Safeguarding Your Digital Assets
In today’s digital landscape, your business data is like gold – incredibly valuable and, unfortunately, increasingly targeted. That’s where a solid data protection plan comes into play.
A data protection plan is more than just a document – it’s your comprehensive strategy for safeguarding what matters most. Think of it as your business’s security blueprint, combining policies, procedures, and technical safeguards that work together to keep your sensitive information secure from loss, corruption, and unauthorized access.
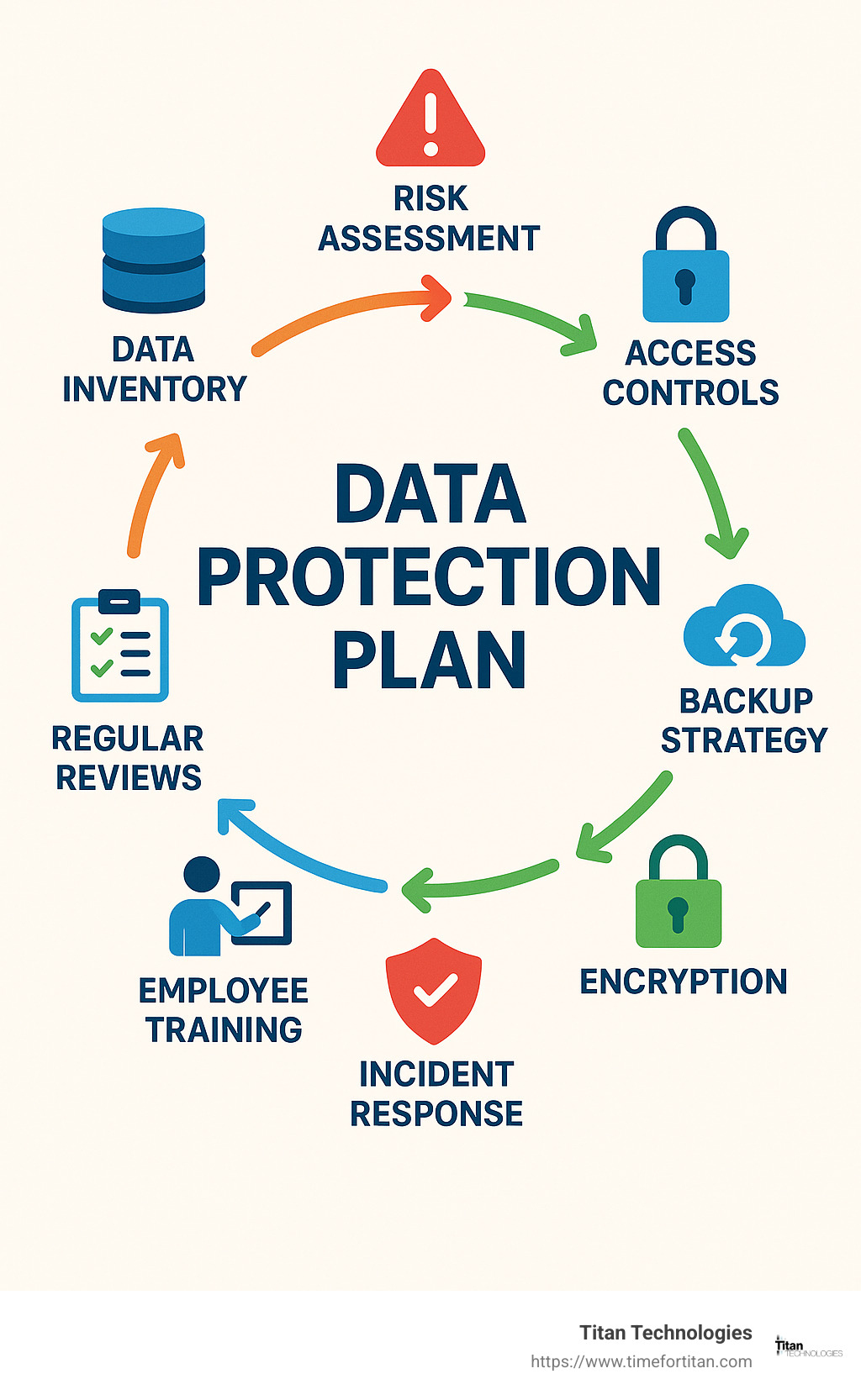
Creating an effective data protection plan doesn’t have to be overwhelming. At its core, you’ll need to identify and classify all your sensitive data through a thorough data inventory. This foundation allows you to conduct a meaningful risk assessment to understand what you’re up against. From there, implementing proper access controls ensures only the right people can reach sensitive information.
