Why Network Management in Operating System is Your Business’s Hidden Powerhouse
Network management in operating system is the set of processes, tools, and capabilities that your OS uses to control, monitor, and maintain network connections and resources. Think of it as the invisible conductor orchestrating every piece of data that flows through your business network.
Here’s what your operating system handles for network management:
• Fault Management – Detects and resolves network issues before they impact operations
• Configuration Management – Controls network settings, IP addresses, and device parameters
• Performance Management – Monitors bandwidth, latency, and network utilization
• Security Management – Enforces firewalls, access controls, and authentication
• Accounting Management – Tracks network usage and resource allocation
The numbers tell the story: the global network management market hit $9.3 billion in 2022 and is growing at 9.4% annually. More telling? 56% of IT professionals don’t fully understand how their networks are configured, and one in three network issues are reported by frustrated end users before IT teams even know there’s a problem.
Your operating system sits at the center of this complexity, managing everything from network interface cards and routing tables to DNS resolution and Quality of Service controls. It’s handling thousands of network decisions every second – decisions that directly impact your business productivity, security, and bottom line.
I’m Paul Nebb, founder of Titan Technologies, and I’ve spent over 15 years helping businesses understand and optimize their network management in operating system environments. Through my work with companies across the tri-state area, I’ve seen how proper OS-level network management transforms chaotic IT into smooth, predictable operations.
Basic network management in operating system vocab:
– network configuration management
– network operations center services
– network security management
Network Management in Operating System: Definition & Importance
Think of your operating system as the ultimate multitasker. While you’re busy running spreadsheets and video calls, your OS is quietly managing thousands of network decisions every second. Network management in operating system environments goes far beyond just connecting to WiFi—it’s the complete operations, administration, maintenance, and provisioning (OAM&P) of every networked component in your business.
Your OS is essentially running a sophisticated control center that handles everything from detecting when your internet connection hiccups to managing which applications get priority bandwidth. It’s working around the clock to keep your business connected, secure, and running smoothly.
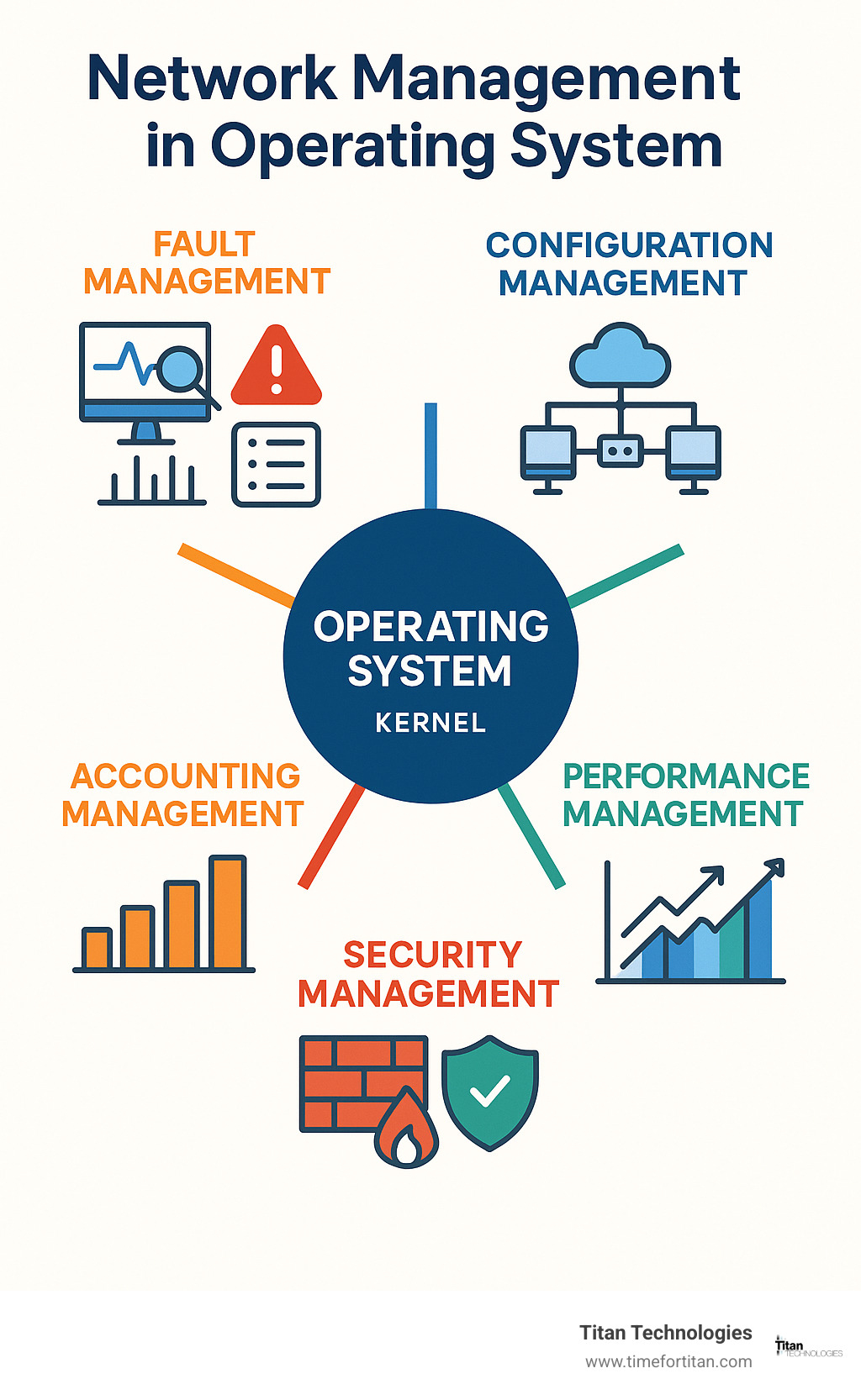
The technology industry uses something called the ISO FCAPS model to understand how network management really works. This framework breaks down the complexity into five manageable pieces: fault management keeps your network running when things go wrong, configuration management handles all the technical settings, accounting management tracks who’s using what resources, performance management makes sure everything runs fast, and security management keeps the bad guys out.
Here’s where the numbers get sobering. Research shows that more than 50% of network outages happen because of simple human errors—problems that proper network management in operating system environments can prevent automatically. When your network goes down for just one hour, you’re looking at thousands or even millions in lost productivity and revenue.
The global network management systems market tells the story of how critical this has become. We’re looking at $14.6 billion by 2027, driven by businesses realizing they can’t afford to manage networks manually anymore. The complexity of modern hybrid cloud environments demands intelligent, automated network operations.
