The Rising Threat to Your Business Data
Your business data faces more threats than ever before. That’s where data protection software comes in – your digital guardian against the rising tide of cyber risks.
Think of data protection software as your business’s security blanket. It safeguards your sensitive information from theft, loss, and corruption through comprehensive backup systems, robust security measures, and reliable recovery capabilities. But what exactly does this essential tool do for your business?
At its core, data protection software shields your valuable business data through multiple layers of defense. It prevents unauthorized access while ensuring your information remains available when you need it. These solutions help you stay compliant with increasingly complex regulations like GDPR, HIPAA, and CCPA. Perhaps most importantly, modern systems automate security across your entire infrastructure – whether your data lives on-premises, in the cloud, or somewhere in between.
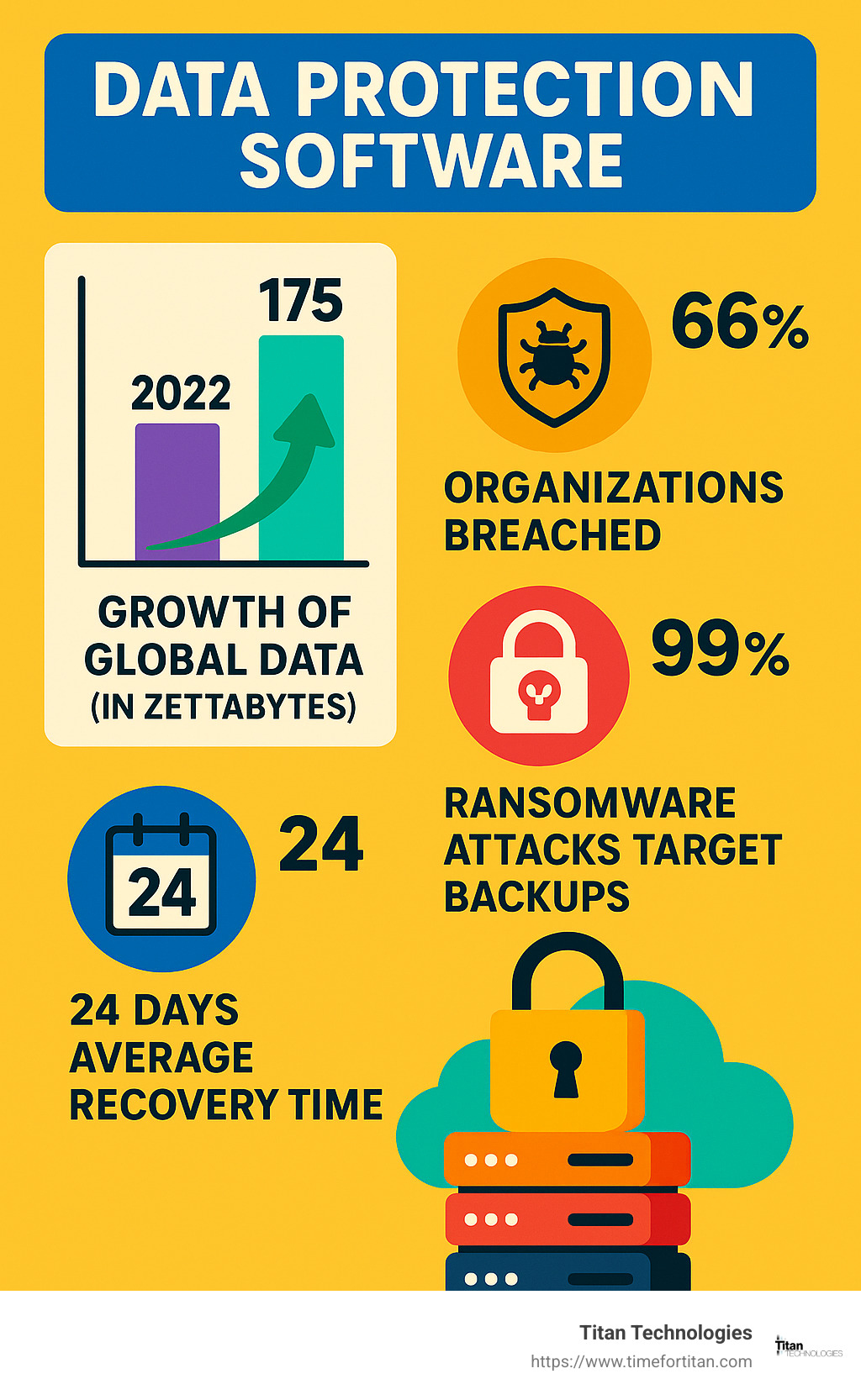
Here’s something that might keep you up at night: In 2022 alone, the world created a staggering 74 zettabytes of data. That’s 74 trillion gigabytes – more information than humans created in our entire history up until just a few years ago! By 2025, experts project this will balloon to 175 zettabytes. With this data explosion comes enormous risk. In fact, 66% of organizations experienced a breach in 2023, and a frightening 99% of ransomware attacks now specifically target backup infrastructure.
