Why Data Security in the Cloud is Critical
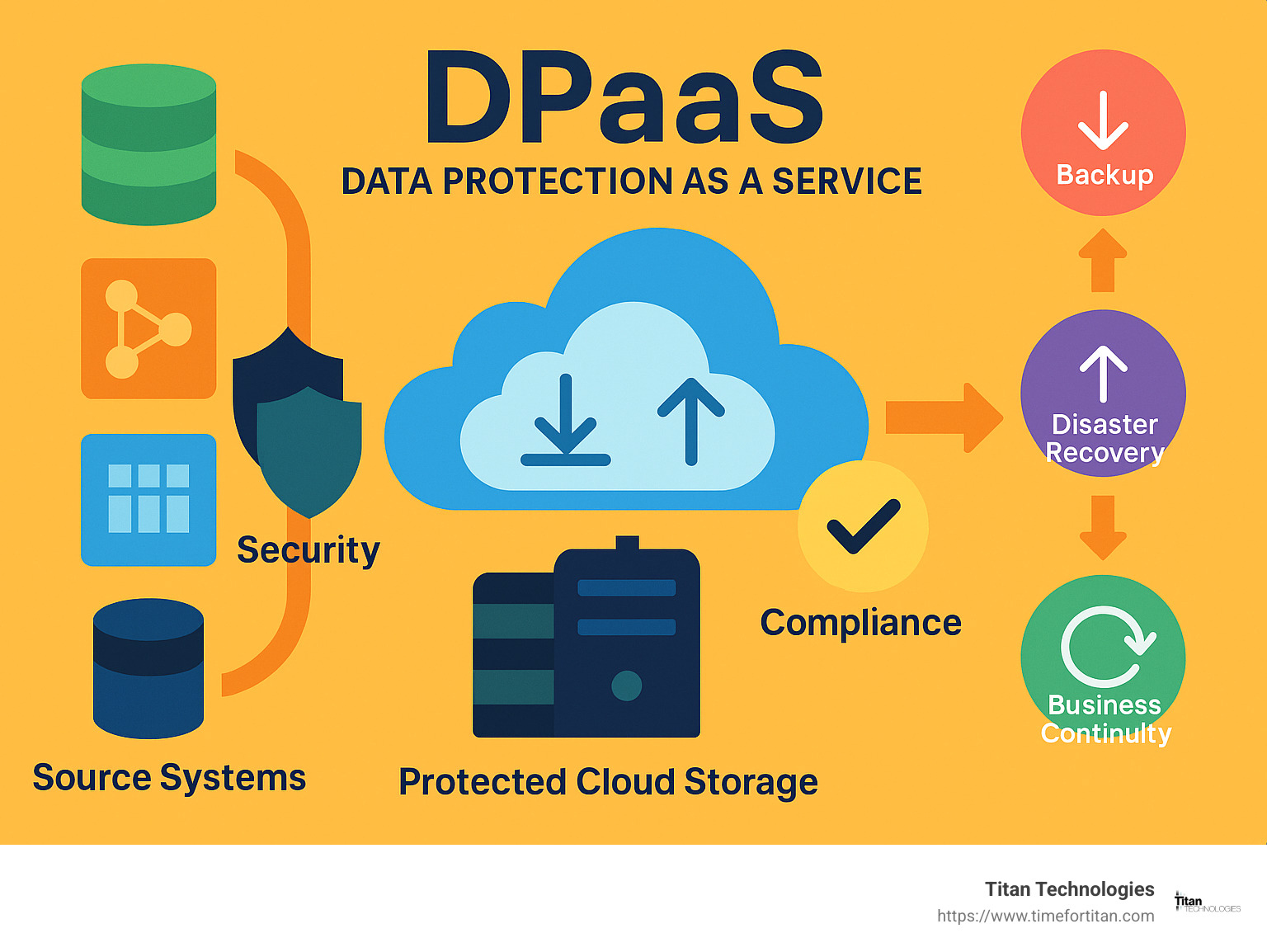
Data protection as a service is so much more than just another tech acronym. It’s a comprehensive cloud-based subscription model that brings together backup, disaster recovery, and robust security capabilities under one umbrella—all managed for you with clear service level agreements.
If you’re just getting your bearings with this concept, here’s a quick snapshot:
| What is it? | Key Components | Main Benefits |
|---|---|---|
| A cloud-based subscription service that protects your organization’s data | • Automated backups • Disaster recovery • Data encryption • Access controls |
• Reduced capital costs • Scalability • Improved security • Improved compliance |
Let’s face it—cybersecurity threats aren’t just making occasional headlines anymore; they’re daily front-page news. With studies showing that a concerning 20% of recovery attempts fail, treating data protection as an afterthought is no longer an option for any business that wants to stay afloat. Traditional protection methods are becoming both expensive money pits and administrative nightmares as threats grow more sophisticated and data environments more complex.