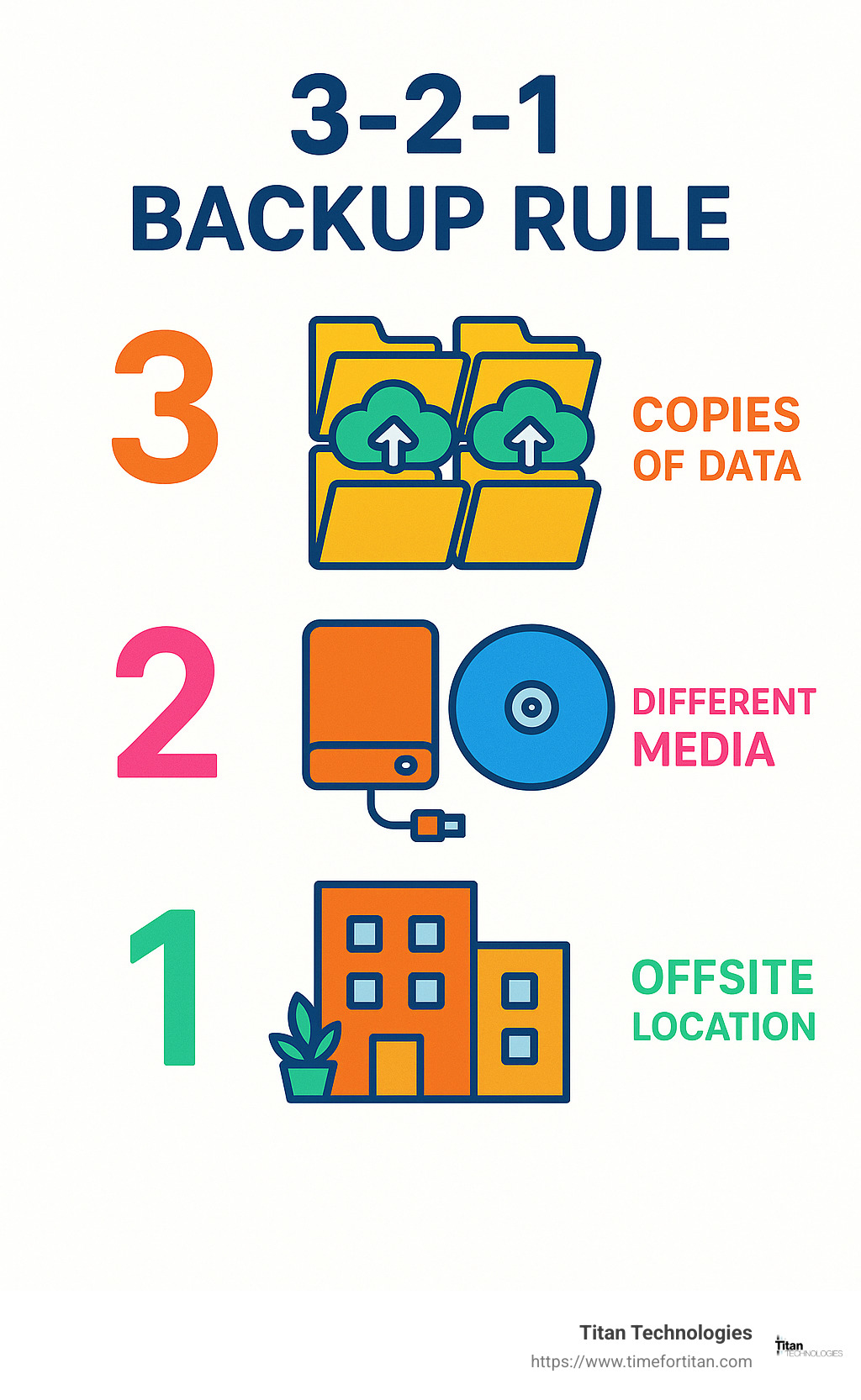
Your plan should include a robust backup strategy – we recommend following the 3-2-1 rule: maintain 3 copies of your data, on 2 different types of media, with 1 copy stored offsite. This approach dramatically reduces your risk of catastrophic data loss. Don’t forget about encryption for both data at rest and in transit – it’s like putting your information in an unbreakable safe.
Even the best defenses can be tested, which is why a clear incident response procedure is crucial. When (not if) something happens, you’ll know exactly what steps to take. Regular employee training transforms your team from a potential vulnerability into your first line of defense. Finally, schedule regular reviews to keep your plan current as threats and technologies evolve.
The stakes couldn’t be higher. With data breaches costing organizations an average of $4.35 million globally according to IBM’s 2022 Cost of a Data Breach Report, small and medium-sized businesses simply can’t afford to be caught unprepared. Every day, businesses collectively generate about 2.5 quintillion bytes of data – creating an enormous target for cybercriminals.
For New Jersey businesses in particular, the challenge is twofold: protecting customer information while navigating an increasingly complex regulatory landscape. A well-crafted data protection plan addresses both concerns while ensuring your business can maintain continuity when incidents occur.
Whether you’re concerned about ransomware attacks, accidental data loss, or regulatory penalties, your data protection plan serves as your roadmap to security success. It’s not just about avoiding problems – it’s about changing data protection from a technical burden into a genuine business advantage that builds customer trust and demonstrates your commitment to data integrity.
Looking to dive deeper? We’ve simplified some key data protection plan concepts through these resources:
– data privacy solutions
– data protection governance risk management and compliance
– data protection security controls
When it comes to protecting your digital assets, being proactive isn’t just smart – it’s essential for your business’s future.
Understanding the Data Protection Plan Landscape
A data protection plan is an organized, systematic approach that encompasses all measures implemented to protect an organization’s data. It goes beyond simple backup procedures to include comprehensive policies, technical controls, and operational practices designed to safeguard information throughout its entire lifecycle.
At its core, a data protection plan follows the CIA triad principles:
– Confidentiality: Ensuring data is accessible only to authorized users
– Integrity: Maintaining data accuracy and completeness
– Availability: Guaranteeing reliable access to information when needed
It’s important to distinguish between related but distinct concepts. Data protection focuses on safeguarding data from loss, corruption, and ensuring its availability. Data security concentrates on defending data against unauthorized access and threats. Data privacy concerns the proper handling, processing, and storage of personal information.
The urgency for robust data protection has never been greater. According to Gartner research, by 2024, 75% of the world’s population will have their personal data covered under modern privacy regulations. This regulatory landscape creates both compliance challenges and opportunities for businesses to differentiate themselves through strong data governance.
For businesses looking to dive deeper into this topic, we recommend checking out our detailed guide on data protection and management. If you’re interested in the financial impact of data breaches, this scientific research on breach costs provides valuable insights.
Why a data protection plan matters
The importance of a comprehensive data protection plan extends far beyond technical compliance. Your business stands to gain much more than just security.
Financial protection is a major benefit – downtime costs can range from $10,000 to over $5 million per hour depending on your organization’s size. When your systems are down, every minute counts against your bottom line. A solid protection plan minimizes these risks by ensuring quick recovery.
