Understanding Personal Data Protection: Your Privacy Rights Explained
Have you ever wondered what happens to all the information you share online? Every time you create an account, make a purchase, or even just browse the web, you’re creating a digital footprint. Personal data protection is all about keeping that footprint private and secure.
At its heart, personal data protection refers to the safeguards that ensure your personal information stays private, secure, and is used only for legitimate purposes. It’s a combination of legal frameworks and technical measures designed to give you control over your own information.
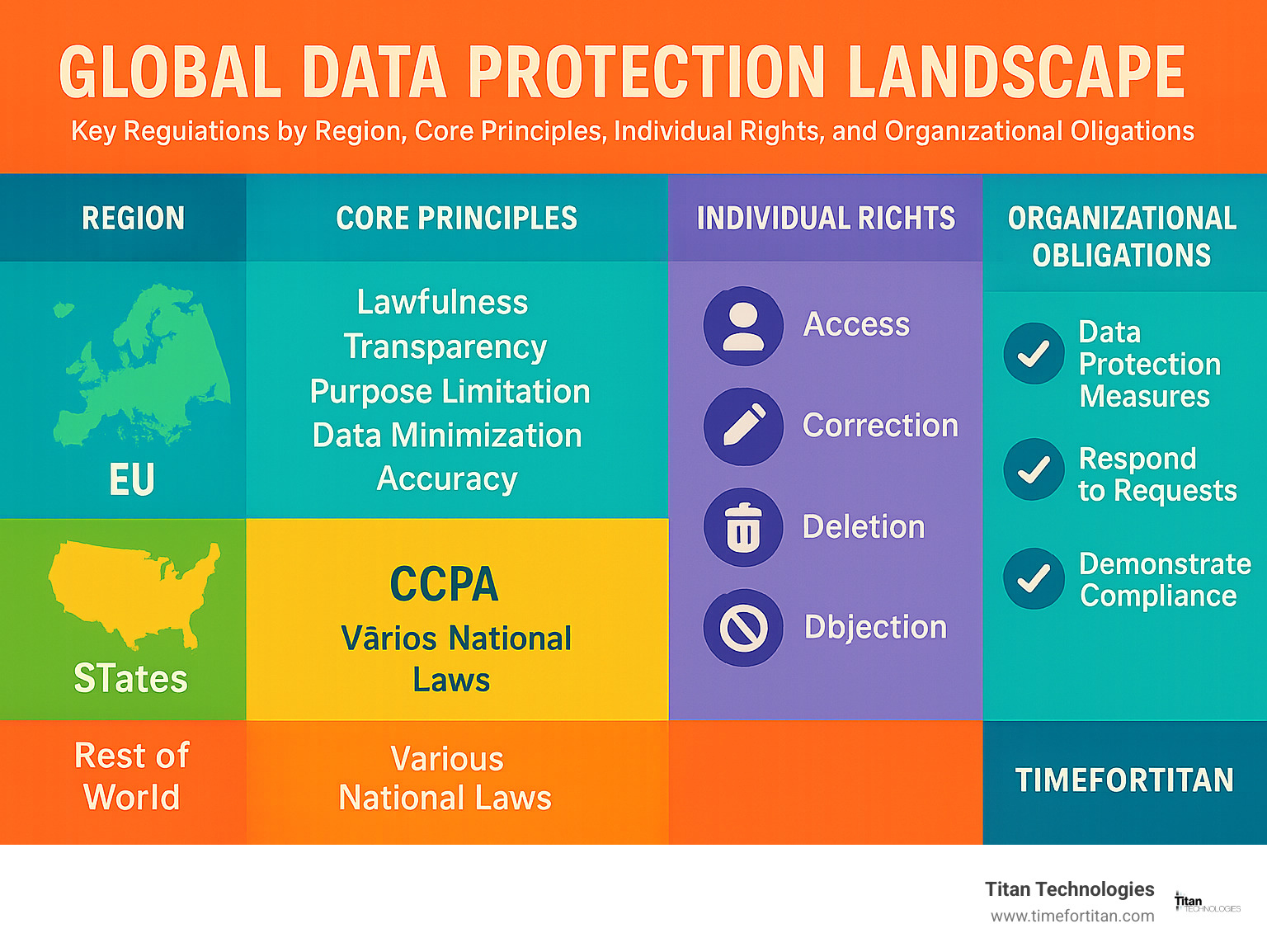
The core principles of good personal data protection are straightforward: lawfulness (data should be collected legally), transparency (you should know what’s happening with your data), purpose limitation (data should only be used for specified reasons), data minimization (only collect what’s needed), accuracy (keep information correct), and security (keep it safe from breaches).