For small and medium-sized businesses here in New Jersey, the consequences of data loss can be truly devastating. Without proper protection, everything that makes your business tick – customer records, financial data, intellectual property – sits vulnerable to both malicious attacks and innocent mistakes.
As Representative Will Hurd wisely noted, “Attacks on both the public and private sectors consistently reveal one common truth – no one is immune.”
Today’s data protection software goes far beyond the simple backups of yesterday. Modern solutions bring powerful capabilities to your business, including automated backup and recovery across multiple platforms, real-time threat detection that spots problems before they spread, data loss prevention that blocks unauthorized sharing, strong encryption for your sensitive information, and compliance tools that keep you on the right side of regulations.
When disaster strikes, time is money. The average reported recovery time from a cyber attack is 24 days – that’s nearly a month of business disruption that could cripple many companies. The right data protection software can dramatically reduce this downtime, getting you back to business faster.
For Central New Jersey businesses, implementing robust data protection software isn’t just a good idea – it’s essential for survival in today’s threat landscape. The right solution provides genuine peace of mind, ensuring your critical business data remains safe, accessible, and compliant with increasingly complex regulations.
Simple guide to data protection software:
– data protection plan
– data protection governance risk management and compliance
– data protection for financial services
What Is Data Protection Software & Key Features
Think of data protection software as your digital bodyguard – it’s the technology that keeps your business information safe, intact, and recoverable when things go wrong. These solutions do far more than just back up your files; they provide comprehensive protection for your most valuable asset: your data.
At its heart, good data protection software ensures three critical things. First, it maintains your data’s integrity, making sure what you saved yesterday hasn’t been tampered with today. Second, it guarantees availability – your team can access what they need, when they need it. And third, it enables recovery, so when accidents or attacks happen (and unfortunately, they will), you can get back to business quickly.
The explosion in data we’re all experiencing is staggering. According to scientific research on data explosion, businesses are drowning in information that needs protection. This data tsunami has sparked incredible innovation in how we safeguard information.
Modern protection tools now incorporate automation that reduces the manual workload on your IT team, artificial intelligence that spots unusual patterns before they become problems, multicloud support that protects data across various cloud platforms, and hybrid capabilities that seamlessly cover both your on-site systems and cloud resources.
Want to dive deeper into comprehensive protection strategies? Check out our guide on Data Protection and Management.
Why data protection software matters
For Central New Jersey businesses, especially those in healthcare, finance, or technology, data protection software isn’t just a nice-to-have – it’s essential. Here’s why it should matter to you:
Those regulatory acronyms (GDPR, HIPAA, CCPA) aren’t just alphabet soup – they represent serious compliance requirements with teeth. Non-compliance can cost up to 4% of your global revenue under GDPR. Good protection software helps you stay on the right side of these regulations.
When your systems go down, money flies out the window. Small and medium businesses typically lose between $10,000 and $50,000 for every hour of downtime. Data protection software dramatically cuts this risk by enabling quick recovery.
Today’s ransomware attacks are frighteningly sophisticated, and they’re specifically targeting backup systems. As one of our clients put it: “When our engineers saw how quickly we could restore an entire virtual server with a few clicks, their jaws dropped.” That’s the peace of mind good protection brings.
Perhaps most importantly, protecting data builds trust. Your customers want to know their information is safe with you. Proper data protection isn’t just good practice – it’s good business.
