The Digital Shield: Protecting NJ Businesses from Cyber Threats
Network security nj is essential for businesses across the Garden State looking to protect their sensitive data and digital infrastructure from growing cyber threats. If you’re searching for information about network security in New Jersey, here’s what you need to know:
| Network Security in NJ: Quick Facts |
|---|
| • 1 in 5 NJ organizations will experience a cyber breach in 2025 |
| • 81% of all breaches target small and medium-sized businesses |
| • 97% of these breaches are preventable with current technology |
| • Key protection includes firewalls, employee training, and managed security services |
| • The NJ Cybersecurity & Communications Integration Cell (NJCCIC) provides state-specific resources |
In today’s interconnected business landscape, your company’s network is like a digital garden that requires constant protection from invasive threats. As cybercriminals become increasingly sophisticated, businesses throughout New Jersey face growing risks of data breaches, ransomware attacks, and other malicious activities.
“If you have a broadband-ISP your network has open doors to the Internet. Just as you would not want to leave the door to your home or business wide open, you shouldn’t leave your door to the Internet open,” notes a leading NJ security provider.
For small and medium-sized businesses in central New Jersey, the stakes are particularly high. Limited IT resources often make these organizations prime targets for cyber attackers looking for vulnerable entry points. The good news? With the right security framework in place, nearly all these attacks are preventable.
Network security isn’t just about installing antivirus software or setting up a basic firewall. It requires a comprehensive, multi-layered approach that addresses hardware, software, and the human element. For New Jersey businesses, this means implementing solutions that not only protect digital assets but also ensure compliance with state and federal regulations.
Understanding Cyber Threats in New Jersey
The digital landscape across the Garden State is under constant siege, with cyber threats evolving at an alarming pace. For New Jersey businesses, understanding these threats isn’t just about IT knowledge—it’s about survival in today’s digital economy.
Common Cyber Threats Targeting NJ Businesses
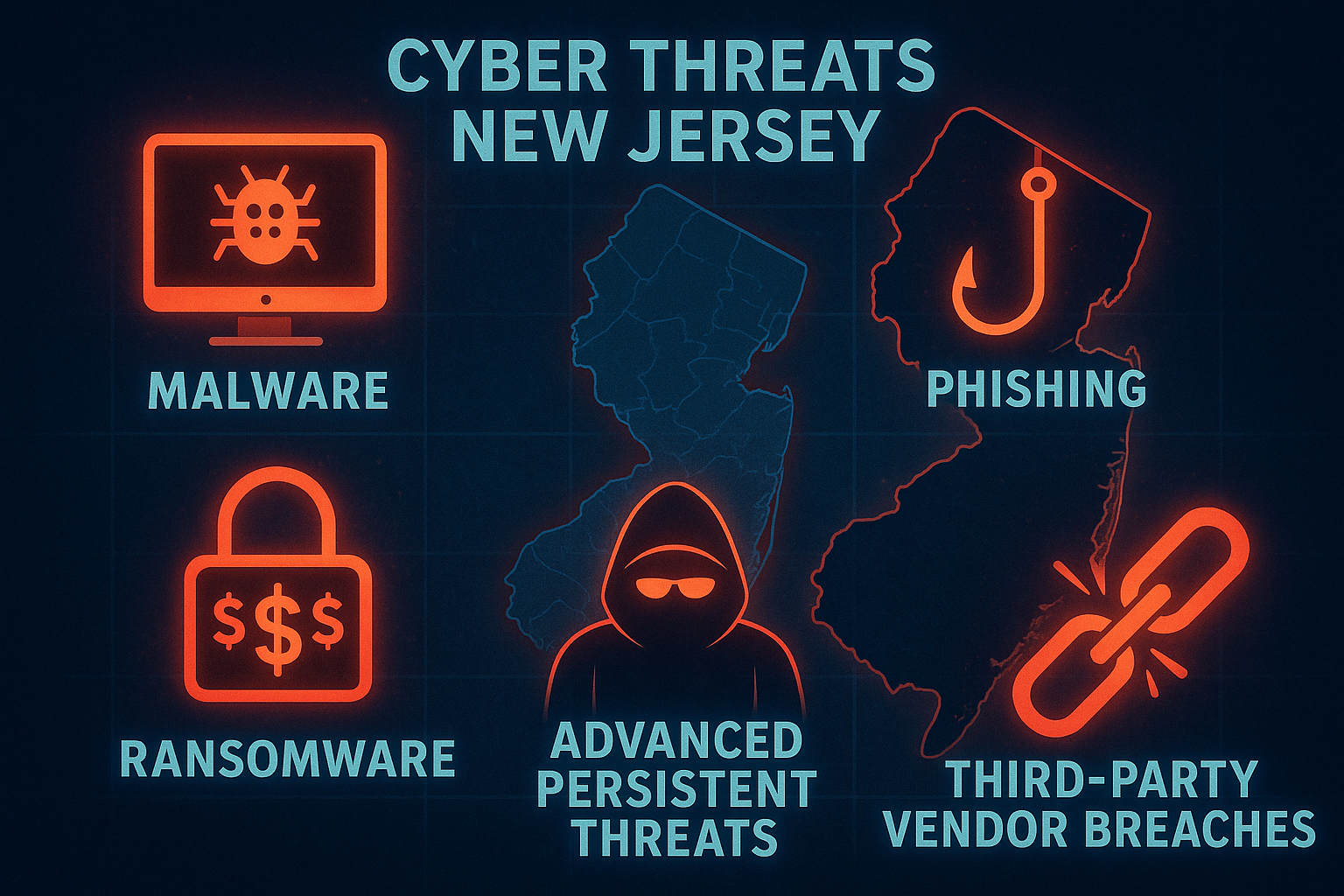
When we look at what’s happening in New Jersey’s cybersecurity landscape in 2025, certain threats stand out as particularly concerning. Malware infections continue to plague businesses of all sizes, with the New Jersey Cybersecurity & Communications Integration Cell (NJCCIC) recently tracking sophisticated campaigns distributing LokiBot through seemingly innocent email attachments. These aren’t your garden-variety viruses from the early 2000s—they’re advanced tools designed to steal sensitive information while remaining undetected.
