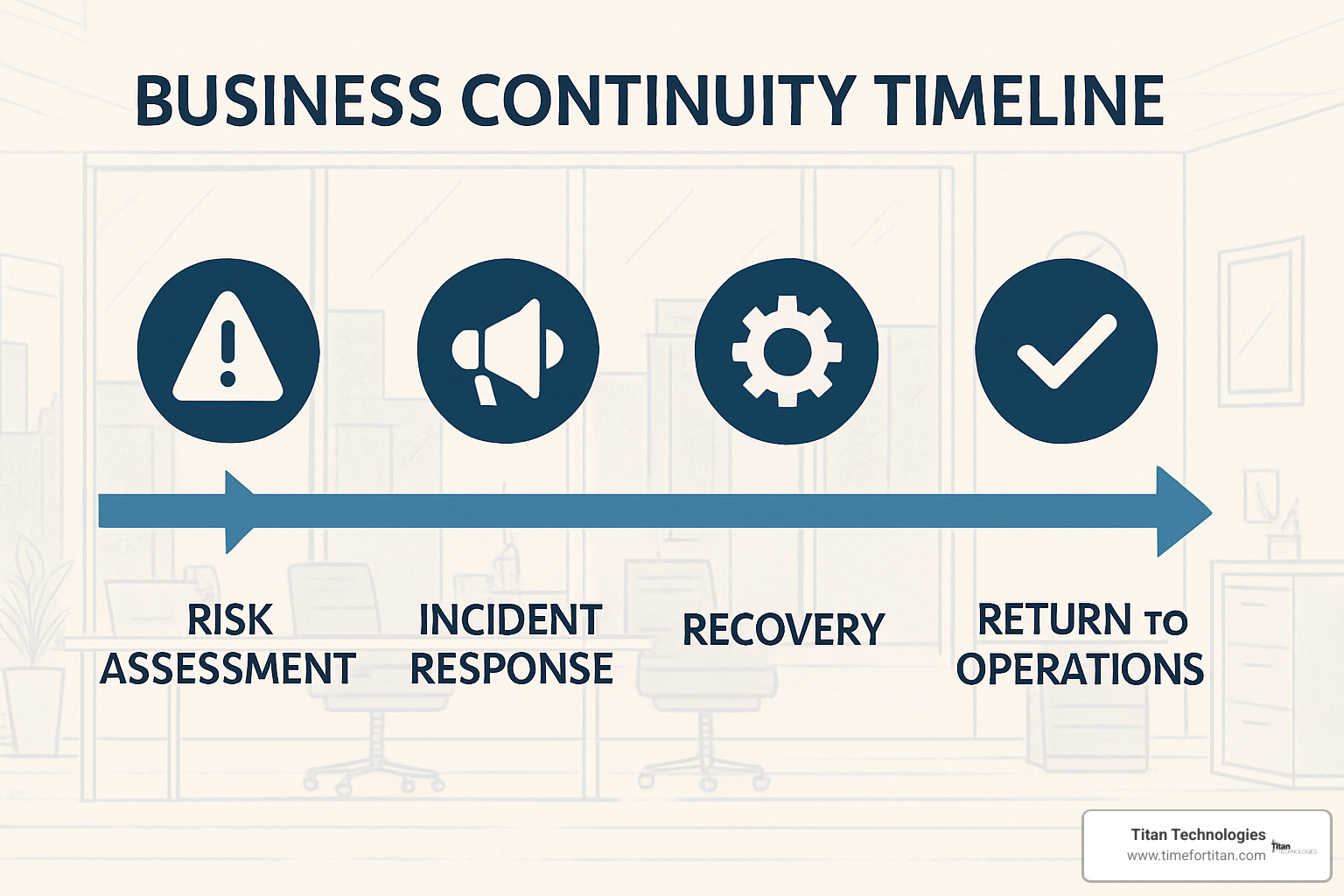
Compliance, Business Continuity & ROI
Let’s talk about the bottom line—because network security monitoring nj isn’t just about preventing attacks, it’s about protecting your business investment and ensuring you can keep serving customers no matter what happens.
When we conduct risk assessments for Central New Jersey businesses, we often find that owners underestimate how much a security incident could actually cost them. It’s not just the immediate damage—it’s the ripple effects that can impact your business for months or even years.
Think about it this way: if your network goes down for even a few hours, you’re losing revenue, productivity, and customer confidence simultaneously. But when you integrate network security monitoring nj with your Business Continuity and Disaster Recovery (BCDR) planning, you’re building a safety net that catches problems before they become disasters.