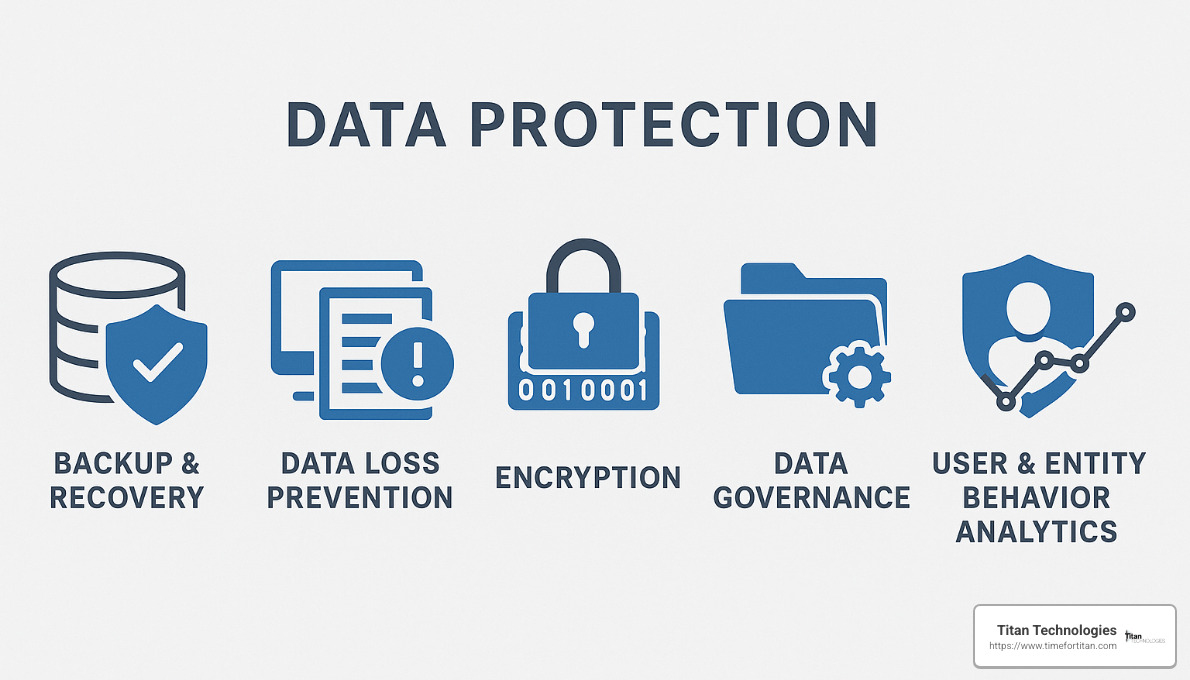
Core capabilities of modern data protection software
Today’s data protection software typically includes several interconnected capabilities that work together to shield your data:
Backup and Recovery forms the foundation of any protection strategy. Modern solutions go beyond scheduled backups with continuous data protection that captures changes as they happen, not just at night when everyone’s gone home.
Data Loss Prevention (DLP) acts like a vigilant security guard, monitoring how information moves through your organization and stopping it from walking out the door through email, cloud uploads, or USB drives.
Encryption transforms your sensitive data into unreadable code that stays that way until accessed by authorized users with the proper keys. This protects information both when it’s stored and when it’s moving across networks.
Data Governance establishes the rules of the road – how information should be classified, who can access what, and how long different types of data should be kept. Good governance automates finding and categorizing sensitive information, so nothing falls through the cracks.
User and Entity Behavior Analytics leverages AI to understand what “normal” looks like in your environment, then flags unusual activities that might indicate a breach or insider threat before major damage occurs.
Orchestration ties everything together, automating complex protection workflows across multiple systems so your team doesn’t have to manually juggle different tools.
| Capability | Primary Function | Key Benefits | Common Features |
|---|---|---|---|
| Backup & Recovery | Creates restorable copies of data | Minimizes downtime after data loss | Snapshots, replication, CDP, immutable storage |
| Data Loss Prevention | Prevents unauthorized data sharing | Reduces risk of data exfiltration | Content inspection, contextual analysis, endpoint monitoring |
| Encryption | Makes data unreadable without keys | Protects confidentiality even if access is breached | Key management, hardware security integration, certificate handling |
| Governance | Establishes data handling policies | Ensures compliance with regulations | Classification, retention policies, access controls, audit trails |
At Titan Technologies, we understand that navigating these capabilities can feel overwhelming. That’s why we work with Central New Jersey businesses to implement protection solutions that make sense for your specific needs – no complicated jargon, just straightforward protection that works.
Top 5 Categories of Data Protection Software Solutions
Navigating data protection software can feel a bit like walking through a maze. There’s no one-size-fits-all solution—instead, you’ll find a spectrum of tools designed to safeguard different aspects of your business data. Most successful organizations adopt what security experts call a “layered defense approach,” combining multiple solutions to create a comprehensive shield around their valuable information.
When considering which tools make sense for your business, think about both the immediate and long-term value they’ll provide. The ROI isn’t just about preventing costly downtime (though that’s certainly important!). It’s also about protecting your reputation and maintaining customer trust—things that are harder to assign a dollar value to, but absolutely critical to your business success.