Key objectives of network management in operating system
When we talk about what network management in operating system environments are trying to achieve, it comes down to four fundamental goals that directly impact your business success.
Availability means your network stays up and running no matter what happens. Your OS handles this through sophisticated backup systems, automatic failover when something breaks, and recovery procedures that kick in without human intervention. Modern operating systems are incredibly smart about maintaining service continuity—they can detect when a component is failing and automatically switch to backup systems before you even notice a problem.
Performance optimization happens at the deepest levels of your OS, where it manages network traffic like a skilled air traffic controller. The operating system continuously monitors how much bandwidth different applications are using, measures response times, and adjusts traffic flow to keep everything running smoothly. It implements Quality of Service controls that ensure your video conference doesn’t get interrupted by someone downloading large files.
Security enforcement works through multiple layers of protection built right into your operating system. From the moment data hits your network card to when it reaches your applications, the OS is checking credentials, enforcing firewall rules, and making sure encrypted data stays encrypted. It’s like having a security team that never sleeps and never misses a threat.
Compliance requirements have become increasingly important as regulations get stricter. Your OS automatically creates detailed logs of network activity, maintains audit trails, and generates reports that help you meet standards like HIPAA, SOX, and GDPR. This isn’t just about avoiding fines—it’s about protecting your business reputation and customer trust.
How network management in operating system evolved from NOS to cloud-native
The story of how network management in operating system environments evolved is really the story of how business computing grew up. Back in the early days, we had clear separation between regular operating systems that ran programs and special Network Operating Systems (NOS) that handled networking.
Those early networks used simple peer-to-peer models where every computer could talk directly to every other computer. This worked great for small offices with maybe five or ten computers, but it became a nightmare as businesses grew. Imagine trying to manage passwords and permissions for hundreds of computers when each one has its own rules.
The solution was client-server architecture, where powerful central servers managed network resources and security for many client computers. This gave us the centralized control and directory services that made large business networks possible. Suddenly, you could manage thousands of users from one central location.
Fast-forward to today, and the line between operating systems and network operating systems has completely disappeared. Modern operating systems like Windows, Linux, and macOS have incredibly sophisticated networking built right in. We’ve entered the age of Software-Defined Networking (SDN), where network behavior is controlled by software running on standard computers rather than expensive specialized hardware.
The current landscape is all about hybrid-cloud environments where network management in operating system must seamlessly handle your office computers, cloud services, and mobile devices all at the same time. Your OS needs to be smart enough to route traffic between your local server, Amazon Web Services, and your employee’s laptop working from a coffee shop—all while maintaining security and performance standards.
This evolution has made network management both incredibly powerful and surprisingly complex, requiring much deeper integration between your operating system’s core functions and its networking capabilities.