These principles translate into practical rights for you. You should be able to access your data, correct it if it’s wrong, delete it when appropriate, and object to how it’s being processed. These aren’t just nice ideas—they’re legally protected rights in many places around the world.
Speaking of which, personal data protection looks different depending on where you are. The EU has the GDPR, California has the CCPA, and over 120 countries worldwide have their own laws giving individuals control over their information. As of 2024, more than 75% of the world’s population is covered by some form of data protection legislation.
What counts as personal data? It’s broader than you might think. Beyond the obvious identifiers like your name and address, it includes your email, phone number, ID numbers, account information, location data, online identifiers, photos, biometric information, and even your opinions and preferences. Basically, if it can be linked back to you, it’s personal data.
The stakes are high when personal data protection fails. Data breaches can lead to identity theft, financial fraud, or damage to your reputation. Organizations understand this too—in 2023 alone, companies worldwide spent billions updating their privacy policies and practices to comply with evolving laws.
For businesses here in Central New Jersey, navigating this landscape is both challenging and essential. Protecting customer and employee data isn’t just about maintaining trust—it’s also about avoiding hefty penalties. The GDPR has resulted in over €4 billion in fines since 2018, while California consumers made more than 1.4 million data subject requests in 2022 alone.
Want to learn more about personal data protection? Check out these related topics:
– data protection governance risk management and compliance
– data protection plan
– data protection security controls
Why This Guide Matters
We’re living in a data explosion. Every day, humans generate approximately 2.5 quintillion bytes of data—that’s a 2.5 followed by 18 zeros! From your morning social media check to your lunchtime online shopping and evening streaming, you’re constantly creating data about yourself and your habits.
The recent shift to remote work has only complicated matters. When employees use home networks or personal devices for work, the line between personal and professional data blurs. Your company spreadsheet might be sitting on the same laptop as your family photos, creating new security challenges for everyone involved.
Adding to this complexity is the confusing patchwork of regulations. In the U.S., there’s no single comprehensive privacy law. Instead, businesses must steer sector-specific federal regulations alongside different state laws, each with their own unique requirements. It’s like trying to follow different traffic rules every few miles on the same highway.
We’ve seen how Central New Jersey businesses struggle with these challenges. Whether you’re worried about your own privacy or responsible for protecting customer data at your company, understanding personal data protection isn’t optional anymore—it’s essential.