Trust and reputation form the foundation of customer relationships. When you handle data properly, customers feel secure doing business with you. One data breach can shatter years of carefully built trust in minutes. We’ve seen clients rebuild their reputation after breaches, and it’s always harder than preventing the problem in the first place.
Having robust data protection can actually give you a competitive edge. When customers are choosing between similar services, knowing their sensitive information is in safe hands often tips the scale. It’s a powerful differentiator that smart businesses leverage in their marketing.
The consequences of non-compliance with regulations are severe. In May 2023, Meta faced a record €1.3 billion GDPR fine for improper data transfers. Even for smaller businesses in New Jersey, penalties can be devastating to your operations and future.
One of our clients, a healthcare provider in Princeton, NJ, experienced this firsthand. After implementing a comprehensive data protection plan, they were able to recover from a ransomware attempt within hours rather than days, maintaining patient care without interruption.
“It is a comfort knowing that preventive IT solutions are always working behind the scene,” shares the CEO of an emergency medical products supplier we work with in Central New Jersey.
Key regulations shaping plans
A robust data protection plan must account for various regulatory frameworks, especially for businesses operating in New Jersey. Understanding these regulations isn’t just about avoiding fines – it’s about building data practices that respect your customers and protect your business.
GDPR (General Data Protection Regulation) applies to any organization handling EU citizens’ data, which might include your New Jersey business if you have international customers or website visitors. It requires explicit consent for data collection and includes the “right to be forgotten” and data portability. Violations can result in fines up to €20 million or 4% of annual global turnover, and you must notify authorities of breaches within 72 hours.
Healthcare providers need to pay special attention to HIPAA (Health Insurance Portability and Accountability Act). This regulation requires technical, physical, and administrative safeguards for patient data. Your data protection plan needs specific provisions for backup procedures, access controls, and audit requirements. Penalties range from $100 to $50,000 per violation with a $1.5 million annual maximum – costs that few small practices can absorb.
Even if you don’t think you serve California customers, the CCPA (California Consumer Privacy Act) and CPRA (California Privacy Rights Act) might still affect your New Jersey business. These laws grant consumers rights to know about, delete, and opt-out of the sale of their personal information. Many of our clients have found California residents in their databases, requiring them to implement specific privacy notices and response mechanisms.
Closer to home, New Jersey Data Protection Laws include the Identity Theft Prevention Act, which requires proper disposal of records, and the New Jersey Security Breach Disclosure Act, mandating notification of breaches. There are also specific data encryption requirements for certain sensitive information.
For businesses in specific New Jersey locations like Edison, Elizabeth, or Newark, additional municipal regulations may apply, particularly for government contractors or healthcare providers.
“Organizations need to go further than simply complying with regulations like GDPR and CCPA,” advises our data protection team. “A proactive stance on data protection will set businesses apart and boost credibility.”
Building Your Data Protection Plan: Step-by-Step Blueprint
Creating a comprehensive data protection plan doesn’t have to be overwhelming when you follow a structured approach. Think of it as building a house—you need a solid foundation, sturdy walls, and a reliable roof to keep everything safe inside.
At its core, effective data protection begins with thorough data mapping. This means understanding exactly what information you have, where it lives in your systems, and how it moves through your organization. This visibility gives you the power to properly classify your data based on its sensitivity and value, which then shapes your protection strategies.
One of the most trusted approaches in the industry is the 3-2-1 backup rule, which we recommend to all our clients:
“Following the 3-2-1 backup rule is one of the best ways to ensure your data remains available even after a catastrophic event,” explains our data protection specialists at Titan Technologies.
Your data protection plan needs to go beyond just backups, though. You’ll want to address encryption for data both at rest and in transit, develop clear incident response procedures for when (not if) breaches occur, and maintain thorough documentation of all your policies and controls.
This plan isn’t something you create once and file away. It’s a living document that needs regular updates as your business grows and the threat landscape evolves. For New Jersey businesses in areas like Trenton, Princeton, or New Brunswick, we recommend tailoring your approach to address specific regional considerations, such as natural disaster risks and local compliance requirements.
Step 1 – Identify & Categorize Sensitive Data
The foundation of any effective data protection plan starts with knowing exactly what data you have and how sensitive it is. Think of it as taking inventory of your valuables before buying home insurance—you need to know what you’re protecting.
Start by creating a comprehensive data inventory. Walk through your digital environment and identify all your data repositories—databases, file shares, cloud storage, email systems, and any other places where information lives. Document what types of data are stored in each location, map how data flows between systems, and identify who owns and manages each data set.
Once you’ve cataloged your data assets, it’s time to implement a classification system. Not all data is created equal, and your protection efforts should reflect that reality. A typical classification system might include levels like Public (marketing materials, public reports), Internal (employee directories, non-sensitive emails), Confidential (customer records, intellectual property), and Restricted (payment data, health information, credentials).
When classifying your data, consider the CIA triad principles that form the backbone of information security:
Confidentiality: Would unauthorized disclosure harm individuals or your organization?
Integrity: Would unauthorized changes impact your operations or decisions?
Availability: Would being unable to access this data disrupt critical business functions?
“Taking inventory of sensitive data across on-premise and cloud systems is essential before you can properly protect it,” notes our security specialists. “You can’t protect what you don’t know you have.”
For businesses in areas like Matawan or Woodbridge, we’ve found that industry-specific classification schemes may be necessary, particularly for those in healthcare, financial services, or government contracting.
For more comprehensive guidance on data governance frameworks, see our resource on Data Protection Governance.
Step 2 – Assess Risks & Threats
With your data identified and classified, the next critical step in your data protection plan is understanding what you’re protecting it from. A thorough risk assessment helps you understand the specific threats your organization faces and prioritize your protection efforts where they matter most.