Core Components and Functions: From FCAPS to Automation
Modern network management in operating system environments have evolved far beyond the traditional FCAPS model. While fault, configuration, accounting, performance, and security management remain foundational, today’s systems add critical capabilities like automated provisioning, advanced observability, and intelligent automation.
The operating system now handles network management through multiple integrated subsystems. The network stack manages protocol handling and packet processing. Device drivers control network interface cards and handle hardware-specific operations. The routing subsystem maintains forwarding tables and implements traffic engineering policies. Security modules enforce access controls and encryption standards.
Network configuration management has become increasingly sophisticated, with operating systems now supporting template-based configurations, automated rollbacks, and version control for network settings. This evolution addresses the reality that 64% of enterprises use 4-10 different tools to troubleshoot their networks, creating dangerous fragmentation in network management capabilities.
Fault & Performance Management
Your operating system continuously monitors network health through multiple mechanisms. At the lowest level, network interface drivers report hardware status, link state changes, and error conditions. The OS correlates this information with higher-level performance metrics to provide comprehensive fault detection.
Modern network management in operating system implementations use sophisticated baseline establishment and anomaly detection. The OS tracks normal network behavior patterns—bandwidth utilization, latency distributions, error rates—and automatically flags deviations that might indicate problems.
Performance monitoring happens in real-time through technologies like NetFlow and streaming telemetry. Your OS can analyze traffic patterns, identify bottlenecks, and even implement automatic Quality of Service adjustments to maintain optimal performance. Network automation tools can respond to performance issues faster than human administrators, often resolving problems before users notice any impact.
Alert systems have evolved from simple threshold-based notifications to intelligent correlation engines that can distinguish between symptoms and root causes. This is crucial because one in three network issues are still reported by end users before IT teams detect them—a clear sign that traditional monitoring approaches need improvement.
Configuration & Provisioning
Configuration management in modern network management in operating system environments relies heavily on template-based approaches and infrastructure-as-code principles. The OS maintains configuration templates that can be rapidly deployed across multiple network devices and interfaces, ensuring consistency and reducing configuration errors.
Version control for network configurations has become standard practice, with the OS maintaining historical records of all configuration changes. This enables rapid rollback capabilities when changes cause problems—a critical feature given that more than 50% of network outages result from human error during configuration changes.
Automated provisioning capabilities allow the OS to detect new network devices and automatically configure them according to organizational policies. This might include IP address assignment through DHCP, VLAN configuration, security policy application, and Quality of Service settings.
The separation of setup and activation phases in configuration management allows administrators to prepare complex changes offline, validate them through testing, and then activate them quickly during maintenance windows. This approach minimizes downtime and reduces the risk of configuration errors.
Security & Accounting Management
Security management in network management in operating system environments operates at multiple layers simultaneously. The OS implements network-level security through integrated firewall capabilities, intrusion detection systems, and access control mechanisms.
Modern operating systems support advanced authentication mechanisms including multi-factor authentication (MFA), certificate-based authentication, and integration with enterprise directory services. The OS can enforce role-based access control, ensuring that users and applications only access network resources they’re authorized to use.
Network security monitoring has become increasingly sophisticated, with OS-level capabilities for deep packet inspection, behavior analysis, and threat correlation. The system can automatically respond to security threats by implementing traffic filtering, quarantining affected systems, or alerting security teams.
Accounting management tracks network resource usage for both operational and billing purposes. The OS maintains detailed logs of network activity, bandwidth consumption, and service utilization. This information supports capacity planning, cost allocation, and compliance reporting requirements.