The good news? Today’s data protection software is designed to grow with you. As your business expands, these solutions can scale accordingly, continuing to protect your data whether it lives in the cloud, on your local servers, or on employees’ devices at the edge of your network.
Let’s take a closer look at the five major categories that form the backbone of any robust data protection strategy. Each serves a distinct purpose, but they work best when implemented together as part of a coordinated approach to keeping your business data safe, available, and compliant.
Think of these categories as the essential building blocks for your data protection strategy. While you might not need every solution right away, understanding the full landscape helps you make informed decisions about where to focus your resources for maximum protection. The goal isn’t just to check a box for compliance—it’s to create genuine security and resilience for the data that powers your business.
As we explore each category in detail, consider which ones address your most pressing data protection challenges. For many of our Central New Jersey clients, starting with a solid backup and recovery platform provides the foundation, while additional layers can be added as needs evolve and budgets allow.
1. Backup & Recovery Platforms
The cornerstone of any data protection strategy, backup and recovery platforms create secondary copies of your data that can be restored in case of loss, corruption, or disaster. Modern solutions have evolved far beyond simple periodic backups to offer sophisticated capabilities that ensure business continuity.
Think of backup and recovery platforms as your business’s safety net – that critical system that catches you when things go wrong. And in today’s digital landscape, things do go wrong, often in ways we couldn’t have predicted.
Immutable copies represent one of the most powerful innovations in modern data protection software. These are backup snapshots that cannot be altered or deleted – even by administrators – for a specified retention period. This feature has become essential in the fight against ransomware, which increasingly targets backup files as part of its attack strategy. As one of our clients, an IT director at a manufacturing firm, recently told us, “Other vendors don’t come anywhere near the level of security assurance we get with immutable snapshots. It’s like having backup insurance for our backups.”
Storage efficiency matters too, especially as data volumes continue to explode. Today’s sophisticated deduplication technology identifies and eliminates redundant data blocks, dramatically shrinking your storage footprint. Some of the solutions we implement achieve deduplication ratios of 65:1 or better – meaning 65 TB of logical data can be stored in just 1 TB of physical space. This not only reduces costs but also speeds up backup and recovery operations.
The ability to create snapshot management systems gives you remarkable flexibility in recovery scenarios. These point-in-time copies allow you to “rewind” your systems to specific moments before an incident occurred. What’s particularly impressive is how modern platforms can create and manage thousands of snapshots with minimal performance impact, giving you granular recovery options without slowing down your business.
For organizations that need guaranteed business continuity, Disaster Recovery as a Service (DRaaS) offers cloud-based recovery solutions that enable rapid restoration after major disruptions. We’ve seen these services reduce downtime by up to 75% compared to traditional recovery methods – the difference between being down for days versus just hours.
For businesses across Edison, Elizabeth, Lakewood, and throughout Central New Jersey, we implement backup and recovery solutions custom to your specific industry requirements and recovery time objectives. Our approach creates multiple layers of protection while ensuring you can get back up and running quickly when disaster strikes.
Want to learn more about how cloud technologies are changing data protection? Visit our guide on Data Protection Cloud-Based Services for a deeper dive into these innovative solutions.
2. Data Loss Prevention (DLP) Suites – a pillar of data protection software
Think of Data Loss Prevention as your digital security guard, constantly watching over your sensitive information to make sure it doesn’t wander where it shouldn’t. While backup solutions help you recover after something goes wrong, DLP works on the prevention side – stopping data leaks before they happen.
“I used to lose sleep worrying about employee mistakes leading to data breaches,” a client from New Brunswick told us recently. “Now our DLP system catches those potential issues before they become problems.”
Data protection software with strong DLP capabilities gives you eyes on your information no matter where it travels. This has become especially crucial with remote work blurring the lines between personal and business devices.
What makes DLP so effective?
Endpoint monitoring watches activity on all your company devices – from office desktops to employees’ laptops and phones. When Sarah in accounting tries to email a spreadsheet with customer credit card numbers to her personal Gmail, the DLP system can stop that transfer instantly and notify your IT team.
The best systems use content filtering and classification that’s smart enough to recognize sensitive information automatically. Rather than just blocking certain file types, modern DLP can identify a Social Security number hiding in a Word document or credit card details embedded in an image.
A manufacturing client in Woodbridge summed it up perfectly: “The process of setting up and using DLP was shockingly simple. Once the installation and setup is done, there is not much to do except check email alerts to make sure the policies are working correctly.”