Phishing attacks have become increasingly convincing, with many New Jersey businesses reporting emails that perfectly mimic legitimate communications from government agencies, banks, or even colleagues. One Bergen County manufacturing firm nearly transferred $50,000 to criminals after receiving what appeared to be an invoice from a longtime supplier—only a last-minute verification call prevented the loss.
Perhaps most frightening is the rise of ransomware across our state. Several New Jersey municipalities have found themselves locked out of critical systems, facing demands that sometimes reach six figures. A Morris County healthcare provider was forced to revert to paper records for nearly two weeks after an attack—creating risks that extended beyond data to actual patient care.
The Latest threats reported by New Jersey Cybersecurity & Communications Integration Cell show a concerning trend toward Advanced Persistent Threats targeting New Jersey’s economic pillars—our pharmaceutical companies, financial institutions, and healthcare organizations. These aren’t smash-and-grab operations but calculated campaigns designed to maintain long-term access to valuable data.
Even more troubling is the growth in third-party vendor breaches. The 2025 CDK Global cyberattack demonstrated how vulnerabilities in one company can cascade through an entire business ecosystem. As one NJCCIC analyst put it, “Your security is only as strong as your weakest connected partner.”
The Impact on NJ Businesses
When cyber attacks hit New Jersey companies, the effects ripple through every aspect of the business. The financial losses extend far beyond any ransom payments—system recovery costs, lost productivity during downtime, and potential legal liabilities can easily run into hundreds of thousands of dollars, even for small businesses.
The operational disruption can be devastating. A Monmouth County retail chain lost access to inventory systems for three days during their busiest season, resulting in confused staff, frustrated customers, and significant revenue loss.
Perhaps most lasting is the reputational damage. As one IT manager from a central New Jersey Internet Service Provider candidly shared after experiencing a breach: “We had to isolate infected systems, implement a remediation strategy to secure our website, and create new protocols to protect our data from future cybersecurity breaches. The experience taught us that no business is too small to be targeted—but worse, it taught us how quickly customers lose trust.”
For businesses subject to industry regulations, regulatory penalties add another layer of pain. Under New Jersey’s data breach notification law and various federal regulations, companies face significant fines for failing to properly protect customer information.
The threats facing network security NJ businesses are substantial, but understanding them is the first step toward creating effective defenses. With proper preparation and the right security partner, New Jersey companies can steer this challenging landscape without becoming another statistic in 2025’s breach reports.
Why Network Security is Essential for NJ Businesses
Let’s face it – running a business in the Garden State is challenging enough without having to worry about cyber criminals targeting your digital assets. Yet for companies across New Jersey, from small family businesses to growing enterprises, network security has become as essential as locking your front door at night.
Financial Protection
When a cyber attack hits, your bottom line takes the first and hardest hit. For small and medium-sized businesses throughout New Jersey, these costs can be crippling. We’re talking thousands of dollars per month in lost revenue while systems are down, expensive recovery efforts, and potentially legal fees if customer data was compromised.
Think about businesses in busy areas like Newark, Princeton, or New Brunswick. In these competitive markets, customers won’t wait around while you recover from a breach – they’ll simply move on to your competitors.
One healthcare company CFO in New Jersey learned this lesson the hard way after experiencing a ransomware attack: “Intellikor helped us remediate and rebuild after a ransomware attack, and created a list of priorities to fix weaknesses they found in our technology. Their guidance will protect us from similar attacks in the future.”
Data Protection Obligations
Your business collects valuable data every day – customer information, financial records, proprietary business knowledge. Protecting this information isn’t just good business sense – it’s often legally required.
This is especially true in industries that dominate New Jersey’s economy: healthcare, pharmaceuticals, and financial services. These sectors face strict regulations about data security, with hefty penalties for non-compliance that go far beyond the immediate costs of a breach.
Network security NJ solutions help ensure you’re not just protecting your data, but also staying on the right side of increasingly complex data protection laws.
Maintaining Business Continuity
Remember when that storm knocked out power across central Jersey a few years back? Businesses without generators or backup plans suffered greatly. Cyber attacks work the same way – except they can happen on perfectly sunny days without warning.
For businesses from Edison to Trenton and Elizabeth to Lakewood, staying operational is non-negotiable. Proper network security NJ measures ensure your systems remain up and running even when faced with cyber threats. With robust backup systems and disaster recovery protocols in place, you can minimize downtime and keep serving your customers no matter what digital storms come your way.
Preserving Reputation and Trust
New Jersey businesses operate in one of America’s most competitive marketplaces. When word gets out that your company experienced a security breach, that reputation you’ve spent years building can crumble overnight.
Customer trust is fragile – especially when it comes to handling their sensitive information. As one New Jersey media company CEO shared after improving their security: “Intellikor was amazing. They managed to secure all our servers and improved our security posture.” That investment in security directly translated to preserved trust and business confidence.
“81% of all breaches happen to small and medium-sized organizations.”
This sobering statistic highlights why network security NJ is particularly crucial for smaller businesses that form the backbone of New Jersey’s economy. Without the extensive IT departments and security budgets of larger corporations, these businesses must be especially strategic and vigilant in their security approaches.
The good news? With the right partner helping manage your network security, even small businesses can implement enterprise-grade protection without breaking the bank. In today’s digital landscape, robust network security isn’t just a technical necessity – it’s a fundamental business investment that protects everything you’ve worked to build.
Key Components of a Comprehensive Network Security Strategy
When it comes to protecting your business in today’s digital landscape, a single security solution just won’t cut it. At Titan Technologies, we’ve learned through years of helping New Jersey businesses that effective protection requires a multi-layered approach – think of it as building a fortress with multiple walls rather than just a single fence.