This guide aims to explain these concepts and give you practical steps to protect what matters. Because in today’s digital world, data protection isn’t just a technical issue—it’s about respecting human dignity and rights in the digital age.
What Is Personal Data Protection? Global Definitions & Frameworks
Personal data protection isn’t just a technical term – it’s the shield that guards your digital identity in our connected world. Think of it as the rules, tools, and safeguards that keep your personal information from falling into the wrong hands.
But what exactly counts as “personal data” in the first place? The answer varies depending on where you are in the world.
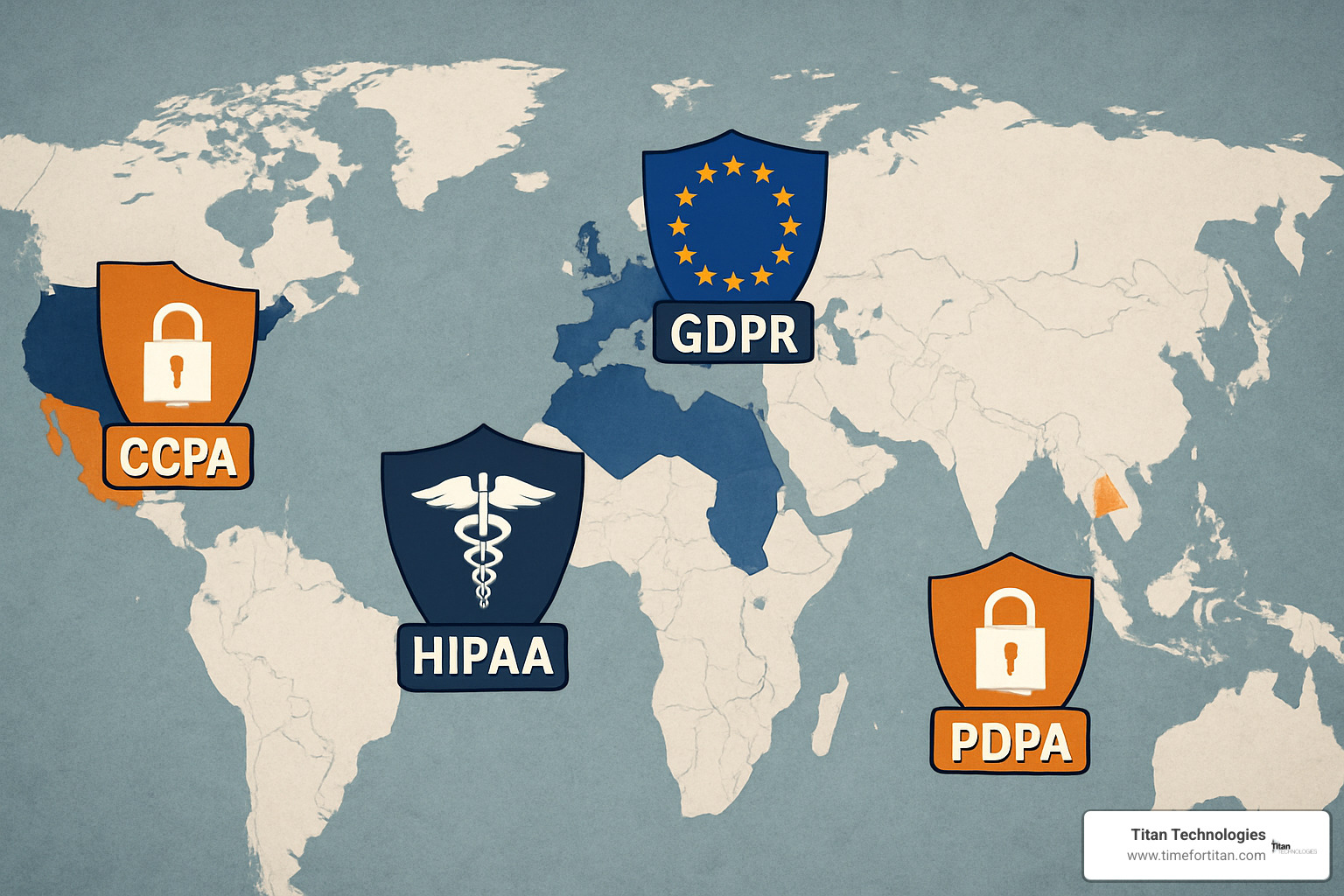
In Europe, the General Data Protection Regulation (GDPR) takes a broad view, considering personal data as “any information relating to an identified or identifiable natural person.” This covers the obvious things like your name and address, but also extends to indirect identifiers that could single you out in a crowd.
As the European Commission puts it, “The GDPR applies to both automated personal data and to manual filing systems where personal data are accessible according to specific criteria.” In other words, whether your information is stored in a high-tech database or an old-fashioned filing cabinet, the same protections apply.
Cross the Atlantic to California, and you’ll find the California Consumer Privacy Act (CCPA) uses slightly different language. They prefer “personal information” over “personal data,” defining it as details that identify, relate to, or could reasonably be linked with a particular consumer or household.
On the global stage, the United Nations has established Principles on Personal Data Protection and Privacy to create some harmony across its organizations. These principles emphasize accountability, purpose limitation, and human rights in how data gets processed.
In Southeast Asia, both Malaysia and Singapore have their own Personal Data Protection Acts, with Singapore’s Personal Data Protection Commission actively enforcing compliance.
The United States presents a unique challenge with its patchwork approach. Instead of one comprehensive federal law, we have sector-specific regulations: financial data falls under the Gramm-Leach-Bliley Act, health information under HIPAA, educational records under FERPA, consumer credit information under FCRA, and children’s online privacy under COPPA.
Perhaps most important for businesses to understand is the cross-border reach of these regulations. The GDPR doesn’t stop at Europe’s borders – it applies to any organization offering goods or services to EU residents, no matter where that organization is based. Similarly, California’s privacy laws can extend to businesses outside the state if they meet certain thresholds.
Personal Data Protection under GDPR
The GDPR has quickly become the gold standard for personal data protection worldwide. Its comprehensive approach has influenced privacy regulations across the globe, and for good reason.