The threat landscape is constantly evolving, but several key concerns remain persistent. Ransomware and malware attacks continue to grow in sophistication, with attackers now targeting backup systems to prevent recovery. In 2021 alone, there were 1,767 reported breaches worldwide, exposing a staggering 18.8 billion records.
Don’t overlook insider threats either. Whether malicious or accidental, employee actions represent a significant risk to your data. This could include unauthorized access, improper data handling, or falling victim to social engineering attacks like phishing.
For businesses in coastal New Jersey areas like Red Bank, physical threats including natural disasters, power outages, hardware failures, and theft should be part of your planning. Hurricane preparedness isn’t just good business practice—it’s essential for data protection.
Your data protection plan should also account for third-party risks. Vendors and partners with access to your systems may introduce vulnerabilities outside your direct control, as many major breaches have demonstrated in recent years.
The threat modeling process doesn’t need to be overly complex. Start with your data inventory from Step 1, create a threat profile specific to your business, assess your current vulnerabilities, calculate risk levels by combining threat likelihood with potential impact, and then prioritize your mitigation efforts on high-risk, high-impact scenarios first.
“A risk-based approach to data protection ensures you’re investing resources where they’ll have the greatest impact,” explains our security team. “Not all data requires the same level of protection.”
For businesses in areas like Freehold or Lakewood, we recommend industry-specific threat assessments that account for your particular business model and customer base.
Risk assessment isn’t a one-time activity but should be performed regularly as part of your ongoing data protection plan maintenance. As threats evolve, so should your protective measures.
Step 3 – Define Access Management & Encryption Controls
With your data classified and risks identified, it’s time to build the walls and locks of your data protection plan. Access controls and encryption form the backbone of your technical safeguards—they determine who can see your data and ensure it remains protected even if your perimeter is breached.
Access management starts with the least privilege principle—giving users only the minimum access necessary to do their jobs. Think of it as giving employees keys only to the rooms they need, rather than a master key to the entire building. This simple approach significantly reduces the potential damage from compromised accounts.
Multi-factor authentication (MFA) adds another critical layer of protection. By requiring something you know (password) and something you have (like a phone app), MFA has been shown to prevent 99.9% of automated attacks. For any system containing sensitive data, MFA should be non-negotiable.
Many organizations find success with role-based access control (RBAC), which assigns permissions based on job roles rather than individual users. This approach simplifies management, reduces errors, and makes it easier to maintain appropriate access levels as employees change positions.
Don’t set access controls once and forget them. Regular access reviews should be conducted quarterly to identify and remove unnecessary permissions, particularly after role changes or employee departures. Lingering access rights are a common security gap in many organizations.
Encryption provides protection that follows your data wherever it goes. Data-at-rest encryption protects stored information using strong algorithms (AES-256 or better), covering databases, file systems, and endpoint devices. Meanwhile, data-in-transit encryption secures information as it moves across networks using TLS 1.2+ for web traffic, VPNs for remote access, and encrypted file transfer protocols.
“Managing data access is one of the best ways to ensure data protection,” notes our security team. “Combined with strong encryption, these controls form your first line of defense against both external and internal threats.”
For businesses in Newark or Elizabeth with remote workers, we recommend additional controls specific to securing distributed workforces, such as conditional access policies and secure remote desktop solutions.
For more detailed guidance on implementing encryption effectively, see this scientific research on encryption safeguards which provides valuable insights on implementation best practices.
Step 4 – Plan Backup & Recovery
Even with the best preventive measures, incidents will occur. That’s why a robust backup and recovery strategy forms the cornerstone of any effective data protection plan. Your ability to recover quickly can mean the difference between a minor hiccup and a business-ending catastrophe.
Start by defining your recovery objectives. Recovery Point Objective (RPO) determines how much data loss your business can tolerate and drives your backup frequency. For mission-critical systems, this might be as little as 15 minutes to 1 hour, while less important systems might tolerate 24 hours of data loss.
Similarly, your Recovery Time Objective (RTO) defines how quickly systems must be restored after an incident. Critical systems might need to be back online within minutes or hours, while non-essential systems could potentially wait 24-48 hours without significant business impact.
Immutable backups have become increasingly important in today’s threat landscape. These are backup copies that cannot be altered or deleted, even by administrators. With ransomware now specifically targeting backup systems, immutability provides an essential safety net when all other defenses fail.
Snapshot technology offers another powerful recovery tool by creating point-in-time recovery options. This allows you to roll back to a specific moment before corruption or deletion occurred, giving you more flexibility than traditional backup methods alone.
Don’t forget the geographic component of your backup strategy. Following the 3-2-1 rule means maintaining copies in geographically separate locations to protect against regional disasters—particularly important for businesses in areas like Princeton or Trenton where severe weather events can affect entire regions simultaneously.
“Backup redundancies are key when it comes to maintaining continuity in business operations,” explains our data protection specialists. “Automated ‘set and forget’ solutions remove human error from backups.”
One of our retail clients in Woodbridge experienced this benefit when their POS system crashed during peak business hours. Thanks to their well-structured backup and recovery plan, we restored operations while customers waited, preventing significant revenue loss and reputational damage.
The final—and often overlooked—component of backup planning is regular testing. Monthly recovery drills verify that your backups are functional and that your team knows how to use them in a crisis. There’s nothing worse than finding your backup system has been failing silently when you need it most.
For comprehensive backup and recovery solutions custom to your specific business needs, explore our Business Disaster Recovery (BDR) services.
Step 5 – Integrate Data Lifecycle Management
A complete data protection plan must address how data is managed from birth to retirement. Data lifecycle management ensures you’re not only protecting information while it’s active but also handling it appropriately as it ages—much like how we care for important documents throughout our lives.