Concerned about old-school data theft? USB and peripheral control features let you manage who can use removable storage devices. You can block them entirely, allow only company-issued encrypted drives, or create custom policies based on department or role. This prevents the classic “download to thumb drive and walk out the door” scenario that still accounts for a surprising number of data breaches.
Perhaps most valuable in today’s complex threat landscape is insider threat protection. These sophisticated tools establish baselines of normal behavior for each user, then flag unusual activities that might indicate a security problem. As one security professional told us, “We went from about 200 to 300 alerts a day down to 15 to 30 after implementing contextual DLP that understands user behavior patterns.”
For our clients in Newark, Trenton, and Princeton, we typically start DLP implementations with a findy phase. This helps us understand how data moves through your organization before we develop and gradually implement policies that protect your information without disrupting your workflow.
The right DLP solution becomes an invisible guardian – working quietly in the background until the moment it needs to step in and prevent a potential data disaster. When paired with other elements of comprehensive data protection software, it creates a security shield that both prevents incidents and enables rapid recovery when necessary.
3. Encryption & Tokenization Engines
Encryption and tokenization serve as your data’s last line of defense—like an invisible shield that protects your information even when other security measures fail. These powerful technologies transform your sensitive data into coded formats that remain secure even if unauthorized access occurs.
At-Rest Encryption keeps your data safe while it’s stored in databases, file systems, and cloud storage. Using robust algorithms like AES-256 (the same military-grade protection used for classified information), this technology ensures that even if someone physically steals your storage devices, they can’t read what’s on them without the proper keys.
“Using encryption proved to be a real advantage because it offers a really powerful and simple process to restore in case of damage or a ransomware attack, while maintaining HIPAA compliance throughout,” shared one of our healthcare clients who implemented data protection software with strong encryption capabilities.
In-Transit TLS Protection works like a secure tunnel for your data as it travels across networks. This Transport Layer Security protocol prevents anyone from “listening in” on your data transfers—whether it’s customer information moving between your website and payment processor or sensitive files being shared between colleagues.
Behind any good encryption system is sophisticated Key Management. Think of encryption keys as the special codes that lock and open up your data. If these keys are lost, your encrypted data becomes permanently inaccessible (like losing the only key to a safe), but if they’re stolen, your encryption can be defeated. Our solutions implement robust systems for generating, storing, rotating, and protecting these critical keys.
Modern data protection software also incorporates Zero Trust Architecture—an approach that follows the principle of “never trust, always verify.” This means every access attempt requires authentication and authorization, regardless of whether it comes from inside or outside your network. It’s like having a security guard who checks ID badges at every door in your building, not just at the main entrance.
For our financial services clients in New Brunswick and healthcare providers in Freehold, we carefully balance robust security with usability. After all, the strongest encryption in the world isn’t helpful if it makes your systems too cumbersome to use. Our encryption implementations protect your sensitive data while maintaining application performance and keeping your team productive.
When properly implemented, encryption and tokenization create a powerful security layer that complements your other data protection software components. Even if a breach occurs, your most sensitive information remains scrambled and useless to attackers—giving you peace of mind that your critical business data stays private and secure.
4. Governance, Risk & Compliance Automation Tools
Keeping up with today’s ever-expanding regulatory requirements can feel like trying to hit a moving target. That’s where Governance, Risk, and Compliance (GRC) automation tools come in as vital components of your data protection software strategy. These solutions help you steer the complex compliance maze while showing regulators you’re doing your homework.
Think of GRC tools as your compliance co-pilot, automatically documenting your journey through regulations like GDPR, HIPAA, and CCPA. According to a recent report on compliance drivers, two-thirds of security professionals point to compliance mandates as what’s driving their security spending—and for good reason.
“Before automation, our quarterly compliance reviews took three weeks of full-time work from two team members,” shared one of our clients in Red Bank. “Now we generate comprehensive reports in just a few hours.”
The magic happens through several key capabilities. Regulatory framework mapping automatically connects your existing security controls to specific requirements across different regulations. No more spreadsheet nightmares trying to track which controls satisfy which requirements!
Audit trails and evidence collection work like a diligent record-keeper, documenting everything from who accessed what data to how you responded to security incidents. When auditors come knocking (and they will), you’ll have everything they need at your fingertips.
Many of our Matawan clients love the workflow automation features that turn manual compliance tasks into streamlined processes. Tasks like getting employees to sign off on updated policies or conducting regular risk assessments happen automatically, often cutting compliance preparation time by up to five weeks.
The centerpiece of these systems is usually robust policy management and enforcement capabilities. Rather than having policies scattered across shared drives and email inboxes, everything lives in one central location where you can easily update, distribute, and track adherence across your organization.