How Operating Systems Deliver Network Magic
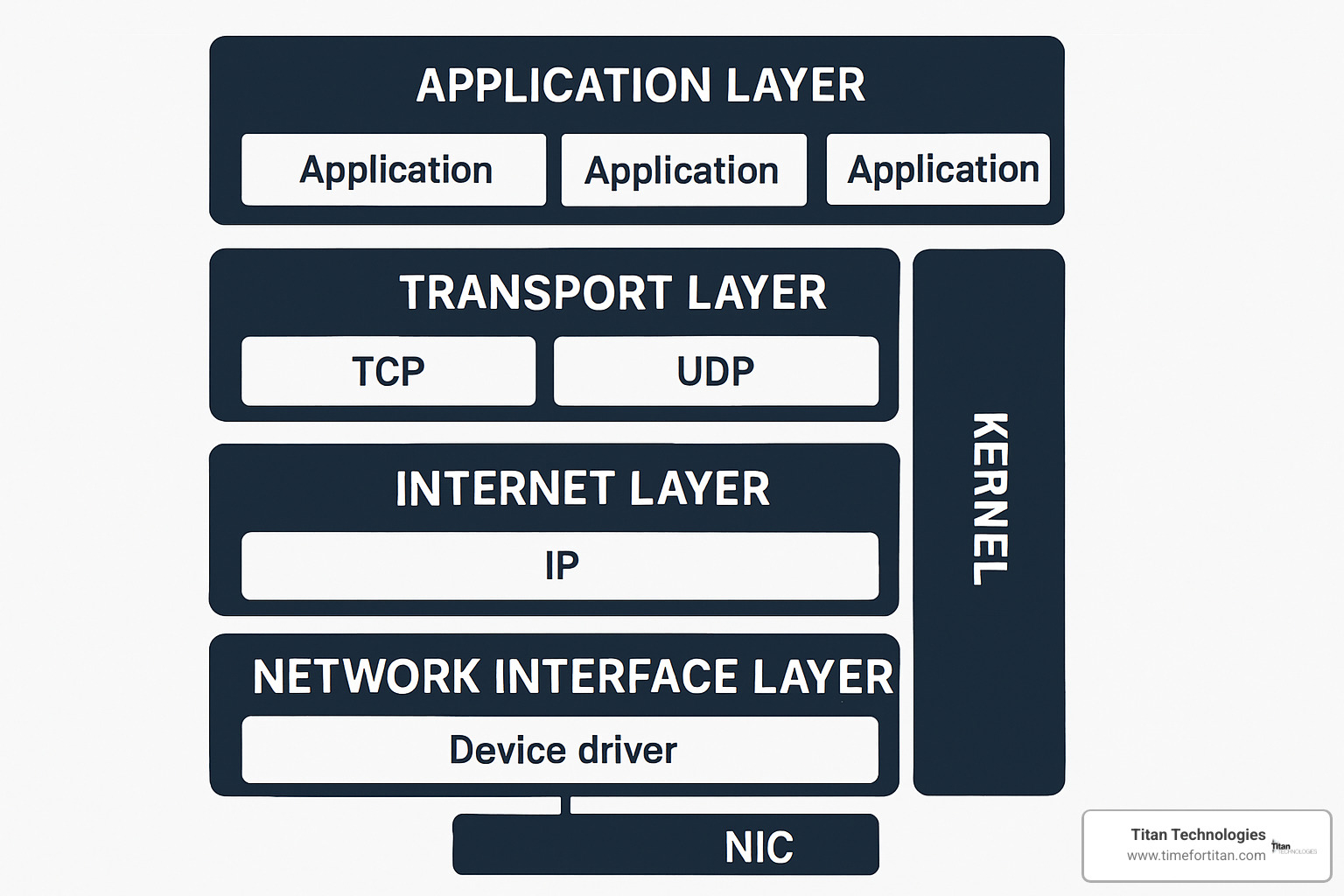
The real magic of network management in operating system environments happens in the network stack—a complex layered architecture that seamlessly handles everything from physical network interfaces to application-level protocols.
At the hardware level, your OS manages Network Interface Card (NIC) drivers that control the physical connection to your network. These drivers handle the complex process of converting digital data into electrical signals and managing the timing and protocols required for reliable data transmission.
The OS maintains multiple network interfaces simultaneously—physical Ethernet ports, wireless adapters, VPN connections, and virtual interfaces. Each interface can be configured with different IP addresses, routing policies, and security settings. The OS automatically handles the complexity of routing traffic through the most appropriate interface based on destination, policy, and current network conditions.
IPv4 and IPv6 addressing are handled transparently by the OS, which maintains routing tables that determine how to reach different network destinations. Modern operating systems can handle dual-stack configurations, seamlessly supporting both IPv4 and IPv6 protocols simultaneously.
DNS caching is built into the OS network stack, reducing latency and network traffic by storing frequently accessed domain name resolutions locally. The OS also implements sophisticated DNS security features, including DNS over HTTPS and DNS filtering capabilities.
Quality of Service (QoS) controls allow the OS to prioritize different types of network traffic. Business-critical applications can receive guaranteed bandwidth, while less important traffic is deprioritized during network congestion.
Virtualization capabilities enable the OS to create virtual network interfaces, software-defined networks, and isolated network namespaces. This allows multiple applications or virtual machines to share physical network resources while maintaining security and performance isolation.
Low-level resource control
Network management in operating system environments requires precise control over low-level system resources. The OS manages network buffers—memory areas where incoming and outgoing network data is temporarily stored. Buffer management is critical for performance; too few buffers cause packet loss, while too many buffers waste memory and can increase latency.
Socket management provides the interface between applications and the network stack. The OS maintains socket tables, handles connection state, and implements flow control mechanisms that prevent network congestion. Advanced operating systems implement sophisticated socket scheduling algorithms that ensure fair access to network resources across multiple applications.
Interrupt handling is crucial for network performance. When network data arrives, the network interface generates hardware interrupts that must be processed quickly to avoid packet loss. Modern operating systems use techniques like interrupt coalescing and NAPI (New API) polling to balance responsiveness with CPU efficiency.