Start by establishing clear retention schedules that specify how long different data types should be kept. These timeframes should be based on legal and regulatory requirements (like the 7-year retention period for financial records), business operational needs, industry best practices, and a careful balancing of storage costs against potential risks.
When data reaches the end of its useful life, secure disposal becomes critical. For digital media, this means using Department of Defense-standard wiping methods or physical destruction. Physical documents require shredding or incineration. For cloud data, ensure complete removal from all storage locations, including backups and archives. Improper disposal of sensitive information can lead to breaches just as devastating as active attacks.
Not all outdated data needs to be destroyed immediately. Archiving strategies help you move inactive but necessary data to cost-effective, secure long-term storage. Be sure to compress and encrypt archived data, maintain searchability for legal findy needs, and ensure archived information remains accessible when needed.
To make this process manageable, leverage automation tools that enforce lifecycle policies without constant manual intervention. Content classification engines, policy-based retention management, and scheduled archiving and deletion workflows can dramatically reduce the administrative burden while improving compliance.
“Some regulations require data to be destroyed after a defined retention period,” notes our compliance team. “An effective lifecycle management system ensures you’re not keeping data longer than necessary, which reduces both risk and storage costs.”
For businesses in regulated industries in areas like Newark or New Brunswick, we recommend industry-specific lifecycle management procedures that align with your compliance requirements.
A practical example comes from a law firm client in Princeton who implemented automated classification and retention policies. This reduced their storage costs by 40% while simultaneously improving their compliance posture and reducing risk exposure.
By integrating data lifecycle management into your data protection plan, you create a comprehensive approach that addresses data from creation through destruction, ensuring nothing falls through the cracks.
Step 6 – Document, Train & Enforce
The final step in building your data protection plan involves bringing everyone on board. Even the most technically sound plan will fail without proper documentation, understanding, and adherence across your organization.
Start with clear, comprehensive documentation using standardized templates. Your documentation should cover data classification guidelines, access control procedures, backup and recovery processes, incident response playbooks, and acceptable use policies. Make these documents living resources that evolve as your protection strategies mature.
Clearly define who’s responsible for each aspect of data protection. This includes data owners (typically department heads), data custodians (IT and security teams), a data protection officer (if required by regulations), and end users (all employees). When everyone understands their role, gaps in protection are less likely to occur.
Ensure your policies are easily accessible to all employees through intranet portals, employee handbooks, and quick reference guides. The best policy in the world is useless if people don’t know where to find it when they need guidance.
Training brings your data protection plan to life. Provide comprehensive data protection training for all new hires during onboarding, conduct quarterly training updates on evolving threats and procedures, deliver specialized training for employees with access to sensitive data, and run phishing simulations and tabletop exercises to test awareness in real-world scenarios.
“A positive security culture through incident-based user training can increase productivity while reducing data loss risk,” explains our security awareness team. “When employees understand not just what to do but why it matters, compliance improves dramatically.”
Don’t forget about enforcement. Implement systems to verify compliance with policies, establish clear consequences for policy violations, and—importantly—recognize and reward good security practices. Positive reinforcement often drives better results than punitive measures alone.
For businesses in Matawan or Red Bank, we recommend industry-specific training programs that address the unique data protection challenges in your sector.
One of our manufacturing clients in Elizabeth saw a 65% reduction in security incidents after implementing a comprehensive security awareness program that included monthly microlearning sessions and recognition for security champions.
Your data protection plan is a living document that should evolve as your business, technologies, and threats change. Regular reviews and updates ensure your plan remains effective and relevant in protecting your most valuable asset—your data.
Special Considerations: Cloud, Compliance, and Breach Response
The cloud has revolutionized how we store and manage data, but it also introduces unique challenges for your data protection plan. When you migrate to cloud services, you’re entering a partnership with your provider—they secure the infrastructure while you remain responsible for protecting your actual data.
Think of it like renting an apartment. The building owner maintains the structure and common areas, but you’re still responsible for locking your door and safeguarding your valuables inside. This “shared responsibility model” is fundamental to understanding cloud security.
Different cloud services require different levels of your involvement:
With SaaS platforms like Microsoft 365, you’re responsible for configuring access controls and protecting your credentials, but the provider handles most of the underlying security. Move to PaaS or IaaS solutions, and your responsibilities grow significantly—now you’re managing applications, operating systems, and sometimes network controls too.
Another wrinkle in cloud data protection is data sovereignty—the idea that your information is subject to the laws of whatever country it physically resides in. For New Jersey businesses serving customers across state lines or internationally, this means carefully considering where your providers store your data.
“Your data protection framework needs to be extremely elastic and very responsive,” notes Lee Cox, Vice President of Compliance & Research at a major technology company. “The technology we now have is enabling us to rely confidently on data at scale with far more efficiency than we ever did before.”
If you’re like many of our clients in Central New Jersey who use multiple cloud providers, you’ll need a unified approach that maintains consistent protection regardless of where your data lives. The days of having separate security strategies for each environment are long gone.
And don’t forget about breach notification timelines—GDPR’s 72-hour requirement can feel impossibly tight if you don’t have clear incident response procedures already in place. Having prepared playbooks isn’t just good practice; it’s practically essential for regulatory compliance.
Want to dive deeper into cloud-specific protection strategies? Check out our resource on Data Protection Cloud-Based Services.
Cloud-native protection best practices
When it comes to protecting data in the cloud, traditional approaches often fall short. The dynamic, scalable nature of cloud environments requires protection strategies designed specifically for these platforms.
Encryption-at-rest is your first line of defense. While most cloud providers offer encryption by default, how you manage the encryption keys makes all the difference. For everyday business data, provider-managed keys offer simplicity and strong protection. For your crown jewels—customer financial data or intellectual property—consider customer-managed keys that give you greater control.
One of our manufacturing clients in Edison initially used the same encryption approach for all their data. After our review, they implemented tiered encryption based on data sensitivity, dramatically improving both security and performance.