Firewalls: Your First Line of Defense
Think of firewalls as the security guards at your network’s entrance. For network security nj implementations that truly work, we typically recommend robust hardware firewalls rather than just software solutions. These physical devices create a stronger barrier between your sensitive data and the wild west of the internet.
Today’s modern firewalls do much more than their predecessors. They inspect incoming and outgoing traffic deeply, prevent intrusions before they happen, filter applications that might pose risks, and support secure VPN connections for your remote workers. For businesses across New Jersey, this first line of defense is absolutely critical – especially as remote work becomes more common.
Intrusion Detection and Prevention Systems
Even with great guards at the door, you still need security cameras and alarms throughout your building. That’s essentially what intrusion detection systems (IDS) and intrusion prevention systems (IPS) provide for your network. These systems are constantly watching for suspicious activities that might indicate someone has slipped past your initial defenses.
For network security nj solutions to be truly effective, these systems need to monitor traffic patterns continuously, alert your team when something doesn’t look right, automatically block suspicious activities, and keep detailed records of everything that happens. This vigilance has saved many of our New Jersey clients from what could have been devastating breaches.
Comprehensive Antivirus and Anti-malware Protection
Malware continues to be one of the most persistent threats facing businesses throughout New Jersey. Effective protection means having strong antivirus and anti-malware solutions deployed across all devices, with regular scanning that happens automatically. The best solutions provide real-time protection, central management so nothing falls through the cracks, and cloud-based updates that keep your defenses current against new threats.
Data Encryption
If sensitive data is the crown jewels of your business, encryption is the unbreakable vault that protects them. Encryption transforms your readable information into coded text that’s meaningless without the proper key. For network security nj strategies to be complete, encryption needs to protect data sitting on your servers (at rest), data moving across networks (in transit), sensitive email communications, and any remote connections to your systems.
Secure Backup Solutions
Even with the best defenses, having a solid backup plan is essential – it’s your safety net if the worst happens. New Jersey businesses need backup strategies that include regular automated copies of critical data, storage both onsite and offsite, proper encryption of those backup files, and regular testing to make sure restoration actually works when needed. We’ve seen too many businesses learn the hard way that untested backups sometimes fail when they’re needed most.
Network Segmentation
Dividing your network into separate sections is like having fireproof doors throughout a building – if one area catches fire, the whole place doesn’t burn down. This approach contains potential breaches to limited areas of your network, keeping your most sensitive data isolated from general access. It also improves overall performance by reducing network congestion and simplifies compliance requirements by separating regulated data.
Mobile Device Security
With so many employees now working remotely across New Jersey, from Newark to Princeton and beyond, mobile device security has become absolutely essential. Effective mobile security includes management solutions that enforce your policies, secure access to company resources, the ability to remotely wipe lost or stolen devices, and security measures that work even on personal devices that employees use for work.
Regular Software Updates and Patch Management
Outdated software is like having a door with a broken lock – it’s an invitation to intruders. A systematic approach to updates is essential, including automation where possible, regular schedules for critical systems, testing before widespread deployment, and constant monitoring for new vulnerabilities. Many of the worst breaches we’ve seen could have been prevented with timely updates.
More info about Network Security Management
The Role of Firewalls in Network Security NJ
Firewalls deserve special attention because they truly are the foundation of your security strategy. As one of our security experts often tells clients, “A hardware-based firewall is the strongest single defense against cyber threats.”
Types of Firewalls for NJ Businesses
Different businesses need different levels of firewall protection. Basic packet-filtering firewalls examine data packets and block those that don’t meet security criteria. Stateful inspection firewalls are smarter – they track active connections and make decisions based on context. Next-Generation Firewalls (NGFW) combine traditional capabilities with additional features like intrusion prevention and threat intelligence. For the most comprehensive protection, Unified Threat Management (UTM) solutions combine firewall capabilities with antivirus, content filtering, and data loss prevention.
For many businesses in tech-forward areas like Princeton and New Brunswick, Next-Generation Firewalls offer the ideal balance of robust protection without slowing down operations.
Effective Firewall Implementation
Installing a firewall is just the beginning. For optimal network security nj protection, we help businesses configure their firewalls according to the principle of least privilege – allowing only what’s absolutely necessary. We also establish regular reviews of firewall rules, monitor logs for anything suspicious, test configurations periodically, and ensure redundancy for critical systems. This comprehensive approach has protected countless New Jersey businesses from potential breaches.
Employee Training: The Human Element in Network Security NJ
All the technology in the world can’t protect you if someone holds the door open for the bad guys. The human element remains both the greatest vulnerability and potential strength in any network security nj strategy. Even a single employee clicking a malicious link or using a weak password can compromise otherwise strong security systems.
The Importance of Security Awareness Training
Good security awareness training helps your team recognize phishing attempts before they click, understand why strong passwords matter, develop safe browsing habits, handle sensitive information properly, and know exactly what to do if they spot something suspicious.
One operations manager at a financial firm in central New Jersey told us: “I’ve worked with [security experts] for several years now. I feel secure knowing they are always working behind the scenes to ensure our data is secure.” That peace of mind comes from knowing everyone on the team is part of the security solution.
Reducing Human Error Through Best Practices
Human error is inevitable, but it can be minimized with the right approach. We’ve found the most successful New Jersey businesses implement regular training that evolves as threats change, test employees with simulated phishing attempts, establish clear security policies that everyone understands, create a culture where reporting suspicious activity is encouraged rather than punished, and implement multi-factor authentication to provide an extra layer of protection beyond passwords.
Our experience at Titan Technologies has shown repeatedly that organizations investing in employee training experience significantly fewer security incidents. Our training programs are custom to the specific needs of businesses throughout central New Jersey, ensuring employees understand both general security principles and the unique threats facing their industry.