At its core, the GDPR requires that any processing of personal data must have a lawful basis. This might be consent freely given by the individual, necessity for fulfilling a contract, compliance with legal obligations, protection of vital interests, performance of a public interest task, or legitimate interests of the data controller (carefully balanced against individual rights).
The regulation takes special care with sensitive information. Data about racial or ethnic origin, political opinions, religious beliefs, trade union membership, genetic and biometric details, health information, and sexual orientation all receive heightened protection. Processing these special categories generally requires explicit consent or must meet specific exceptions outlined in the regulation.
As GDPR Article 5 clearly states, “Any processing of personal data should be lawful and fair” – a simple principle that forms the foundation for all data protection activities in the EU.
Personal Data Protection under CCPA & Emerging U.S. State Laws
While Europe acceptd comprehensive privacy regulation, the United States has taken a state-by-state approach, with California leading the charge in personal data protection.
The California Consumer Privacy Act (CCPA), expanded by the California Privacy Rights Act (CPRA), provides Californians with privacy rights similar to those under the GDPR. However, there’s a key difference in approach. Rather than focusing on lawful bases for processing data, California emphasizes consumer rights and business obligations.
The CCPA applies to for-profit businesses that meet at least one of these criteria: annual revenue exceeding $25 million; buying, selling, or sharing personal information of 100,000+ California residents; or deriving 50% or more of annual revenue from selling consumers’ personal information.
California’s newest addition, the Delete Act (effective January 1, 2024), specifically targets data brokers. It requires them to create a centralized mechanism for consumers to delete their information from all registered data brokers at once – no more having to contact dozens of companies individually.
Beyond California’s borders, a growing number of states have enacted their own comprehensive privacy laws, each with their own unique flavors: Virginia Consumer Data Protection Act, Colorado Privacy Act, Connecticut Data Privacy Act, Utah Consumer Privacy Act, and the Florida Digital Bill of Rights.
As law firm DLA Piper aptly notes, “United States privacy law is a complex patchwork of national, state and local privacy laws and regulations.” For businesses operating across multiple states, this creates a challenging compliance landscape – especially for our clients here in Central New Jersey who may have customers throughout the tri-state area and beyond.
For more detailed information about these frameworks, you can visit the official sources at California Consumer Privacy Act and European Commission – What is personal data?
Principles & Core Rights in Personal Data Protection
When it comes to personal data protection, there’s a set of universal principles that form the backbone of most privacy regulations worldwide. Think of these as the “golden rules” that organizations should follow when handling your personal information.
At the heart of these protections are seven fundamental principles that guide how your data should be treated:
First, there’s lawfulness, fairness, and transparency. This means companies can’t just collect your data however they want – they need a legal reason, they must be upfront about it, and they should handle your information fairly.
Next is purpose limitation – a fancy way of saying organizations should only collect your data for specific, clearly stated reasons, and not use it for something entirely different later (with some exceptions for research or archiving).
Data minimization is another crucial principle – companies should only collect what they actually need. If they don’t need your birthday to deliver your pizza, they shouldn’t ask for it!
The accuracy principle requires organizations to keep your information correct and up-to-date. If something’s wrong, they need to fix it promptly.
Storage limitation means your data shouldn’t be kept forever – only as long as necessary for the original purpose.
Your data also needs integrity and confidentiality – proper security measures to prevent unauthorized access, loss, or damage.
Finally, accountability requires organizations to not just follow these rules but also prove they’re following them.