Cloud Security Posture Management (CSPM) tools have become essential components of a modern data protection plan. These solutions continuously monitor your cloud configurations against best practices and can automatically remediate common misconfigurations. Think of CSPM as having a security expert constantly checking your work and fixing small mistakes before they become big problems.
“Technology is evolving, but the threats are also growing exponentially,” cautions Mehdi Charafeddine, a distinguished engineer at a major technology company. “Fortunately, there are more and more sophisticated ways to apply data protection and support data privacy.”
Vendor assessment isn’t a one-time activity when selecting a cloud provider—it should be ongoing. Review your providers’ security certifications annually, understand their backup capabilities, and verify their data deletion practices. We’ve seen too many businesses in Princeton and Trenton assume their providers handle everything, only to find gaps during an incident.
For organizations with hybrid environments—a common scenario in New Jersey’s pharmaceutical and financial sectors—consistency is key. Your on-premises and cloud security controls should work together seamlessly, ideally managed through unified tools and centralized identity management.
Cloud environments evolve rapidly. A data protection plan that perfectly addresses today’s cloud landscape may need significant updates next year as providers introduce new features and security capabilities.
Aligning with global & state regulations
Creating a data protection plan that satisfies the patchwork of regulations facing today’s businesses can feel like trying to solve a puzzle with constantly changing pieces. From GDPR to CCPA to New Jersey’s own data protection laws, compliance requires both technical controls and organizational processes.
Regular audits and assessments form the backbone of regulatory compliance. We recommend quarterly internal reviews to catch issues early, complemented by annual third-party assessments for an unbiased perspective. For our healthcare clients in New Brunswick, these regular checkups have proven invaluable for maintaining HIPAA compliance while adapting to new technologies.
Data Protection Impact Assessments (DPIAs) might sound like bureaucratic paperwork, but they’re actually powerful tools for identifying privacy risks before they become problems. By systematically analyzing how new initiatives might affect individual privacy, you can make smart adjustments early in the process rather than expensive fixes later.
A financial services client in Princeton initially viewed DPIAs as a compliance burden until they realized these assessments were uncovering valuable insights about their data handling practices. Now they conduct them for all new projects, not just those required by regulations.
Comprehensive record-keeping isn’t glamorous, but it’s essential when regulators come knocking. Documenting your data flows, consent mechanisms, and responses to data subject requests creates an audit trail that demonstrates your commitment to compliance. As one of our clients humorously put it, “In the eyes of regulators, if you didn’t document it, it didn’t happen.”
“Privacy is part of a competitive advantage story that touches on practices across our company and contributes directly to revenue,” notes Christina Montgomery, Chief Privacy Officer at a major technology company. This perspective reflects what we’re seeing among forward-thinking businesses throughout Central New Jersey—compliance isn’t just about avoiding penalties; it’s becoming a business differentiator.
For businesses operating across multiple jurisdictions, we recommend creating a regulatory matrix that maps your obligations by location. Many of our clients in Edison and Elizabeth find it simplest to implement the strictest requirements across all their operations rather than maintaining different standards for different customers.
Your data protection plan should include a process for monitoring regulatory changes. With privacy laws evolving rapidly, staying current isn’t optional—it’s essential for maintaining compliance.
Breach prevention & incident response
Even the most robust data protection plan can’t guarantee you’ll never experience a security incident. The reality is that most organizations will face some form of breach attempt—what separates the success stories from the cautionary tales is how quickly and effectively they respond.
Monitoring and detection capabilities form your early warning system. Implementing a Security Information and Event Management (SIEM) solution gives you visibility across your environment by centralizing logs and alerting on suspicious activities. One of our retail clients in Woodbridge initially resisted this investment until a small breach went undetected for weeks. Now they consider their SIEM indispensable.
User and Entity Behavior Analytics (UEBA) adds another layer of protection by identifying when users are acting outside their normal patterns. This technology has proven particularly valuable for detecting compromised accounts—often before the attackers can cause significant damage.
Beyond technology, vulnerability management must be an ongoing process. Regular scanning, prioritized remediation, and consistent patch management might not be exciting, but they prevent the vast majority of successful attacks. As we often tell our clients in Matawan and surrounding areas: “Basic security hygiene beats flashy security tools every time.”
When it comes to incident response, preparation makes all the difference. Detailed playbooks for common scenarios ensure your team knows exactly what to do when minutes count. These should clearly define roles, communication channels, and decision-making authority—because during a crisis, confusion can be as damaging as the attack itself.
“Organizations with mature incident response capabilities incur on average $1.49 million less per breach and resolve incidents 54 days faster,” according to recent industry research. We’ve seen this play out with our own clients—those with well-rehearsed response plans consistently experience less downtime and lower recovery costs.
Tabletop exercises might feel like role-playing games, but they’re serious business. By simulating breach scenarios quarterly, your team builds the muscle memory needed for effective response. A manufacturing client in Trenton credits these exercises with their successful containment of a ransomware attempt—they isolated affected systems and restored from clean backups so quickly that operations barely noticed.
After any security incident, conduct a thorough post-mortem review. This isn’t about assigning blame; it’s about continuous improvement. Document what happened, what worked, what didn’t, and what you’ll do differently next time. Then share these lessons (appropriately anonymized) across your organization.
At Titan Technologies, we’ve helped countless Central New Jersey businesses develop and test their incident response capabilities. We’ve learned that the most resilient organizations view each incident not as a failure but as an opportunity to strengthen their overall security posture.
Monitoring, Measuring, and Evolving Your Data Protection Plan
A data protection plan isn’t something you can set and forget. Like a garden that needs regular tending, your plan requires continuous monitoring, measurement, and evolution to stay effective against new threats and changing business needs. Without proper oversight, even the most sophisticated protection strategies can become outdated and ineffective.