More info about Network Security
Network Security Assessments: Identifying Vulnerabilities
Before implementing security measures, understand where your vulnerabilities lie. Network security assessments provide a comprehensive view of your current security posture and identify areas that need improvement.
Types of Security Assessments for NJ Businesses
Vulnerability Scanning
Think of vulnerability scanning as a health checkup for your network. Using specialized tools, we can identify known security weaknesses in your systems and software. For network security nj implementations, these regular scans are invaluable.
When we perform vulnerability scanning for our New Jersey clients, we’re looking for unpatched systems and outdated software that hackers love to exploit. These scans also catch misconfigurations—those small setup errors that can create big security holes.
“Many of our clients are surprised by what we find,” says one of our security specialists. “That forgotten server in the closet or the old printer that no one updated can be the entry point attackers use to compromise your entire network.”
The scan results give you a clear baseline for measuring your security improvements over time and help prioritize what needs fixing first based on risk levels. Most importantly, they catch problems before hackers do.
Penetration Testing
While vulnerability scanning spots potential weaknesses, penetration testing takes security assessment to the next level by actively attempting to exploit those vulnerabilities. It’s like hiring friendly hackers to break into your systems before the malicious ones can.
Our professional penetration testers simulate real-world attack scenarios against your network, using the same techniques actual hackers would use. This hands-on approach reveals not just isolated vulnerabilities but entire attack pathways that might otherwise go unnoticed.
One IT director from a Middlesex County manufacturing firm told us: “Penetration testing revealed vulnerabilities we had no idea existed, even though we thought our systems were secure. The detailed report showed exactly how attackers could move through our network once they gained initial access.”
After testing, you’ll receive actionable recommendations that truly improve your security posture—not just theoretical advice.
Risk Assessments
Risk assessments take a wider view than purely technical scans. They examine not just your technology but also your processes, policies, and the potential business impact of various security scenarios.
For New Jersey businesses, especially those in regulated industries like healthcare or finance, risk assessments begin with identifying your most critical assets and data. We then analyze potential threats to those assets and evaluate how likely those threats are to materialize.
We’ll examine your existing security controls to determine if they adequately protect your most valuable resources. Most importantly, we’ll assess the potential business impact—what a breach would actually cost your organization in terms of downtime, reputation damage, and financial loss.
The end result is a set of practical recommendations for risk mitigation that balance security needs with business realities and your available resources.
Security Audits
Security audits evaluate how well you’re following both internal security policies and external regulations. For businesses throughout New Jersey, from pharmaceutical companies in Princeton to financial services firms in Jersey City, regular security audits are essential for maintaining compliance.
These audits validate that your security controls are functioning as intended and identify any gaps between your written policies and actual practices. The documentation produced during an audit provides evidence for regulators and stakeholders that you’re taking security seriously.
“Many of our clients use our audit reports to demonstrate compliance during regulatory inspections,” explains our compliance specialist. “Having a third-party assessment carries more weight than internal reviews alone.”
Benefits of Regular Security Assessments
For businesses across New Jersey, from Elizabeth to Trenton, regular security assessments provide substantial benefits beyond just finding vulnerabilities.
First, they enable proactive risk management. By identifying and addressing vulnerabilities before they can be exploited, you stay ahead of attackers rather than scrambling to respond after a breach.
Second, they ensure compliance validation. Regular assessments verify that your security measures meet regulatory requirements, helping you avoid costly penalties and legal issues.
Third, they support resource optimization. Instead of spending your security budget based on guesswork or the latest headlines, assessments help you focus investments where they’re most needed for your specific environment.
Fourth, they improve security awareness across your organization. When employees see security being taken seriously through regular assessments, they’re more likely to follow security protocols themselves.
Finally, assessments provide third-party validation of your security from experts outside your organization. This objective perspective can identify blind spots that internal teams might miss due to familiarity.
At Titan Technologies, we provide comprehensive security assessments for businesses throughout central New Jersey. Our approach combines automated scanning with expert analysis to provide a complete picture of your security posture and actionable recommendations for improvement.
More info about Network Configuration Management
Benefits of Managed IT Services for Network Security in NJ
Running a business in New Jersey is challenging enough without having to worry about cyber threats lurking around every corner. For many small and medium-sized organizations across the Garden State, maintaining robust network security nj often feels like trying to build a fortress with limited resources and constantly changing blueprints. This is exactly where managed IT services shine brightest.
24/7 Proactive Monitoring and Management
Cyber criminals don’t clock out at 5 PM on Friday—they’re constantly probing for weaknesses in your defenses. With managed IT services, your network gains round-the-clock guardians who keep vigilant watch when you’re focused on running your business or even fast asleep.
“I feel secure knowing they are always working behind the scenes to ensure our data is secure,” shared one operations manager from a financial company in New Jersey who made the switch to managed services.
This continuous monitoring means suspicious activities get flagged immediately, potential threats are addressed before they can cause damage, and those critical security patches don’t sit waiting to be installed for weeks on end. It’s like having a security team that never takes a coffee break.
Access to Specialized Expertise
The cybersecurity landscape has grown incredibly complex—from ransomware and phishing to zero-day exploits and supply chain attacks. Keeping up with it all is practically a full-time job in itself.
When you partner with a managed IT provider for your network security nj needs, you’re not just getting generic tech support. You’re gaining access to security specialists who eat, sleep, and breathe cybersecurity. These professionals stay current on the latest threats targeting New Jersey businesses and bring specialized expertise that would be prohibitively expensive to maintain in-house.
For businesses in innovation hubs like Princeton and New Brunswick, this specialized knowledge can make the difference between being protected or becoming the next cautionary tale in the local business journal.
Cost-Effective Security Solutions
Let’s face it—building your own in-house security team with 24/7 coverage would require hiring multiple specialists, investing in ongoing training, and purchasing enterprise-grade security tools. For most New Jersey small businesses, that’s simply not realistic.