The OS also manages network-related kernel threads and processes that handle background network operations like routing table updates, neighbor findy, and network service daemons. These processes must be carefully scheduled to ensure they don’t interfere with time-critical network operations.
Tools & Commands every admin should know
Effective network management in operating system environments requires familiarity with key diagnostic and management tools. The specific tools vary by operating system, but the concepts remain consistent across platforms.
On Linux systems, netstat provides comprehensive information about network connections, routing tables, and interface statistics. The newer ss command offers similar functionality with better performance for large systems. The ip command from the iproute2 package has largely replaced older tools like ifconfig and route, providing unified management of network interfaces, routing, and tunnels.
Windows administrators rely heavily on PowerShell cmdlets for network management. Commands like Get-NetAdapter, Get-NetRoute, and Test-NetConnection provide detailed network information and diagnostic capabilities. The Windows Event Log system provides comprehensive logging of network events that can be analyzed for troubleshooting and security monitoring.
Both platforms provide packet capture capabilities through tools like tcpdump on Linux and netsh trace on Windows. These tools are invaluable for diagnosing complex network problems and understanding actual network behavior.
Log analysis is crucial for effective network management. Operating systems generate extensive logs of network activity, from connection attempts and routing changes to security events and performance metrics. Understanding how to analyze these logs is essential for maintaining healthy networks.
Network management in operating system for virtual and container networks
Modern network management in operating system environments must handle increasingly complex virtualized networking scenarios. Virtual Network Interface Cards (vNICs) allow multiple virtual machines to share physical network hardware while maintaining network isolation and security.
Software bridges and switches implemented in the OS kernel provide Layer 2 connectivity between virtual machines and external networks. These virtual switches can implement VLANs, traffic filtering, and Quality of Service controls just like physical network equipment.
Overlay networks enable complex multi-tenant networking scenarios where multiple isolated networks can coexist on the same physical infrastructure. Technologies like VXLAN and GENEVE allow the OS to create virtual networks that span multiple physical hosts and data centers.
Container networking adds another layer of complexity, with technologies like Kubernetes Container Network Interface (CNI) plugins that integrate container orchestration with OS-level network management. The OS must handle dynamic network configuration as containers are created, moved, and destroyed.
Network namespaces provide complete network isolation within a single OS instance, allowing different applications or containers to have completely separate network stacks, routing tables, and firewall rules.
Protocols, Automation, and Future Trends
The protocols that enable network management in operating system environments have evolved significantly from the early days of simple monitoring tools. Today’s systems use sophisticated protocols for monitoring, configuration, and automation that enable unprecedented levels of network intelligence and control.
Simple Network Management Protocol (SNMP) remains the foundation of network monitoring, but it’s being supplemented and sometimes replaced by more advanced approaches. SNMP provides a standardized way for network devices to report status information and accept configuration commands, but its polling-based approach can be inefficient for large-scale networks.
Internet Control Message Protocol (ICMP) provides essential network diagnostic capabilities, enabling tools like ping and traceroute that are fundamental to network troubleshooting. Modern operating systems implement sophisticated ICMP handling that can provide detailed path and performance information.
NetFlow and similar technologies provide detailed traffic analysis capabilities, allowing the OS to understand exactly what types of traffic are flowing through the network. This information is crucial for capacity planning, security monitoring, and performance optimization.
Streaming telemetry represents the future of network monitoring, with network devices pushing real-time performance data to management systems rather than waiting to be polled. This approach provides much more timely and detailed information about network behavior.
Artificial Intelligence and Machine Learning are increasingly integrated into network management in operating system environments, enabling predictive analytics, automated problem resolution, and intelligent traffic optimization. These technologies can detect patterns and anomalies that would be impossible for human administrators to identify.
Intent-based networking represents a paradigm shift where administrators specify desired outcomes rather than detailed configurations. The OS and network management systems automatically implement the necessary configurations to achieve those outcomes.
Zero-trust networking principles are being built into OS-level network management, with every network connection authenticated and authorized regardless of its source or destination.
For more comprehensive network management, consider our Network Operations Center Services that provide 24/7 monitoring and management of your network infrastructure.
Choosing and securing management protocols
Selecting appropriate protocols for network management in operating system environments requires balancing functionality, security, and performance requirements. Modern implementations emphasize encrypted communications, with protocols like HTTPS, SSH, and TLS becoming standard for management traffic.
Access control mechanisms ensure that only authorized personnel can access network management functions. This includes not just authentication, but also role-based authorization that limits what each user can view and modify. The OS can integrate with enterprise directory services to provide centralized user management.
Rate limiting protects management systems from being overwhelmed by monitoring traffic or malicious attacks. The OS can implement sophisticated rate limiting that prioritizes critical management traffic while throttling less important activities.