“The most dangerous assumption in cybersecurity is believing yesterday’s protection will be sufficient for tomorrow’s threats,” our security operations team often reminds clients.
Tracking key performance indicators gives you visibility into how well your protection strategies are working. Think of these metrics as your security vital signs – they tell you if your protection is healthy or needs attention:
Recovery Test Pass Rate measures how often your backup restoration tests succeed, giving you confidence your data can be recovered when needed. Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) track how quickly you identify and contain security incidents – critical factors that directly impact breach costs. Data Classification Coverage shows what percentage of your information is properly categorized, while Policy Compliance Rate reveals how well your team follows protection procedures. Finally, Security Control Effectiveness measured through penetration testing tells you if your defenses can withstand real-world attacks.
Measurement isn’t just about compliance checkboxes – it’s about continuous improvement. By tracking these metrics over time, you can spot concerning trends before they become serious problems. It’s like having regular health check-ups instead of waiting until you’re seriously ill.
One of our financial services clients in Red Bank implemented a quarterly protection scorecard that transformed how they managed security. What started as a simple tracking tool evolved into a powerful communication device that helped justify critical security investments to their board. “Having hard data made all the difference in getting buy-in for our security initiatives,” their CIO told us.
For businesses in Princeton or Matawan, we recommend comparing your metrics against industry benchmarks to understand how your protection measures stack up against similar organizations. This context helps prioritize your improvement efforts where they’ll have the greatest impact.
For more detailed guidance on implementing effective security controls, check out our resource on Data Protection Security Controls.
Tools & automation for oversight
Monitoring a modern data protection plan without specialized tools is like trying to steer the ocean without instruments – technically possible but unnecessarily risky. The volume and complexity of today’s data environments simply demand automation to stay on top of potential issues.
Data Loss Prevention (DLP) systems serve as your first line of defense, examining content as it moves through your organization and automatically blocking unauthorized transfers. Think of DLP as a vigilant security guard who checks every package leaving your building for sensitive information. One healthcare client in Newark told us their DLP system prevented at least three significant data breaches in its first year alone by catching employees accidentally sending protected health information via unsecured channels.
User and Entity Behavior Analytics (UEBA) takes a different approach by establishing what “normal” looks like in your environment, then flagging unusual activities that might indicate a breach. It’s like having a security system that doesn’t just detect when windows are broken, but also notices when someone is walking through your house at unusual hours. This technology is particularly valuable for detecting insider threats that might otherwise fly under the radar.
AI-Powered Anomaly Detection represents the cutting edge of protection monitoring, using machine learning to identify subtle patterns that human analysts might miss. “Deploying AI in security monitoring is like adding a team of tireless analysts who never need coffee breaks,” explains our security team. “These systems continuously learn and adapt to new threat patterns, becoming more effective over time.”
The financial impact of these technologies is substantial. According to industry research, organizations with fully deployed security AI and automation experience breach costs averaging $3.05 million less than those without these tools. That’s not just a security benefit – it’s a competitive advantage.
For businesses in Edison or Elizabeth with complex data environments, we recommend implementing integrated security platforms that provide unified visibility across all systems. This comprehensive view eliminates blind spots where threats might hide while streamlining management for your IT team.
When selecting tools for your data protection plan, consider how well they’ll integrate with your existing infrastructure, their ability to grow with your business, customization options for your specific industry requirements, and the total cost of ownership, including ongoing maintenance and training.
Review cadence & governance
Even the best data protection plan will drift from effectiveness without regular reviews and strong governance. Think of these reviews like regular maintenance for your car – they might seem like an inconvenience, but they prevent catastrophic failures down the road.
How often should you review your protection measures? It depends on the sensitivity of your data. For your most sensitive information (classified as Restricted), quarterly reviews with your security team, data owners, and compliance officers are essential. Confidential data warrants bi-annual reviews, while Internal and Public information categories can typically be reviewed annually.
Creating a Data Protection Steering Committee brings structure and accountability to your governance efforts. This committee should include executive sponsorship to ensure resources and attention, plus representatives from IT, Legal, Compliance, and key business units. Meeting quarterly, this group reviews protection metrics, approves policy changes, and allocates resources where needed.
“In my experience, organizations that treat data protection as an afterthought inevitably experience preventable incidents,” shares one of our senior security consultants. “The difference between companies that weather breaches well and those that suffer catastrophic damage often comes down to governance structures established long before any incident occurs.”
Your annual strategy refresh provides an opportunity to step back and evaluate your overall protection approach. This comprehensive review should include a gap analysis against current threats and regulations, alignment with your technology roadmap, and resource planning for the coming year. Think of it as your protection program’s yearly physical – a chance to identify health issues before they become serious.
Documentation management might sound boring, but it’s crucial for maintaining an effective data protection plan. Version control for all protection policies, scheduled review workflows, and accessibility of current documents ensure everyone follows the same playbook. When an incident occurs at 2 AM, you don’t want your response team hunting through email for the latest procedures.
A law firm in Princeton transformed their security posture by implementing quarterly data protection reviews. “Before establishing regular reviews, our security was reactive and inconsistent,” their IT director told us. “Now we systematically address gaps before they become problems, and our team has a much clearer understanding of protection priorities.”
For businesses in Trenton or Freehold, we recommend integrating data protection reviews into existing governance structures rather than creating entirely separate processes. This integration ensures protection receives appropriate attention without overwhelming your team with additional meetings.
Governance isn’t just about checking compliance boxes – it’s about creating accountability and ensuring your data protection plan evolves alongside your business and the threat landscape. With proper governance, data protection transforms from a one-time project into a sustainable business practice that provides lasting value.
Frequently Asked Questions about Data Protection Plans
What’s the difference between data protection, data security, and data privacy?