Managed IT services transform these unpredictable capital expenses into steady, predictable monthly costs. As one satisfied New Jersey business owner put it: “You can have a team of highly skilled network engineers and computer technicians providing computer support services for your business network at a fraction of a cost of a full-time employee.”
This budget-friendly approach means you’re not sacrificing security due to cost concerns. Instead, you’re leveraging economies of scale that only managed service providers can offer.
Scalable Security Solutions
Your business isn’t static, and neither should your security approach be. As your company grows—whether you’re expanding from Edison to Lakewood or adding remote workers across central New Jersey—your security needs evolve too.
Managed IT services excel at scaling alongside your business. Adding new locations? No problem. Bringing on dozens of new employees? Your security scales accordingly. Implementing new systems or cloud services? Your protection adapts without missing a beat.
This flexibility means your network security nj solution grows with you instead of becoming an obstacle to expansion—something particularly valuable in New Jersey’s dynamic business environment.
Comprehensive Security Approach
Effective security isn’t about having one really strong lock—it’s about having multiple layers of protection working together. Managed IT providers like Titan Technologies implement this layered approach automatically, covering all your bases:
Your endpoints get advanced protection against malware and ransomware. Your email systems gain shields against the phishing attempts that target New Jersey businesses daily. Your cloud applications receive proper security configurations. Your network gets continuous monitoring for unusual activity. Your data gets backed up regularly, with tested recovery procedures ready if disaster strikes.
Perhaps most importantly, your employees—often the weakest link in security—receive the training they need to recognize and avoid threats. This comprehensive shield provides protection that far exceeds what most organizations could implement on their own.
Focus on Core Business Functions
At the end of the day, the most significant benefit of managed IT services might be the simplest: peace of mind. When professionals are handling your network security nj needs, you and your team can redirect your energy toward what you do best.
Instead of your staff spending hours troubleshooting security alerts or researching compliance requirements, they can focus on serving customers, developing new products, or expanding into new markets. Your IT team, if you have one, can work on strategic initiatives rather than constantly putting out security fires.
At Titan Technologies, we’ve seen how this shift in focus transforms businesses across central New Jersey. Our clients sleep better knowing their digital assets are protected around the clock, allowing them to pour their passion into growing their businesses instead of worrying about the next cyber threat.
More info about Network Monitoring and Management
Latest Trends and Technologies in Network Security for NJ Businesses
The cybersecurity landscape never stands still. As threats evolve, so must your defenses. For network security nj to truly protect your business, staying current with emerging technologies isn’t optional—it’s essential.
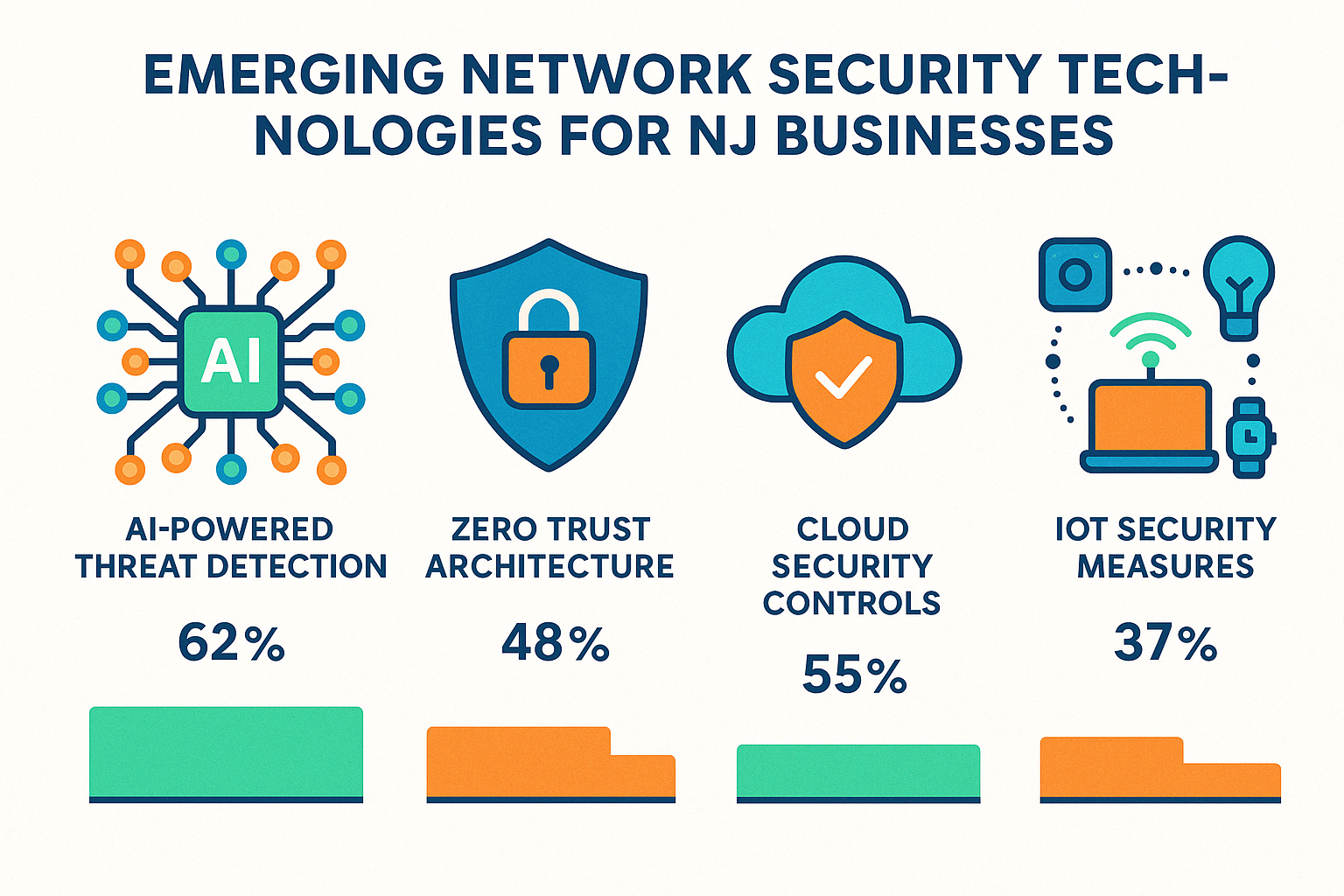
Artificial Intelligence and Machine Learning
Remember when security meant simply installing antivirus software? Those days are long gone. Today’s AI-powered security solutions act like tireless digital sentinels for your business.