Here’s something that might surprise you—many cyber insurance companies now offer premium reductions for businesses with comprehensive monitoring systems. They’ve done the math and realized that well-monitored organizations are simply better risks. Some of our clients have seen their insurance costs drop significantly after implementing proper monitoring.
The numbers from scientific research on breach costs are sobering. The average cost of a data breach now exceeds $4 million. When you compare that to the cost of monitoring services, the ROI becomes crystal clear. It’s like paying for a fire sprinkler system—you hope you’ll never need it, but you’re grateful it’s there when trouble strikes.
Our Network Infrastructure Management Services integrate security monitoring with your broader infrastructure needs, giving you comprehensive protection that makes business sense.
Integrating Monitoring Into DR/BC Plans
Your disaster recovery plan is only as good as your ability to detect when you need it. That’s where Recovery Point Objective (RPO) and Recovery Time Objective (RTO) metrics become crucial. These fancy terms simply answer two critical questions: “How much data can we afford to lose?” and “How quickly do we need to be back up and running?”
Security monitoring systems act as your early warning system, giving you the visibility you need to make smart decisions during a crisis. When something goes wrong, you don’t want to be flying blind, trying to figure out what happened while your customers are waiting.
Automated failover capabilities can be a lifesaver—literally. When monitoring systems detect that your primary systems are failing, they can automatically switch operations to backup systems. This happens so fast that your customers might never even notice there was a problem.
We always recommend tabletop exercises that include security monitoring scenarios. Think of these as fire drills for your IT systems. They help you practice what you’ll do when real problems occur, and they often reveal gaps in your planning that you didn’t know existed.
The communication protocols built into modern monitoring systems ensure that the right people get notified at the right time. No more playing phone tag during an emergency or wondering if everyone knows what’s happening.
Plus, all those monitoring logs automatically create the documentation you need for regulatory compliance and insurance claims. When auditors or insurance adjusters come calling, you’ll have detailed records showing exactly what happened and how you responded.
Calculating Return on Security Investment
Let’s get practical about the money. Reduced downtime hours provide the clearest ROI for most businesses. Every hour your systems are down costs you money—lost sales, idle employees, frustrated customers. When monitoring prevents even one significant outage, it often pays for itself.
Avoided regulatory penalties can be huge. A single HIPAA violation can cost more than years of monitoring services. We’ve seen businesses face fines that could have been prevented with proper monitoring and response procedures.
The productivity gains are often overlooked but equally important. When your IT team isn’t constantly fighting fires, they can focus on projects that actually grow your business. Instead of spending their time recovering from security incidents, they’re improving systems and supporting your strategic goals.
Customer retention might be the biggest benefit of all. In today’s market, customers expect you to protect their data. When you can demonstrate robust security practices, you gain a competitive advantage. Businesses that suffer public security breaches often struggle to win back customer trust.
Here’s the key—you need to track your baseline before implementing monitoring, then measure improvements over time. Keep records of security incidents, downtime events, and compliance costs. When you can show clear before-and-after numbers, the ROI becomes undeniable.
The math is simple: prevention costs less than recovery. Much less.
Frequently Asked Questions about Network Security Monitoring NJ
What threats can continuous monitoring actually stop?
When business owners ask me what network security monitoring nj can actually protect them from, I tell them to think of it like having a security guard who never sleeps, never takes breaks, and can watch every corner of your digital business at once.
Malware infections get caught the moment they try to “phone home” to their criminal controllers. Your monitoring system sees these suspicious conversations and cuts them off before any real damage happens. It’s like catching a burglar while they’re still trying to pick the lock.
Ransomware attacks are particularly satisfying to stop because they’re so destructive when they succeed. These attacks create very specific patterns when they start encrypting your files—patterns that monitoring systems recognize immediately. We can isolate the infected computer before it spreads to your shared drives or backups, saving you from potential disaster.
Insider threats are trickier because they involve people who already have legitimate access to your systems. But monitoring catches the unusual behavior—like someone accessing sensitive files at 3 AM or downloading massive amounts of data they don’t normally need. Sometimes it’s a disgruntled employee, sometimes it’s just someone who clicked the wrong thing, but either way, we spot it fast.
Data theft attempts show up clearly when monitoring systems track what’s leaving your network. If someone tries to steal your customer database or send your trade secrets to competitors, the monitoring system sees those unusual data transfers and stops them cold.
The sneakiest threats are Advanced Persistent Threats (APTs)—sophisticated attackers who use stolen credentials and move slowly to avoid detection. They might hide in your systems for months, but continuous monitoring eventually spots the subtle patterns that give them away.
How quickly will my team receive alerts?