One TrustArc customer reported not just an 80% decrease in privacy incidents after implementing these tools, but also saved over $650,000 in compliance costs. For small and medium businesses in Central New Jersey, those kinds of savings can make a real difference to your bottom line.
For our healthcare clients in Freehold, automating HIPAA compliance has transformed what was once a dreaded annual ordeal into a continuous, much less painful process. The same goes for our financial services clients dealing with regulations like SOX and GLBA.
Want to dive deeper into how governance, risk management, and compliance approaches can work for your business? Check out our detailed guide on Data Protection Governance, Risk Management, and Compliance.
At Titan Technologies, we specialize in creating compliance programs that don’t just reduce risk, but also cut down on the administrative headaches. After all, you should be spending your time growing your business, not buried in compliance paperwork.
5. AI-Driven Cyber Resilience Solutions – the future of data protection software
The newest and most exciting frontier in data protection software harnesses the power of artificial intelligence to create true cyber resilience. This isn’t just about protecting your data – it’s about building systems that can anticipate attacks, withstand them when they occur, recover quickly, and adapt to prevent future incidents.
These intelligent solutions represent where data protection is heading – moving away from static, reactive defenses toward smart systems that learn and evolve alongside emerging threats.
Behavior Analytics has transformed how we detect potential breaches. Rather than just looking for known malware signatures, AI establishes what “normal” looks like for your users and systems, then flags unusual activity that might indicate something’s wrong.
“We were drowning in alerts before implementing AI analysis,” one IT director told us. “We went from sifting through 200-300 alerts daily to just 15-30 meaningful ones that actually require attention. It’s like having a security expert who never sleeps.”
Ransomware Rollback capabilities have become game-changers for businesses facing the growing ransomware threat. When traditional defenses fail, these advanced systems can identify ransomware activity in its early stages and automatically restore affected systems to their pre-attack state. While the industry average recovery time hovers around 24 days, organizations with AI-driven protection often restore operations in mere hours – sometimes even minutes.
Automated Remediation takes protection a step further. When threats are detected, these intelligent systems don’t just send alerts – they take immediate action based on predefined security playbooks. This dramatically reduces response time and eliminates human error during those critical first moments of an incident.
Multicloud Protection addresses one of today’s biggest challenges – protecting data that lives across multiple cloud environments. With workloads and data scattered across AWS, Azure, Google Cloud, and private infrastructure, unified protection is essential. Dell’s cloud protection solutions, for example, deliver this unified approach while being 80% more cost-effective than many competing options.
For businesses throughout Central New Jersey – from small retailers in Elizabeth to healthcare providers in Lakewood – we implement custom AI-driven resilience solutions that match your specific industry requirements and threat landscape. These aren’t one-size-fits-all tools, but customized protections that grow with your business.
The real value of these advanced solutions isn’t just in preventing attacks – it’s the confidence they provide. Knowing your business can continue operating even when facing sophisticated threats gives you the freedom to focus on growth rather than constantly worrying about the next cyber incident.
How to Choose & Implement Data Protection Software
Selecting the right data protection software isn’t just about checking boxes on a feature list—it’s about finding a solution that truly fits your business like a comfortable glove. At Titan Technologies, we’ve guided countless Central New Jersey businesses through this process, and we’ve learned that success starts with understanding what makes your data environment unique.
The journey begins with a thorough risk assessment. Think of this as creating a map of your digital landscape—identifying your crown jewels (your most valuable data), understanding who might want to steal them, and spotting the weak points in your defenses. This assessment becomes your compass for the entire selection process.
When evaluating potential solutions, several factors should guide your decision:
Scalability matters tremendously. The software that perfectly handles your current 2TB of data might buckle under the weight of 20TB next year. Look for solutions with room to grow alongside your business without performance hiccups.
Total Cost of Ownership (TCO) goes far beyond the initial price tag. Consider the ongoing costs—storage requirements, annual maintenance fees, training needs, and administrative time. Some solutions with higher upfront costs actually prove more economical over a three-year horizon.
“We initially went with the cheaper option,” shared one of our clients in Edison, “but ended up spending twice as much on storage and overtime hours for our IT team. Sometimes you truly get what you pay for.”
Integration Capabilities determine how smoothly your new protection software will play with your existing systems. The best solution in the world becomes a headache if it doesn’t communicate properly with your critical applications or cloud services.
Usability might seem secondary until you realize it directly impacts adoption. When protection tools are overly complex, people find workarounds—creating security gaps. Intuitive interfaces and streamlined workflows encourage proper use.