I hear this question all the time from our clients in Central New Jersey, and it’s a great one. These terms get tossed around interchangeably, but they actually serve different purposes within your data protection plan.
Think of it this way: data protection is like ensuring your family photos are safe from floods, fires, and accidental deletion. It’s all about safeguarding information from loss or corruption and making sure it’s available when you need it. This includes your backup procedures, disaster recovery planning, and business continuity measures.
Data security, on the other hand, is more like the locks, alarm system, and security cameras for your home. It focuses on defending your information against unauthorized access and external threats through tools like encryption, access controls, and network security measures.
Then there’s data privacy, which is comparable to the rules you set about who can see your personal photos and what they can do with them. It deals with the proper handling of personal information, addressing consent, transparency, and individual rights regarding how their data is used.
“Most organizations initially focus on security but often overlook the equally important aspects of protection and privacy,” explains our data governance team at Titan Technologies. “A truly comprehensive approach needs all three working in harmony.”
For our clients in Newark and New Brunswick, understanding these distinctions has helped them develop more targeted strategies while maintaining a unified approach to information management.
How often should we test our backups and recovery processes?
Imagine finding your backups don’t work right when you desperately need them after a ransomware attack. It’s a nightmare scenario we’ve helped several Central New Jersey businesses recover from—and one that’s completely avoidable with regular testing.
Your data protection plan should include a testing schedule based on how critical each system is to your operations:
For mission-critical systems (those that would shut down your business if unavailable), we recommend quarterly full recovery tests with monthly spot-checks. These should involve complete restoration to a test environment.
Business-critical systems (important but with some tolerance for downtime) should undergo bi-annual full tests with quarterly spot-checks.
Standard systems can typically manage with annual full tests and bi-annual spot-checks, often just restoring sample files to verify functionality.
Beyond the schedule, there are some golden rules we share with all our clients:
Always test after making significant changes to your systems or backup procedures. The worst time to find a problem is during an actual recovery situation.
Make your tests realistic by simulating actual disaster conditions. If possible, have different team members perform the recovery to ensure the process isn’t dependent on a single person.
“One of our manufacturing clients in Matawan finded during a routine test that their backup system was capturing data but missing configuration files,” shares our recovery specialist. “Had they needed those backups in a real emergency, they would have faced days of additional downtime reconfiguring everything from scratch.”
A backup that can’t be restored isn’t a backup at all—it’s just wasted storage space.
What are the top metrics to prove my data protection plan is effective?
When clients ask how they can be sure their data protection plan is working, I tell them it’s all about measuring the right things. Just like you wouldn’t judge a car’s performance solely by its color, you can’t evaluate your data protection by a single metric.
The most telling metrics fall into three categories:
First, look at your recovery performance. How successful are your recovery tests? Are you meeting your target Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO)? What’s your Mean Time to Recover (MTTR) after an incident? These numbers tell you how quickly you can bounce back when problems occur.
Second, examine your security effectiveness. How long does it take to detect incidents (MTTD) and contain threats (MTTC)? What percentage of your systems have proper protection controls? How quickly are vulnerabilities addressed once identified? These metrics reveal how well you’re preventing and responding to threats.
Finally, assess your compliance and governance. What percentage of your systems adhere to protection policies? How much of your data is properly classified and protected? Are access reviews completed on schedule? Have all staff completed security training? These measurements show how well your policies translate into practice.
“Numbers tell stories,” explains our data protection team at Titan Technologies. “When one of our healthcare clients in Princeton started tracking these metrics, they finded their backup success rate was perfect, but their detection time for unusual access patterns was concerning. This insight allowed them to focus improvements where they were most needed.”
For businesses in Woodbridge and throughout Central New Jersey, we typically recommend starting with just 3-5 key metrics that align with your biggest risks, then expanding measurement as your program matures. The goal isn’t perfect scores across the board, but continuous improvement over time.
Effective measurement isn’t about looking good on paper—it’s about knowing your true protection status so you can sleep better at night knowing your business data is truly secure.
Conclusion
The digital landscape we steer today makes a comprehensive data protection plan not just a nice-to-have but an absolute necessity. As cyber threats grow more sophisticated and regulations tighten, businesses that prioritize data protection position themselves for success while those that neglect it face increasing risks.
Throughout this guide, we’ve walked through the essential components of effective data protection—from carefully mapping and classifying your sensitive information to implementing robust technical controls like encryption and access management. We’ve explored how governance frameworks and continuous monitoring transform data protection from a one-time project into an ongoing business practice that evolves with your needs.
Data protection isn’t something you “finish” and check off your list. It’s a dynamic, living process that requires regular attention as threats evolve and your business grows. The most effective protection comes from creating a culture where everyone understands their role in safeguarding your valuable information assets.
The business case for investing in data protection is compelling. With data breaches now costing organizations an average of $4.35 million, the financial implications alone justify a proactive approach. But beyond the numbers, there’s the invaluable currency of trust—when customers know you take protecting their information seriously, they reward you with loyalty and confidence that no marketing campaign can buy.
For businesses across Central New Jersey—whether you’re operating in Princeton, Newark, Edison, or Red Bank—building and maintaining an effective data protection plan doesn’t have to be a solo journey. Titan Technologies partners with organizations like yours every day, providing the expertise and support needed to steer these complex waters with confidence.
Our professional team understands the unique challenges facing New Jersey businesses, offering swift, dependable support backed by our 100% satisfaction guarantee. We believe that proper data protection isn’t just about avoiding problems—it’s about creating a foundation for growth and innovation where data can be leveraged safely and effectively.
Data is both your most valuable asset and your greatest responsibility. By investing in thoughtful protection now, you’re not just checking a compliance box—you’re creating a genuine competitive advantage that will serve your business well for years to come.
For more information about our comprehensive services and how we can help strengthen your data protection posture, visit our services page.