For companies in tech hubs like Princeton and New Brunswick, AI security tools are game-changers. They sift through mountains of data to spot attack patterns that human analysts might miss. What makes them particularly valuable is their ability to learn and adapt—identifying anomalies that could signal previously unknown threats and automatically responding to common attacks.
“The difference between traditional security and AI-powered solutions is like comparing a security guard to a mind reader,” explains one of our security specialists at Titan Technologies. “AI doesn’t just watch for known problems—it anticipates what might happen next.”
Cloud Security Advancements
As your business accepts cloud services, your security approach needs to evolve too. Modern cloud security isn’t just about protecting data—it’s about creating a secure environment no matter where your employees work.
For New Jersey businesses with remote teams (which, let’s face it, is most of us these days), tools like Cloud Access Security Brokers (CASBs) provide visibility into all cloud applications your team uses. Cloud Workload Protection Platforms safeguard your virtual machines and containers, while Cloud Security Posture Management ensures nothing is misconfigured—which is like making sure you haven’t accidentally left a window open in your digital house.
Perhaps most exciting is the emergence of Secure Access Service Edge (SASE) technology, which combines network security functions with wide-area networking capabilities—perfect for businesses with employees spread across central New Jersey and beyond.
IoT Security Solutions
The Internet of Things has connected everything from office thermostats to manufacturing equipment—creating convenience but also new security headaches. For network security nj implementations, addressing these challenges is becoming increasingly crucial.
Manufacturing businesses in Elizabeth and Woodbridge particularly need to secure industrial IoT devices. The most effective approach combines network segmentation (keeping IoT devices in their own digital “neighborhood”), specialized monitoring tools, and automated patching systems.
“Think of unsecured IoT devices as open uped side doors to your network,” notes our security team. “They might seem insignificant, but they can provide easy access to your most valuable assets.”
Extended Detection and Response (XDR)
When it comes to security visibility, more is definitely better. XDR platforms bring together intelligence from multiple security layers—endpoints, networks, email, cloud services, and user behavior—creating a comprehensive view of your security landscape.
This unified approach helps businesses spot sophisticated attacks that might otherwise slip through the cracks. For New Jersey organizations with complex IT environments, XDR provides the digital equivalent of having eyes in the back of your head—nothing sneaks past unnoticed.
Security Orchestration, Automation, and Response (SOAR)
For many central New Jersey businesses, limited security resources are a fact of life. SOAR technologies help these teams work smarter, not harder.
By automating routine security tasks and standardizing incident response procedures, SOAR tools free up your team to focus on more strategic work. They also improve collaboration among team members and integrate your various security tools into a cohesive system.
One of our clients described the difference after implementing SOAR: “Before, we were constantly chasing alerts like firefighters. Now, we’re more like fire marshals—preventing problems before they start.”
The Importance of Zero Trust in Network Security NJ
Remember when network security was like a castle with a moat? Once someone got past the perimeter, they had free reign inside. Zero Trust turns this model on its head with a simple philosophy: trust nothing, verify everything.
Key Principles of Zero Trust Security
The Zero Trust approach has become particularly crucial for network security nj implementations. At its core are three fundamental principles:
First, verify explicitly. This means always authenticating and authorizing based on all available information—who the user is, where they’re connecting from, what device they’re using, and whether anything seems unusual about their behavior.
Second, use least privileged access. Users should only have access to exactly what they need, when they need it—no more, no less. This limits potential damage if an account is compromised.
Finally, assume breach. This mindset means designing your security as if attackers are already inside your network, using techniques like micro-segmentation to limit their movement and continuous monitoring to detect suspicious activity.
Implementing Zero Trust for New Jersey Businesses
For businesses throughout central New Jersey, from New Brunswick to Red Bank, implementing Zero Trust isn’t a single product purchase—it’s a strategic shift.
“Zero Trust isn’t just a technology—it’s a strategy that requires rethinking how we approach security at every level,” explains one of our cybersecurity experts at Titan Technologies.
The journey typically begins with strong identity and access management solutions, including multi-factor authentication. Network micro-segmentation follows, creating smaller, more defensible zones within your network. Throughout the process, continuous monitoring and validation ensure nothing suspicious goes unnoticed.
Perhaps most importantly, Zero Trust accepts data-centric security controls that protect your information regardless of where it lives—crucial in today’s world where your data might be accessed from an employee’s kitchen table in Matawan or a coffee shop in Freehold.
At Titan Technologies, we help businesses across central New Jersey implement these cutting-edge security approaches, custom to your specific needs and environment. The threats may be evolving, but with the right technology and strategy, your defenses can stay one step ahead.
Ensuring Compliance with Cybersecurity Regulations in New Jersey
New Jersey businesses face a complex mix of cybersecurity regulations that can feel overwhelming to steer. Understanding and complying with these regulations isn’t just about avoiding penalties—it’s a fundamental part of creating an effective network security nj strategy that protects your business and builds customer trust.
Key Regulations Affecting New Jersey Businesses
When it comes to data protection in the Garden State, several regulations stand out as particularly important for local businesses.