These principles aren’t just abstract concepts – they translate into real, practical rights for you:
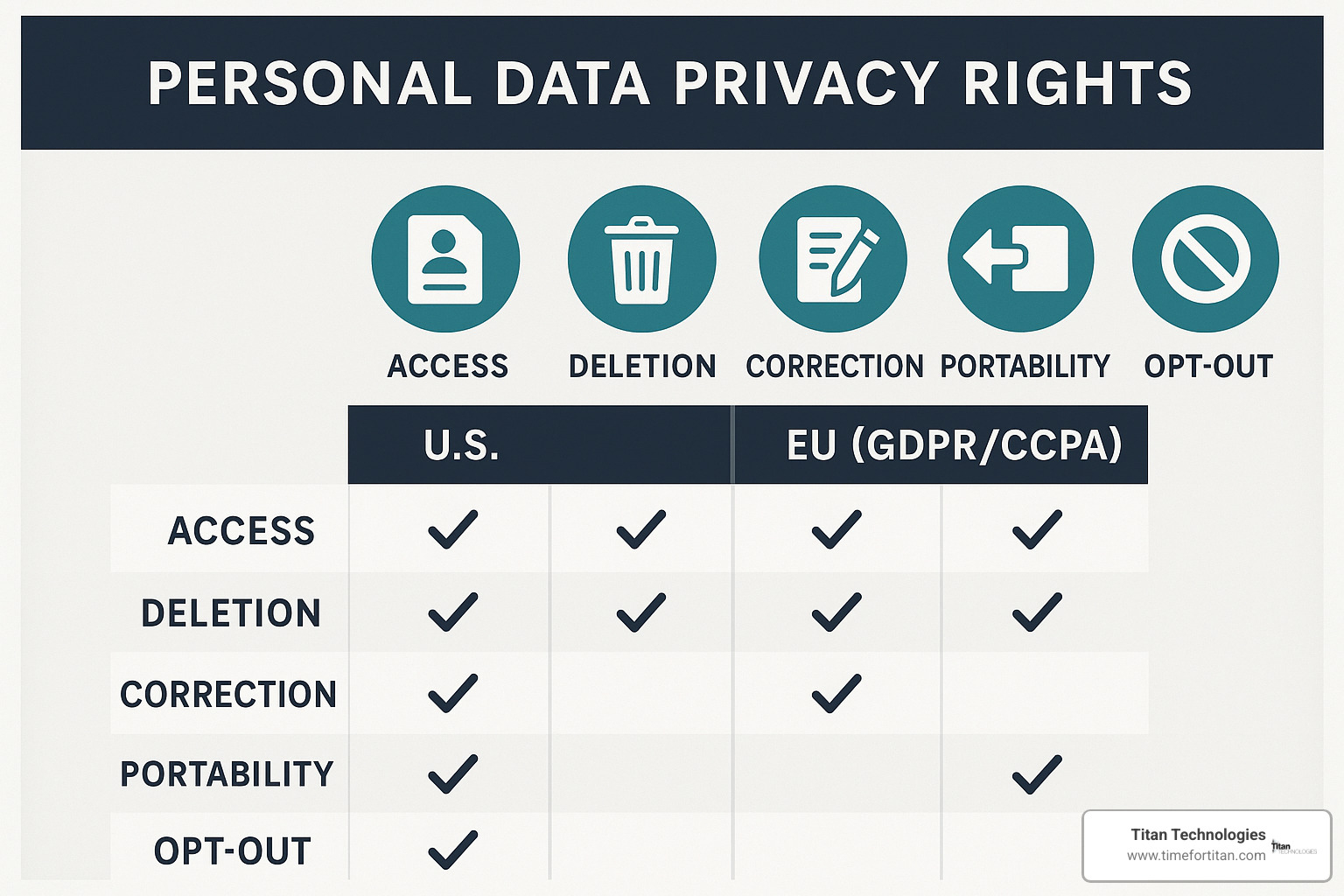
You have the right of access to request copies of your personal information. The right to deletion (sometimes called the “right to be forgotten”) lets you request removal of your data under certain circumstances. If your information is incorrect, the right to correction allows you to have it fixed. The right to data portability enables you to receive your data in a usable format and transfer it elsewhere. And the right to opt out gives you the power to object to certain types of processing, including marketing.
Of course, there are some reasonable limits to these rights. Companies may decline deletion requests if they need to keep your data for legal reasons or to defend against claims. And response timelines vary – GDPR typically gives companies one month to respond, while California’s CCPA allows 45 days (with possible extensions).
Want to learn more about solutions that can help protect your data privacy? Check out our Data Privacy Solutions page.
Exercising Your Personal Data Protection Rights
So how do you actually put your personal data protection rights into practice? It typically starts with something called a Data Subject Access Request (DSAR) – which is just a formal way of asking a company what information they have about you.
The process is simpler than it sounds. First, figure out which organization has your data and find their privacy contact (often called a Data Protection Officer). Then submit your request – most companies offer multiple ways to do this, whether through email, a form on their website, or even regular mail. Be clear about what you’re asking for and which right you’re exercising.
The company will likely ask you to verify your identity – this is actually a good thing! It ensures they’re not handing your personal information to someone pretending to be you. Then comes the waiting game. Under California’s CCPA, companies have 45 days to respond (though they might request an extension). In Europe, GDPR typically requires responses within a month.
When you receive the response, it should be clear and easy to understand. If you’re not satisfied or your request is denied, you have options – including filing a complaint with the appropriate privacy authority.