Protocol selection often involves trade-offs between real-time capabilities and resource consumption. Streaming telemetry provides immediate visibility into network behavior but requires more bandwidth and processing power than traditional polling-based approaches.
Security considerations are paramount, with management protocols being prime targets for attackers. The OS must implement strong encryption, authentication, and access controls while maintaining the performance and reliability required for effective network management.
Automation & AI drive next-gen network management in operating system
The future of network management in operating system environments is increasingly automated and intelligent. Automation playbooks can handle routine network management tasks like configuration updates, security patching, and performance optimization without human intervention.
Anomaly detection systems use machine learning algorithms to understand normal network behavior and automatically identify deviations that might indicate problems. These systems can often detect issues before they impact users, enabling proactive problem resolution.
Self-healing networks represent the ultimate goal of network automation, where the OS can automatically diagnose and resolve network problems without human intervention. While we’re not there yet, current systems can handle many routine problems automatically.
The integration of AI and ML into network management in operating system environments enables predictive maintenance, where the system can identify potential problems before they occur and take preventive action. This approach can significantly reduce unplanned downtime and improve overall network reliability.
Network automation is projected to grow from $3.4 billion in 2021 to over $8.3 billion by 2026, driven by the need to manage increasingly complex networks with limited human resources.
Best Practices & Real-World Challenges
Implementing effective network management in operating system environments requires addressing numerous challenges while following proven best practices. The complexity of modern networks, combined with the need for high availability and security, creates a challenging environment for network administrators.
Scalability remains one of the biggest challenges in network management. Networks must be designed to handle growth in both the number of devices and the volume of traffic. The OS must be configured to handle these scaling requirements without degrading performance or reliability.
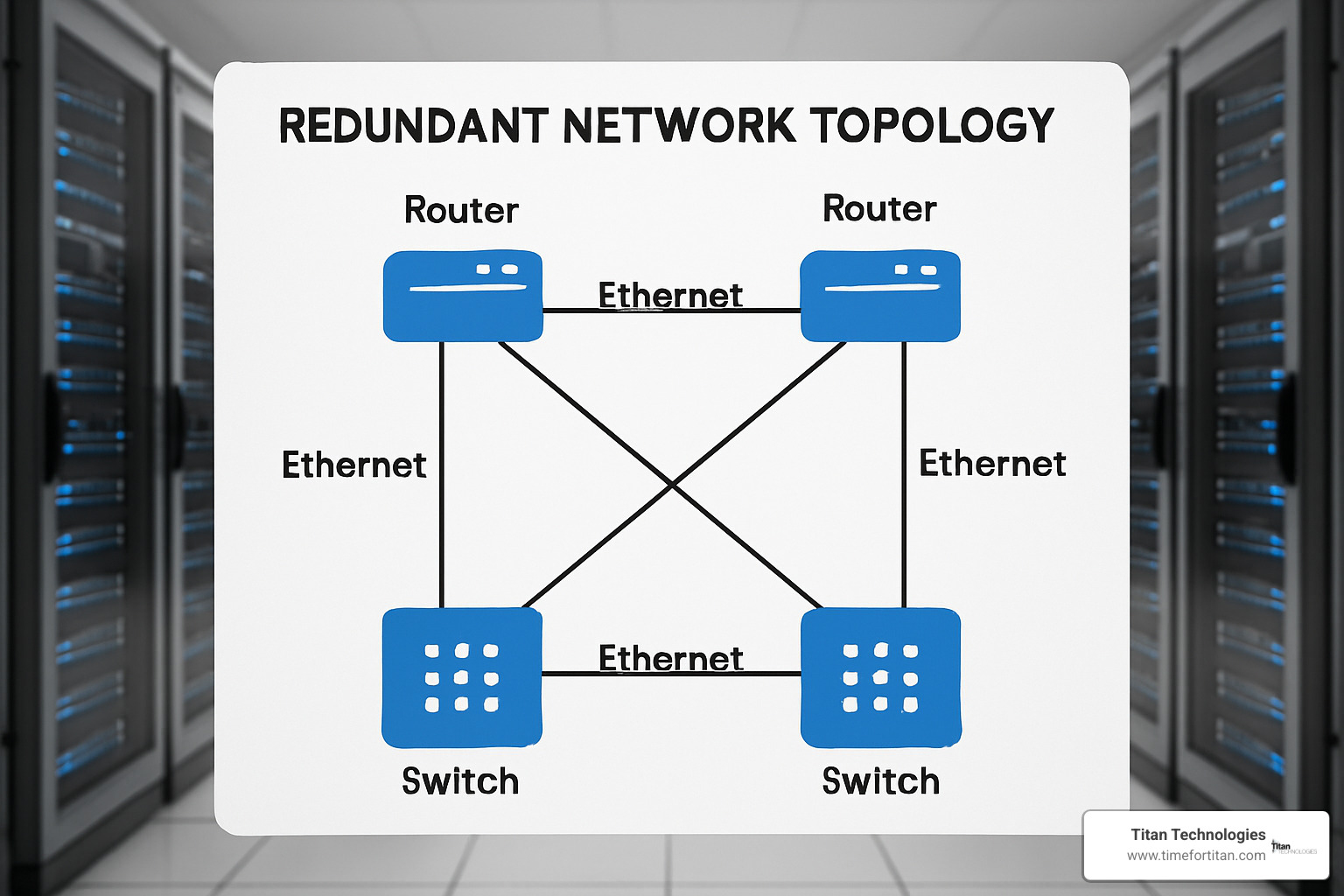
High availability requires redundant network paths, automatic failover mechanisms, and careful capacity planning. The OS must be configured to detect failures quickly and switch to backup systems seamlessly. This requires sophisticated monitoring and automated response capabilities.