Support Quality becomes invaluable when problems arise (and they will). Investigate the vendor’s support options: Do they offer 24/7 assistance? What’s their average response time? Can you speak directly with technical experts or will you face endless phone trees?
Key selection criteria
When narrowing down your data protection software options, focus on these critical selection criteria:
Recovery Service Level Agreements (SLAs) should align with your business needs. If your operation can only tolerate 15 minutes of downtime, a solution with a four-hour recovery window simply won’t cut it. Be honest about your Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO)—how quickly you need to be back online and how much data you can afford to lose.
Regulatory Fit ensures your solution addresses your specific compliance requirements. A manufacturing company in Perth Amboy has different needs than a medical practice in Princeton. Healthcare providers need solutions that satisfy both HIPAA and the New Jersey Identity Theft Prevention Act, while financial services firms must address SEC and FINRA requirements.
Automation Level directly impacts both security and efficiency. More automated solutions reduce human error and free up your team for strategic work. Look for policy-based automation that handles routine tasks while maintaining appropriate human oversight for exceptions.
Reporting Depth provides the visibility needed for both operations and compliance. Your solution should generate reports that satisfy auditors while also giving IT teams actionable insights. Reports should be customizable and accessible to various stakeholders—from technically detailed logs for your IT team to executive summaries for leadership.
Deployment best practices
Even the perfect data protection software can fail if implemented poorly. Follow these field-tested best practices to ensure success:
Pilot Testing creates a safe space to identify issues before they impact your entire organization. Start with a small, controlled environment—perhaps a single department or non-critical system. This approach reveals integration challenges, performance impacts, and workflow disruptions while they’re still manageable.
“Our pilot with the accounting department saved us enormous headaches,” recalled a client in Newark. “We finded conflicts with their tax software that would have caused major problems during tax season if we’d done a company-wide rollout.”
Phased Rollout builds on the pilot’s success by implementing the solution in stages. Start with less critical systems, learn from each phase, and apply those lessons as you progress to more sensitive environments. This approach minimizes business disruption and builds confidence among both IT staff and users.
Policy Tuning requires patience but pays dividends in reduced false positives. Begin with policies in monitoring-only mode to establish baselines of normal behavior. Analyze the alerts generated during this period to refine rules before switching to enforcement mode. This prevents the “boy who cried wolf” syndrome where excessive alerts lead to alert fatigue.
Staff Training ensures everyone understands their role in data protection. Technical staff need comprehensive training on administration and troubleshooting, while end users need awareness of their responsibilities and processes for requesting exceptions when necessary. Protection tools are only as effective as the people using them.
For businesses throughout Central New Jersey—from Edison to Lakewood, Newark to Trenton—we provide white-glove implementation services that follow these best practices while addressing your specific business requirements. Our team brings experience across multiple industries, helping you avoid common pitfalls and accelerate time-to-protection.
For more information about developing a comprehensive data protection strategy, visit our guide on Data Protection Plan.
Frequently Asked Questions about Data Protection Software
What’s the difference between data protection software and data security tools?
I often get this question from clients who are trying to sort through the maze of IT security options. While they’re close cousins, data protection software and data security tools actually serve different primary purposes.
Think of data protection software as your safety net. It focuses on making sure your data remains available, maintains its integrity, and can be recovered when things go wrong. The bread and butter of data protection includes backup systems, business continuity solutions, and tools that help you stay compliant with regulations. Essentially, it’s there to ensure you can access your critical data even after something bad happens.
Data security tools, on the other hand, are more like your front-line defenders. They’re designed to prevent unauthorized access and keep your data confidential. This category includes familiar technologies like firewalls, intrusion detection systems, and anti-malware solutions that work to stop security incidents before they happen.
As one of our security professionals explained to a client recently, “Data security without recovery capabilities leaves you vulnerable to ransomware, while backup without security controls creates an open door for attackers.”
That’s why at Titan Technologies, we don’t see this as an either/or situation. We implement integrated solutions that address both protection and security needs, creating multiple layers of defense for your valuable business information.
How does data protection software help with GDPR, HIPAA, or CCPA compliance?
Navigating today’s complex regulatory landscape can feel overwhelming. The good news is that data protection software can be your compliance ally, helping satisfy key requirements across different regulations.
For GDPR compliance, good data protection software helps you find and classify personal data that falls under GDPR’s scope. It provides access controls and encryption to ensure appropriate protection, creates audit trails documenting your data processing activities, and gives you tools to fulfill data subject rights requests like access, deletion, and portability.