If you live in California, there’s a helpful tool called the Global Privacy Control (GPC) that automatically signals your opt-out preferences as you browse the web. It’s like a digital “Do Not Sell My Personal Information” sign that follows you around online.
For our Central New Jersey business clients who serve customers across multiple states or countries, keeping up with all these different requirements can be challenging. At Titan Technologies, we help design streamlined processes that respect individual privacy rights while keeping administrative burdens manageable. We believe that good personal data protection practices aren’t just about compliance – they’re about building trust with your customers.
Organizational Obligations & Security Best Practices
Picture this: You’re running a small business in New Brunswick, and suddenly you realize your customer database is a goldmine of personal information. Are you a data controller or processor? And what exactly does that mean for your responsibilities?
The distinction is crucial. If you’re determining why and how data is processed (like that local brewery deciding what employee information to collect), you’re a controller. If you’re handling data on someone else’s behalf (like the payroll company the brewery hires), you’re a processor. This isn’t just technical jargon—it fundamentally shapes your personal data protection obligations.
For Central New Jersey businesses, understanding these roles helps clarify who bears primary responsibility when things go wrong. And in today’s data-driven world, things can certainly go wrong without proper safeguards.
Organizations with solid data protection practices typically accept several key obligations. Data Protection Impact Assessments help you identify privacy risks before they become problems—think of them as preventive medicine for your data practices. Maintaining detailed processing records creates a clear map of what personal data you collect and why. Effective vendor management ensures your third-party partners don’t become your security weak link. And breach notification protocols prepare you for the worst-case scenario, when you need to inform authorities and affected individuals quickly (remember, GDPR gives you just 72 hours for serious breaches).
“Most businesses don’t realize they’re responsible for data breaches caused by their vendors,” notes one privacy expert. “That payroll provider you hired? Their security practices can become your problem overnight.”
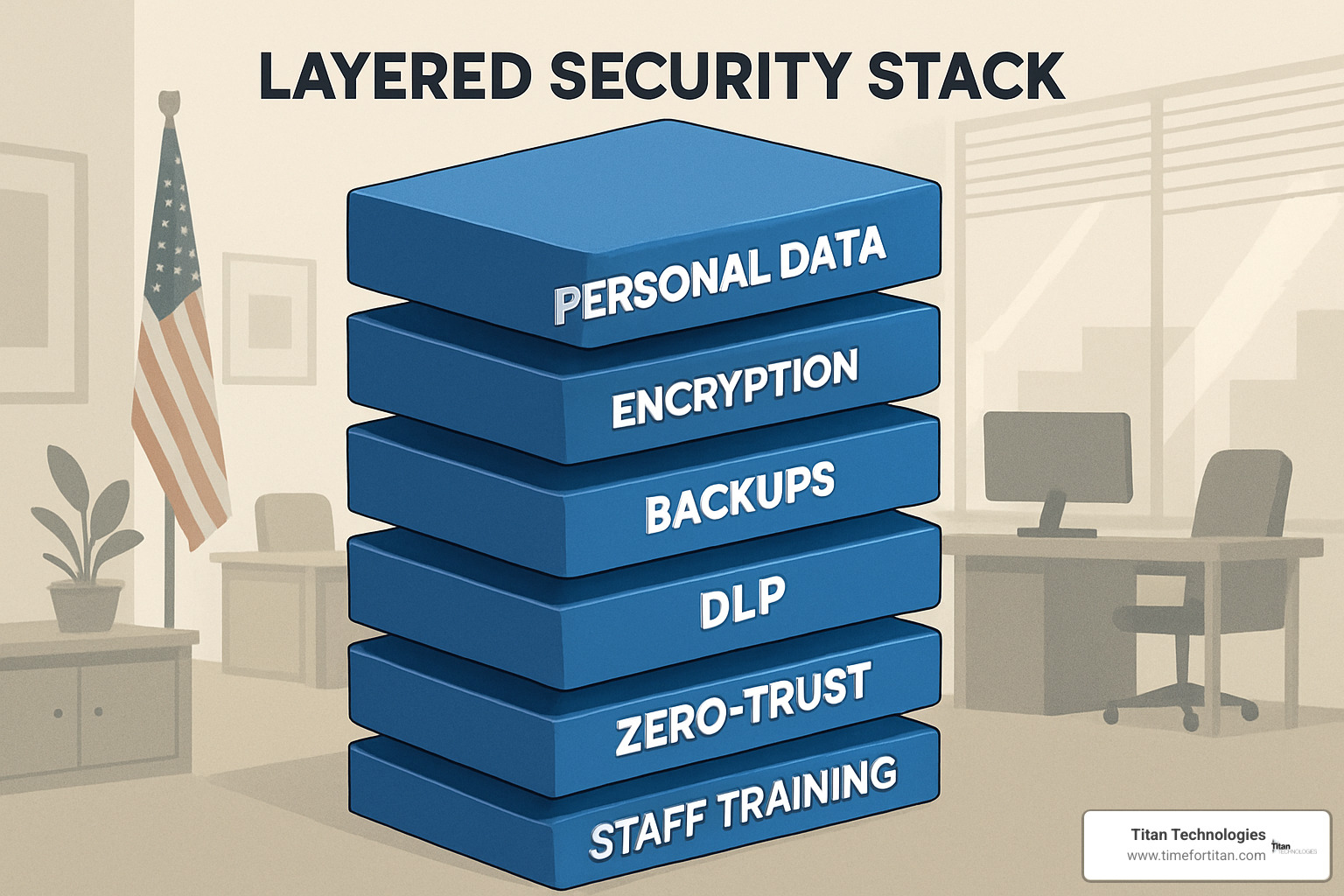
Beyond regulatory requirements, protecting personal data requires robust security measures. Think of your data protection strategy as a house—you need multiple layers of security to keep the valuables safe:
Strong encryption protects data both in storage and during transmission—like having a safe inside a locked room. Regular backups provide insurance against ransomware and accidental deletion. Data Loss Prevention tools act like security guards, preventing sensitive information from walking out the door. A zero-trust architecture verifies everyone and everything trying to access your network—even people already “inside” the building. And don’t forget comprehensive staff training—because even the best security technology can be undermined by human error.