Documentation is often overlooked but critically important for effective network management. The research shows that 56% of IT professionals have incomplete knowledge of how their networks are configured. Comprehensive documentation of network configurations, procedures, and troubleshooting guides is essential for maintaining reliable networks.
Skill gaps represent a significant challenge, with many organizations struggling to find qualified network administrators who understand both traditional networking and modern cloud-native approaches. This makes automation and intelligent management systems even more important.
Multi-vendor environments add complexity, as different vendors implement standards differently and may not interoperate perfectly. The OS must handle these differences gracefully and provide unified management interfaces.
Cloud-edge integration creates new challenges as networks span from on-premises data centers to public clouds to edge computing devices. Network management in operating system environments must handle this complexity while maintaining security and performance.
Building for resilience and compliance
Resilience in network management in operating system environments requires multiple layers of redundancy and automated recovery mechanisms. Backup network paths must be pre-configured and regularly tested to ensure they work when needed. The OS should automatically detect path failures and switch to backup routes without interrupting network services.
Compliance requirements are increasingly built into network management systems, with automated audit trails, configuration validation, and reporting capabilities. The OS must maintain detailed logs of all network activities and configuration changes to support compliance audits.
Service Level Agreement (SLA) metrics must be continuously monitored and reported. The OS should track availability, performance, and security metrics that align with business requirements and contractual obligations. Automated alerting ensures that SLA violations are detected and addressed quickly.
Regular backup and recovery testing ensures that network configurations can be quickly restored after failures or security incidents. The OS should support automated backup of network configurations and rapid restoration procedures.
Bridging peer-to-peer vs client-server models
Modern network management in operating system environments often need to support both peer-to-peer and client-server networking models simultaneously. Workgroup environments may use peer-to-peer networking for simplicity, while domain environments require centralized directory services and policy management.
Directory services provide centralized user and resource management in client-server environments. The OS must integrate with these services to provide single sign-on, centralized policy enforcement, and unified resource access.
Hybrid environments that combine both models require careful planning to ensure security and manageability. The OS must handle different authentication mechanisms, access controls, and resource sharing models within the same network.
Migration strategies from peer-to-peer to client-server models (or vice versa) require careful planning and testing. The OS must support gradual migration approaches that minimize disruption to business operations.
Frequently Asked Questions about Network Management in Operating Systems
What separates a network OS from a general-purpose OS today?
Here’s something that might surprise you: the line between network operating systems and regular operating systems has become incredibly blurry. Back in the day, you had clear distinctions—your Windows or Linux desktop was one thing, and specialized network gear ran completely different software.
Today’s reality is much more interesting. Modern operating systems like Windows Server, Linux distributions, and even macOS have network management in operating system capabilities built right into their core. They’re not afterthoughts or add-ons anymore—they’re fundamental features that handle everything from traffic shaping to security policies.
But specialized network operating systems haven’t disappeared entirely. You’ll still find them running on dedicated hardware like enterprise routers, switches, and security appliances. These systems are laser-focused on specific tasks and often include real-time processing capabilities that general-purpose systems can’t match.
The main difference comes down to optimization and focus. A specialized network OS might handle millions of packets per second with microsecond precision, while a general-purpose OS excels at running your business applications while simultaneously managing complex network operations.
Most businesses end up using both approaches. Your servers and workstations run general-purpose operating systems with robust network management in operating system features, while your core network infrastructure might use specialized systems for maximum performance and reliability.
Which OS-level tools help troubleshoot latency spikes fastest?
When network performance goes sideways and users start complaining about slowdowns, you need tools that give you answers fast. The good news is that modern operating systems come packed with diagnostic capabilities that can pinpoint latency issues quickly.