The New Jersey Identity Theft Prevention Act puts real responsibilities on your shoulders as a business owner. You’ll need to implement reasonable safeguards to protect personal information—think encryption, access controls, and secure disposal methods. If you experience a breach, you’re required to notify affected customers promptly. And when those records containing personal information are no longer needed? The law requires you to destroy them securely.
“Many small business owners I work with are surprised to learn they have specific legal obligations under New Jersey law,” explains one compliance specialist. “They often assume these regulations only apply to large corporations.”
The New Jersey Cybersecurity and Communications Integration Cell (NJCCIC) serves as our state’s cybersecurity information hub. While they don’t create regulations themselves, they’re an invaluable resource for staying informed about threats specifically targeting New Jersey businesses. They provide regular alerts that can help you stay ahead of emerging threats, offer incident reporting mechanisms if you do experience a breach, and maintain a wealth of resources to help with compliance.
Beyond state requirements, many federal regulations may apply to your business depending on your industry. If you’re in healthcare, HIPAA compliance is non-negotiable. Financial institutions need to follow GLBA guidelines. Process credit card payments? PCI DSS standards apply to you. Defense contractors face CMMC requirements, and if you have European customers, GDPR compliance enters the picture as well.
Compliance Strategies for NJ Businesses
Creating a workable compliance strategy doesn’t have to be overwhelming. Start by identifying which regulations actually apply to your specific business. There’s no one-size-fits-all approach here—your industry, the types of data you handle, and your customer base all determine which rules you need to follow.
Regular assessments are your friend in this process. Think of them as health check-ups for your security posture. We recommend quarterly reviews where you can identify gaps in your compliance and create action plans to address them. These assessments often reveal simple fixes that can make a big difference in your security stance.
Documentation matters more than you might think. Well-documented policies and procedures aren’t just paperwork—they’re your roadmap for consistent security practices and your evidence of compliance efforts. Keep comprehensive records of your security controls, employee training, and incident response procedures.
Of course, implementing the right technical controls is essential. This includes encryption for sensitive data, robust access controls that limit who can see what information, and monitoring systems that alert you to suspicious activity. These technical measures form the backbone of your compliance efforts.
Don’t forget the human element—employee training remains one of the most effective compliance tools available. Your team needs to understand not just what the rules are, but why they matter and how to follow them in daily operations. Regular training sessions keep security awareness fresh and help prevent costly mistakes.
Finally, be ready for the worst with incident response planning. Having a tested plan in place before a breach occurs can dramatically reduce damage and recovery time. Make sure your plan includes the notification procedures required by New Jersey regulations.
Resources for Compliance Assistance
You don’t have to tackle compliance alone. New Jersey businesses have several helpful resources at their disposal.
The NJCCIC website should be bookmarked on every business owner’s computer. It provides New Jersey-specific guidance that’s regularly updated to reflect the latest threats and regulatory changes. They even offer cybersecurity education programs custom to New Jersey businesses and organizations.
Industry associations often develop specialized compliance guidance for their members. These resources can be particularly valuable because they understand the unique challenges of your specific business sector.
Many businesses throughout central New Jersey find that working with a managed IT service provider like Titan Technologies provides the expertise they need without having to build an in-house compliance team. We help businesses from Princeton to Red Bank understand exactly which regulations apply to them and implement the right security controls to meet those requirements.
“Compliance isn’t just about checking boxes—it’s about implementing meaningful security measures that protect your business and your customers,” notes a legal professional specializing in New Jersey data protection laws. This perspective highlights why compliance should be viewed as an opportunity to strengthen your security posture rather than just a regulatory burden.
Cybersecurity regulations and education in NJ
At Titan Technologies, we guide businesses through the sometimes confusing landscape of cybersecurity regulations with practical, straightforward advice. We understand that compliance can feel overwhelming, especially for smaller businesses without dedicated IT security staff. Our compliance-focused network security nj solutions ensure you meet all applicable requirements while maintaining robust protection against the ever-changing threat landscape.
Frequently Asked Questions about Network Security in NJ
What are the most common cyber threats faced by NJ businesses?
When it comes to cyber threats in the Garden State, New Jersey businesses face a constantly evolving landscape of digital dangers.
Phishing attacks remain one of the most prevalent threats, with crafty cybercriminals creating increasingly convincing emails designed to trick your employees. The New Jersey Cybersecurity & Communications Integration Cell (NJCCIC) regularly reports on these campaigns, including recent ones distributing nasty LokiBot malware through innocent-looking compressed files.
Ransomware continues to be a nightmare for many organizations across NJ. Just ask the municipalities and healthcare providers who’ve had their systems locked down, only to find ransom demands in the hundreds of thousands of dollars. It’s like having a digital padlock slapped on your most important files – except you don’t have the key.
For businesses that handle wire transfers (which is most of us these days), business email compromise poses a serious risk. These aren’t your garden-variety scams – they involve sophisticated tactics like compromising executive email accounts to authorize fraudulent transfers. For companies in financial centers like Newark and Princeton, this threat hits particularly close to home.
Credential theft remains a persistent problem, with attackers constantly looking for ways to snatch your login information. Once they have your passwords, they essentially have the keys to your digital kingdom.
Supply chain attacks have become increasingly common, as highlighted by the NJCCIC. Rather than targeting your business directly, attackers strike at your vendors and partners, using them as a backdoor into your systems. It’s like securing your front door with a state-of-the-art lock while leaving your side entrance wide open.
I recommend regularly checking the NJCCIC’s Cyber Alert Level for New Jersey to stay informed about emerging threats in our area. It’s a valuable resource that helps you understand the current threat landscape without needing a cybersecurity degree.
How can small businesses in NJ protect their networks from cyber attacks?
Small businesses across New Jersey often think they’re too small to be targeted. Unfortunately, cybercriminals see things differently – they view smaller companies as low-hanging fruit with fewer defenses.