The Federal Trade Commission has made it clear: “Implementing and documenting reasonable data security measures” isn’t optional if you want to avoid enforcement actions. They’ve increasingly used their authority to go after companies with lax security practices under unfair or deceptive trade practice provisions.
Building a Compliant Data Protection Plan
Creating a data protection plan doesn’t have to be overwhelming. Start by understanding your data landscape—what personal information you collect, where it lives, and how it flows through your organization.
Risk assessments form the foundation of any good plan. They help you identify vulnerabilities before they become breaches. One small accounting firm in Matawan finded through a risk assessment that their employees were routinely emailing unencrypted tax documents containing Social Security numbers—a practice they quickly corrected.
Data classification helps you prioritize your protection efforts. Not all data needs the same level of security—your marketing email list requires different protection than your customer payment information.
Establishing clear governance structures means assigning responsibility for personal data protection. Someone needs to “own” this issue, whether it’s a formal Data Protection Officer or another designated role.
A thoughtful retention schedule prevents data hoarding—a common problem for businesses of all sizes. As one security expert candidly observed, “Admit it, you are doing it, too”—keeping data long after its useful life, creating unnecessary risk.
Finally, developing incident response procedures prepares you for security events. It’s like having a fire drill for data breaches—everyone knows their role before the emergency happens.
For businesses across Central New Jersey—from Edison to Princeton, Elizabeth to Red Bank—we at Titan Technologies understand these challenges aren’t theoretical. They’re practical problems requiring practical solutions. We help develop customized data protection plans that align with your specific business needs while meeting regulatory requirements.
Protecting personal data isn’t just about compliance—it’s about maintaining the trust your customers place in you every time they share their information. And in today’s digital economy, that trust may be your most valuable asset.
| Technical Measures | Organizational Measures |
|---|---|
| Encryption | Staff training programs |
| Multi-factor authentication | Clear data handling policies |
| Network monitoring | Vendor assessment procedures |
| Access controls | Regular compliance audits |
| Secure backup systems | Incident response planning |
Emerging Trends & Cross-Border Data Challenges
The world of personal data protection is constantly evolving, with new technologies and regulations reshaping how we think about privacy and security. It’s like trying to hit a moving target – just when you think you’ve got it figured out, everything changes!
AI and big data have dramatically transformed how organizations collect and process information. With artificial intelligence becoming more integrated into everyday business operations, regulators are racing to keep up. California’s Age-Appropriate Design Code (though currently facing legal challenges) and the EU’s AI Act represent some of the first serious attempts to put guardrails around these powerful technologies.