Start with network interface statistics—they’re your first line of defense. On Linux systems, ip -s link shows you immediately if you’re dealing with packet loss or hardware errors. Windows administrators can use Get-NetAdapterStatistics in PowerShell for similar insights. These tools tell you if the problem is happening right at the network card level.
Real-time packet capture is where things get interesting. Tools like tcpdump on Linux or Wireshark on any platform let you see exactly what’s happening with your network traffic. You can quickly identify whether latency is coming from network congestion, slow DNS lookups, or application-level delays.
Don’t forget about system resource monitoring. Sometimes what looks like a network problem is actually your server running out of CPU or memory. Tools like top and iostat on Linux, or Performance Monitor on Windows, can reveal if system resources are the real culprit.
Network path analysis tools like traceroute or Windows’ pathping are invaluable for identifying where latency is being introduced. Is it your local network? Your internet provider? The destination server? These tools map out the entire path and show you exactly where delays are happening.
Modern network management in operating system environments also include built-in performance counters that can help you spot trends before they become user-visible problems. The key is knowing which tools to reach for when trouble strikes.
How does automation reduce OPEX without compromising security?
This is the million-dollar question that keeps IT directors awake at night. The short answer? Automation eliminates the human errors that cause most network problems while actually improving security—when it’s done right.
Consider this sobering statistic: more than 50% of network outages happen because someone made a configuration mistake. Automation eliminates these errors by ensuring that network changes are implemented consistently, according to predefined security policies, every single time.
Automated configuration management is a game-changer for network management in operating system environments. Instead of manually configuring dozens or hundreds of devices (and inevitably making mistakes), automation tools apply configurations that have been tested and validated. This means fewer security vulnerabilities and dramatically reduced labor costs.
Monitoring and alerting automation works around the clock, detecting threats and performance issues faster than any human team could. While your security team sleeps, automated systems are watching for suspicious activity and can respond to threats in seconds rather than hours.
Patch management automation might be the biggest security win of all. Keeping network devices updated with security patches is critical but incredibly time-consuming when done manually. Automation ensures patches are applied consistently and promptly across your entire infrastructure.
The security key is implementing automation thoughtfully. You need proper access controls, comprehensive audit trails, and human oversight for complex decisions. The goal isn’t to replace human judgment—it’s to free up your skilled staff to focus on strategic work while automation handles the routine tasks that cause most problems.
At Titan Technologies, we’ve seen how properly implemented automation can cut operational costs by 30-40% while actually improving security posture. The secret is starting with well-understood processes and gradually expanding automation as your team gains confidence and expertise.
Conclusion
The journey through network management in operating system environments reveals just how far we’ve come—and how critical these systems have become to modern business success. Your operating system isn’t just running programs anymore; it’s orchestrating a complex symphony of network connections, security policies, and performance optimizations that happen thousands of times every second.
The reality check is sobering: network downtime can cost businesses anywhere from thousands to millions of dollars per hour. When you add the fact that 56% of IT professionals don’t fully understand their own network configurations, it becomes clear that effective OS-level network management isn’t just nice to have—it’s absolutely essential for survival in today’s digital landscape.
Here’s where things get personal. I’ve been in your shoes, watching businesses struggle with network complexity while trying to focus on what they do best. That’s exactly why we built Titan Technologies the way we did. We don’t just understand network management in operating system environments—we live and breathe them every day.
Our approach is refreshingly straightforward. We handle the technical complexity so you don’t have to. Whether you’re wrestling with legacy peer-to-peer networks that seemed like a good idea ten years ago, managing modern client-server environments, or navigating the brave new world of hybrid cloud infrastructures, we’ve got the experience to make it all work seamlessly.
What sets us apart is our proactive mindset. We’re not waiting for problems to happen—we’re identifying and fixing issues before they ever touch your business operations. Our 100% satisfaction guarantee isn’t just marketing speak; it’s how we’ve built our reputation across Central New Jersey, from the busy corridors of Edison and Elizabeth to the innovation hubs of Princeton and Red Bank.
The technology landscape keeps evolving, and frankly, it’s not slowing down. That’s why our team stays ahead of the curve with the latest developments in network automation, AI-driven management, and security protocols. Your network management in operating system capabilities should grow with your business, not hold it back.
Don’t let network management complexity become the bottleneck that limits your growth. The businesses that thrive are the ones that recognize when to bring in specialists who can handle the technical heavy lifting while they focus on serving customers and growing revenue.
Ready to transform your network from a source of stress into a competitive advantage? Let’s talk about how our comprehensive approach to OS-level network management can boost your reliability, tighten your security, and improve your performance—all while reducing those operational headaches that keep you up at night.
For complete details about how we can optimize your network infrastructure, check out our Desktop & Network Support services and see what’s possible when network management is done right.