When it comes to HIPAA compliance, the right solutions encrypt Protected Health Information both at rest and in transit, limit PHI access to authorized personnel only, log all access attempts for future auditing, and provide secure backup and disaster recovery to maintain availability.
For businesses dealing with CCPA/CPRA requirements, data protection software helps create inventories of consumer personal information, establishes processes for responding to consumer requests within required timeframes, documents data sharing with third parties, and prevents the sale of personal information when consumers opt out.
I remember a conversation with a financial services client in Princeton who told me: “TrustArc’s automation helped us achieve a 35% decrease in the total cost of proving compliance and reduced our time to compliance by five weeks.”
For New Jersey businesses facing multiple regulatory requirements, we create compliance-focused implementations that satisfy overlapping obligations without duplicating effort – saving you time, money, and headaches.
Can automation and AI really shorten recovery after a ransomware attack?
Absolutely! This isn’t just marketing hype – automation and AI are game-changers when it comes to ransomware recovery. Let me explain how they make such a dramatic difference.
First, there’s detection speed. AI-based systems can spot ransomware behavior patterns before encryption completes, often limiting the attack’s scope. Traditional signature-based detection frequently misses new variants until significant damage is already done.
Then comes automated isolation. When ransomware is detected, these smart systems can immediately quarantine affected systems to prevent lateral movement – often without waiting for a human to make the call.
Recovery prioritization is another area where AI shines. The technology analyzes business dependencies to restore your most critical systems first, optimizing the entire recovery process. And before systems go back into production, automated validation checks ensure the restored data is clean and uncompromised, preventing reinfection.
I’ll never forget what one customer told us after we helped them recover from a ransomware attack: “I never saw the support team admit defeat. I witnessed their determination to work the problem with my team until it was resolved. It was a miracle to have all our systems and data back so quickly.”
The numbers back this up too. Dell reports up to 75% reduction in downtime with PowerProtect Cyber Recovery compared to traditional approaches. When you consider that the industry average recovery time is 24 days, having a well-automated recovery measured in hours can literally be the difference between your business surviving or failing.
For organizations throughout Central New Jersey – from Trenton to New Brunswick and beyond – we implement AI-improved recovery solutions that minimize both downtime and data loss when ransomware strikes.
Conclusion
In today’s data-driven business environment, robust data protection software isn’t just an IT concern—it’s a business imperative. The exponential growth of data, increasing regulatory requirements, and evolving threat landscape make comprehensive protection essential for organizations of all sizes.
The truth is, your business data faces more threats today than ever before. From sophisticated ransomware attacks to accidental deletion, the risks are real and growing. But with the right protection strategy, you can safeguard your most valuable digital assets while maintaining compliance and business continuity.
As we’ve explored throughout this article, effective data protection requires a multi-layered approach. Think of it as building a fortress around your data—each layer adding another level of security. This fortress combines backup systems that preserve your information, prevention tools that control how data moves, encryption that makes sensitive information unreadable to unauthorized users, governance frameworks that ensure compliance, and AI-powered solutions that adapt to emerging threats.
For businesses in Central New Jersey, from the busy offices of Edison to the historic streets of Red Bank, from Elizabeth’s industrial parks to Princeton’s innovation centers, Titan Technologies provides custom data protection solutions custom to your specific needs. We understand that a healthcare provider in Freehold has different requirements than a financial services firm in New Brunswick, and we design our solutions accordingly.
Our professional team doesn’t just implement technology—we build relationships based on trust and reliability. When your systems are down or your data is at risk, you need a partner who responds quickly and resolves issues completely. That’s why we back our services with a 100% satisfaction guarantee. As one client put it:
“It is a comfort knowing that preventive IT solutions are always working behind the scene.” – Vernon Ralph, CEO
We’ve seen how proper data protection software has saved businesses from disaster. Like the manufacturing company in Woodbridge that recovered from a ransomware attack in hours rather than weeks. Or the healthcare provider in Matawan that maintained HIPAA compliance even during a system migration. These success stories share a common thread—preparation and the right protection tools.
Whether you’re worried about the next ransomware variant, struggling to meet new regulatory requirements, or simply ensuring your business can continue operating after an unexpected event, we have the expertise and solutions to help. Our approach balances robust security with usability and cost-effectiveness, ensuring that protection improves rather than hinders your business operations.
Ready to strengthen your data protection strategy? Contact Titan Technologies today to schedule a comprehensive assessment of your current protection measures and identify opportunities for improvement. Our team is ready to help you implement the right data protection software for your specific needs.
For more information about our comprehensive range of IT services and solutions, visit our services page.