Start with the basics: invest in a proper business-grade firewall (not the consumer version that came with your internet package). Install reputable antivirus software on all devices, and make “update everything” a regular habit. Those pesky software updates you keep postponing? They often contain critical security patches.
Your employees are both your greatest asset and potentially your biggest security vulnerability. Regular security awareness training isn’t a luxury – it’s essential. Help them recognize phishing attempts and establish clear security policies. As one small business owner in Matawan told us: “Working with a managed IT provider gave us enterprise-level security that we could never have achieved on our own. It’s been a game-changer for our business.”
Network security nj isn’t complete without a solid backup strategy. Think of backups as your insurance policy – you hope you never need them, but you’ll be incredibly grateful if you do. Maintain regular backups of critical data, store them in multiple locations (including off-site), and regularly test your restoration process. A backup you can’t restore is just wasted storage space.
With so many employees working remotely across New Jersey, securing mobile devices has become crucial. Implement mobile device management solutions that require strong authentication and enable remote wiping if devices are lost or stolen. When your team connects from coffee shops in Trenton or home offices in Red Bank, make sure they’re using secure VPN connections.
For many small businesses, partnering with a managed service provider like Titan Technologies offers the most comprehensive protection. You get enterprise-level security expertise without the enterprise-level cost of hiring full-time security staff. Think of it as having a dedicated security team on call 24/7, monitoring your systems and responding to threats before they become disasters.
What advantages do managed IT services offer for network security in NJ?
For many New Jersey businesses, especially smaller ones, keeping up with cybersecurity can feel like trying to bail out a leaking boat with a teacup. Managed IT services change that equation dramatically.
First and foremost, you get around-the-clock monitoring and response capabilities. Cyber attackers don’t clock out at 5 PM or take weekends off – and neither does your managed security team. When suspicious activity occurs at 2 AM, you’ll have experts responding immediately, not finding the problem when the office opens the next morning.
Access to specialized security expertise is perhaps the most valuable advantage. The cybersecurity landscape changes daily, and keeping up requires dedicated professionals who eat, sleep, and breathe security. A good network security nj provider employs certified experts who understand both global threats and challenges specific to New Jersey businesses.
Rather than implementing piecemeal security solutions, managed services provide comprehensive protection across your entire digital environment. This layered approach addresses multiple threat vectors simultaneously, from email security to endpoint protection, network monitoring to vulnerability management. It’s like having a security system that protects not just your doors and windows, but every possible entry point.
The cost efficiency is undeniable. Instead of making large upfront investments in security infrastructure and hiring specialized staff (who command premium salaries in the competitive New Jersey job market), you pay a predictable monthly fee. This approach transforms cybersecurity from a capital expense to an operational one, making budgeting more straightforward and often reducing overall costs.
As your business grows – whether you’re expanding from Princeton to Parsippany or adding remote workers across central New Jersey – managed IT services scale with you. Your security solutions adapt to your changing business needs without requiring complete overhauls or significant new investments.
At Titan Technologies, we understand the unique challenges facing businesses throughout central New Jersey. Our team of security professionals works tirelessly behind the scenes, monitoring your systems and addressing potential threats before they impact your operations. This proactive approach gives you something invaluable: peace of mind knowing your digital assets are protected while you focus on growing your business.
Conclusion
In the digital landscape of New Jersey, network security isn’t just an IT concern—it’s a fundamental business imperative. As we’ve explored throughout this guide, the threats facing businesses across the Garden State are diverse and evolving, from sophisticated malware to targeted phishing campaigns and ransomware attacks.
The statistics are sobering: 1 in 5 organizations will experience a breach this year, with small and medium-sized businesses being particularly vulnerable. Yet there’s also reason for optimism, as network security nj solutions continue to advance, and resources like the NJCCIC provide valuable support for local businesses.
Think of your business network as your digital home. You wouldn’t leave your front door open uped in a neighborhood where break-ins happen regularly. Similarly, in today’s digital neighborhood, leaving your network unprotected is an invitation for trouble. The good news? With the right locks, alarm systems, and vigilance, you can keep the digital intruders at bay.
The key to effective protection lies in a comprehensive, multi-layered approach that addresses all aspects of security. It’s like protecting your home with not just a strong front door, but also window locks, motion sensors, and security cameras. For your network, this means implementing robust technical controls like firewalls and encryption, conducting regular security assessments to find weak spots, providing employee training to strengthen your human firewall, maintaining proactive monitoring for suspicious activity, and ensuring compliance with relevant regulations.
Perhaps most importantly, businesses must recognize that security is not a one-time project but an ongoing process that requires continuous attention and adaptation. Just as you wouldn’t install a home security system and never check if it’s working, your network security needs regular maintenance and updates to stay effective against evolving threats.
“97% of breaches could have been prevented with today’s technology.”
This statistic highlights something truly encouraging: most security breaches aren’t inevitable disasters—they’re preventable with the right combination of technology, processes, and people. It’s like knowing that 97% of home break-ins could be prevented with proper locks and alarm systems. With that knowledge, wouldn’t you make sure your home is secure?
At Titan Technologies, we’re committed to helping businesses throughout central New Jersey implement effective security strategies that protect their digital assets and enable their growth. We understand that every business is unique, with its own security challenges and requirements. Whether you’re a healthcare provider in Princeton concerned about HIPAA compliance, a financial services firm in Newark handling sensitive client data, or a manufacturing company in Elizabeth protecting intellectual property, we tailor our solutions to your specific needs.
Our professional team provides fast, reliable support with a 100% satisfaction guarantee, ensuring that your network remains secure and your business remains productive. From Edison to Trenton, Princeton to Red Bank, we serve businesses across central New Jersey with customized security solutions designed to address their specific needs and challenges.
Don’t wait for a breach to occur before taking action. Contact Titan Technologies today to schedule a comprehensive security assessment and take the first step toward robust protection for your digital business.