Children’s online privacy has rightfully taken center stage in recent years. As kids spend more time online, protections like the Children’s Online Privacy Protection Act (COPPA) in the US have become increasingly important. These regulations impose much stricter requirements for collecting and using children’s personal information – and for good reason!
Health data is another area seeing rapid regulatory development. Beyond traditional healthcare laws like HIPAA, we’re seeing innovative new protections emerge. Washington’s My Health My Data Act, for instance, takes a broad view of health information that extends well beyond traditional medical records.
Cross-border data transfers have become particularly thorny. When your data travels across international borders, which laws apply? The EU-US Data Privacy Framework (which replaced the invalidated Privacy Shield) offers one solution for companies transferring personal data from Europe to participating US businesses. Standard Contractual Clauses (SCCs) provide another pathway for international transfers, though they come with their own complexities.
Some countries have taken a more direct approach through data localization requirements. These laws mandate that certain types of personal data must physically remain within national borders. This creates significant challenges for cloud-based services and global operations that rely on distributed infrastructure.
On the technology front, Privacy-Enhancing Technologies (PETs) are gaining momentum. These innovative solutions help protect privacy while still enabling valuable data use – a win-win approach. Singapore’s Personal Data Protection Commission has even launched a PET Sandbox program to encourage businesses to adopt these promising technologies.
Biometric privacy has emerged as a particularly sensitive area. Laws like Illinois’ Biometric Information Privacy Act (BIPA) have led to significant litigation and are changing how organizations implement technologies like facial recognition. The unique nature of biometric data – you can change a password, but you can’t change your fingerprints – requires special consideration.
The threat landscape continues to evolve in frightening ways. Modern ransomware attacks don’t just encrypt your data; they threaten to publish it if you don’t pay up. This creates a double whammy of both security and privacy concerns for organizations of all sizes.
For businesses in Central New Jersey that operate across state lines or internationally, these trends create a complex compliance puzzle. At Titan Technologies, we help local businesses steer these challenges by staying ahead of evolving requirements. Our approach combines proactive monitoring with adaptive security strategies custom to your specific business needs.
The future of personal data protection will require nimble approaches that can adapt to emerging technologies and changing regulations. More info about Data Protection Cloud-Based Services can help you understand how cloud technologies fit into this evolving landscape.
Conclusion
In today’s digital landscape, personal data protection isn’t just a nice-to-have—it’s become as essential as locking your front door. Throughout this guide, we’ve steerd the complex web of regulations that businesses must understand to stay compliant and build trust with customers.
The reality for Central New Jersey businesses is that managing these requirements can feel overwhelming. Whether you’re a small shop in Princeton or a growing enterprise in Newark, the expectations around protecting personal information remain equally demanding.
At Titan Technologies, we’ve helped countless local businesses transform data protection from a regulatory headache into a competitive advantage. We believe that robust personal data protection should feel like a natural extension of your business values, not just a checkbox exercise.
When you partner with us, we start by getting to know your specific challenges. We’ll conduct thorough risk assessments that identify where your sensitive data lives and where potential vulnerabilities might exist. Rather than applying one-size-fits-all solutions, we develop security measures custom to your business needs and the regulations that affect you most.
We’ve found that even the best technical solutions can falter without proper human understanding. That’s why our employee training programs focus on making data protection principles relatable and practical for your team. After all, your employees are both your greatest asset and potentially your biggest vulnerability when it comes to data security.
The digital threat landscape never stands still, and neither do regulations. Our ongoing monitoring services keep an eye on both, ensuring you stay ahead of emerging challenges. And because even the best defenses can be breached, we help you develop incident response plans that minimize damage and maintain customer trust if the worst happens.
Personal data protection is ultimately a journey, not a destination. As your business grows and evolves, so too should your approach to safeguarding the information entrusted to you. The good news? You don’t have to make that journey alone.
Whether you’re in Edison, Elizabeth, Lakewood, Newark, Trenton, Princeton, New Brunswick, Matawan, Woodbridge, Freehold, or Red Bank, our team at Titan Technologies brings local knowledge and global expertise to your data protection challenges. We understand the unique needs of Central New Jersey businesses because we’re your neighbors.
Ready to turn personal data protection from a compliance burden into a business strength? Explore our services and solutions or reach out for a conversation about your specific needs. Together, we can build a data protection approach that not only meets today’s requirements but adapts seamlessly to tomorrow’s challenges.
After all, protecting what matters isn’t just good business—it’s good citizenship in our increasingly connected world.