Speed matters when your business is under attack, so let me break down exactly what to expect when threats are detected.
Critical threats that indicate active attacks get our immediate attention—we’re talking minutes, not hours. If ransomware is detected or someone’s actively stealing your data, you’ll get phone calls, text messages, and emails simultaneously. We don’t mess around with the serious stuff.
Our 24/7 SOC team follows specific escalation procedures for these critical alerts. If the automated systems can’t handle it immediately, a real person gets involved to coordinate the response and make sure the threat is properly contained.
Medium-priority alerts for suspicious activities usually reach you within 15-30 minutes. These might be things like multiple failed login attempts or unusual network activity that needs investigation but isn’t immediately dangerous. You’ll get detailed information about what triggered the alert and what we recommend doing about it.
Routine security events get bundled into daily or weekly reports so you’re not drowning in notifications about normal network activity. These reports help you understand your overall security posture without creating alert fatigue for your team.
The key is having monitoring systems that know the difference between “the building is on fire” and “someone left a light on.” Good monitoring prioritizes alerts intelligently, so you get immediate notification for real threats without being overwhelmed by false alarms.
Will monitoring help me pass an upcoming compliance audit?
If you have a compliance audit coming up, network security monitoring nj solutions can be your best friend—or at least make the process much less stressful.
Audit documentation is where monitoring really shines. Those detailed logs that monitoring systems automatically generate? They’re exactly what auditors want to see. Instead of scrambling to prove you had proper security controls in place, you can hand over comprehensive records that show exactly what happened and when.
HIPAA audits become much more manageable when your monitoring system tracks every access to patient information. The system shows who looked at what records, when they did it, and whether they had proper authorization. This kind of detailed tracking demonstrates compliance with multiple HIPAA requirements without requiring manual documentation.
PCI-DSS assessments require you to monitor all systems that handle credit card data. Your monitoring system provides the real-time detection and comprehensive logging that assessors look for during their reviews. It’s like having your homework already done when the teacher asks to see it.
SOX compliance gets easier when monitoring systems track changes to your financial systems and maintain detailed audit trails. These records help prove that your internal controls are working effectively and that financial data hasn’t been tampered with.
The best part about using monitoring for compliance is that it’s proactive documentation. Instead of trying to recreate what happened months ago, you have real-time records that auditors can trust. This approach often shortens audit timelines and reduces the stress of compliance reviews.
At Titan Technologies, we work with businesses throughout Central New Jersey to ensure their monitoring configurations meet specific compliance requirements. We help prepare the documentation packages that make audits smoother and demonstrate your commitment to proper security controls.
Conclusion
The reality facing New Jersey businesses today is stark: cyber threats aren’t slowing down, and network security monitoring nj has become as essential as having reliable electricity or internet service. When 60% of small businesses close within six months of a cybersecurity breach, the question isn’t whether you can afford monitoring—it’s whether you can afford to operate without it.
The good news is that comprehensive monitoring solutions deliver real, measurable value that extends far beyond cybersecurity. Your business gains reduced downtime, stronger compliance posture, improved customer trust, and competitive advantages that help you win contracts in an increasingly security-conscious marketplace. The investment in proper monitoring consistently pays for itself through prevented incidents and improved operational efficiency.
The path forward depends on your organization’s specific needs and capabilities. Whether you build in-house monitoring capabilities or partner with a managed service provider, the critical factor is implementing solutions that provide 24/7 visibility and rapid response capabilities. Half-measures and delayed decisions leave your business vulnerable during the exact moments when attackers strike.
At Titan Technologies, we’ve dedicated over 15 years to helping Central New Jersey businesses steer these security challenges. Our team works with organizations throughout Edison, Elizabeth, Lakewood, Newark, Trenton, Princeton, New Brunswick, Matawan, Woodbridge, Freehold, and Red Bank to implement monitoring solutions that make sense for their operations and budget.
We start with comprehensive assessments that reveal your current security posture and identify the monitoring approaches that will provide maximum protection for your investment. Our 100% satisfaction guarantee ensures you receive the reliable, fast support your business needs to maintain operations and protect customer data.
The cost of prevention will always be less than the cost of recovery. Every day you delay implementing proper monitoring is another day your business operates without the protection it needs. Security incidents don’t wait for convenient timing—they happen when you’re least prepared.
Contact us today to schedule your network security assessment and find how comprehensive monitoring can protect your business from evolving cyber threats. Take that first step toward the peace of mind that comes from knowing your network is properly protected.
For more information about our security services, visit our Network Security page to learn how we can help safeguard your business operations and customer data.