Today’s ransomware attacks have evolved far beyond their simpler ancestors. They’re smarter now—actively hunting for your backup files to cut off your escape route and force you to pay up. As Peter Mackenzie from Sophos Rapid Response colorfully but accurately puts it:
“Modern ransomware is less of a primary threat and more of a courtesy call announcing a larger-scale attack on your organization.”
For small and medium businesses, this creates what I like to call the “perfect risk storm.” Your data is growing exponentially due to cloud apps and remote work—often requiring backup capacity 10-50 times larger than your original data. Meanwhile, regulations like GDPR, HIPAA, and CCPA aren’t just suggestions; they come with serious penalties if you don’t protect data properly.
This is where data protection as a service shines. It shifts the burden from your already-stretched internal team to specialists who do this all day, every day. Instead of a massive upfront investment in infrastructure, you get a flexible operational expense that grows with you. The smart deduplication technology behind these services can shrink your storage requirements by up to 90%, while giving you near-instant backups and dramatically faster recovery when you need it most.
The beauty of DPaaS is simplicity—one complete solution, one service level agreement. No more juggling multiple tools and vendors while hoping nothing falls through the cracks.
If you’re looking to dive deeper into data protection as a service, we’ve got you covered with these helpful resources:
– Data Protection: Cloud-Based Services
– Data Protection, Governance, Risk Management, and Compliance
– Data Protection Security Controls
Data Protection as a Service (DPaaS): Definition, Components & Differentiators
Data protection as a service is changing how businesses safeguard their critical information. Unlike traditional backup solutions that require significant upfront investments in hardware and software, DPaaS delivers comprehensive protection through a flexible cloud-based subscription model that brings together backup, disaster recovery, and security under one umbrella.
This approach makes perfect sense for today’s businesses because it:
Converts those large capital expenses into manageable monthly operating costs, making budgeting more predictable. No more unexpected hardware failures requiring emergency purchases!
Frees you from the endless cycle of hardware refreshes and maintenance headaches that seem to always happen at the worst possible time.
Provides transparent monthly billing based on what you actually use, rather than what you might need someday.
Grows smoothly alongside your business without requiring disruptive upgrades or migrations.
Reduces the burden on your IT team, allowing them to focus on initiatives that drive your business forward rather than babysitting backup jobs.
The technology powering data protection as a service uses sophisticated deduplication and compression that typically shrinks storage requirements by up to 90%. This efficiency doesn’t just save money—it dramatically improves performance, enabling recovery points and times measured in minutes rather than hours or days.
For businesses across New Jersey facing growing regulatory requirements and security threats, DPaaS offers a welcome alternative to juggling multiple backup solutions, disaster recovery platforms, and security tools. Instead of managing relationships with several vendors and reconciling different SLAs, you get one comprehensive service agreement with clear metrics and a single point of accountability.
Core Components of Data Protection as a Service
A robust data protection as a service solution combines several essential elements working together to create a safety net for your information:
Automated Backups handle the daily protection of your data without requiring manual intervention. These intelligent systems identify only what’s changed since the last backup, minimizing both the time needed and network impact. Think of it as having a vigilant guardian that never takes a day off or calls in sick.
Disaster Recovery Orchestration prepares for the worst by creating predefined recovery playbooks that execute automatically when disaster strikes. This approach eliminates the confusion and human error that often occur during stressful recovery situations when every minute counts.
Immutable Storage creates backup copies that simply cannot be altered—even by someone with administrative privileges. This technology is your best defense against ransomware, as attackers can’t encrypt or delete backups that are inherently write-protected.
End-to-End Encryption wraps your data in a protective layer using military-grade encryption standards both while it’s moving and when it’s stored. The encryption keys are managed separately with strict controls, ensuring that only authorized users can access your information.
Multi-Factor Authentication adds crucial layers of security by requiring multiple verification methods before anyone can access backup systems or initiate recoveries. This simple step effectively blocks most credential-based attacks.
AI-Powered Ransomware Detection works like an immune system for your data, constantly monitoring for unusual patterns that might indicate an attack in progress. This early warning system can spot trouble before it spreads, allowing for immediate intervention.
We’ve seen these components protect businesses throughout Central New Jersey—from healthcare providers handling sensitive patient data to financial firms managing client investments and retailers processing thousands of daily transactions. When properly integrated, these technologies create a resilient shield against both everyday mishaps and sophisticated attacks.
Data Protection as a Service vs Backup as a Service
While sometimes used interchangeably, data protection as a service and Backup as a Service (BaaS) are not the same thing. Understanding the differences helps ensure you’re getting the protection your business actually needs:
| Feature | Data Protection as a Service | Backup as a Service | Disaster Recovery as a Service |
|---|---|---|---|
| Primary Focus | Comprehensive data security, backup, and recovery | Data backup and restoration | System-level recovery and business continuity |
| Scope | End-to-end protection across data lifecycle | Point-in-time data copies | Application and infrastructure failover |
| Failover Capabilities | Included for critical systems | Limited or none | Primary function |
| Security Features | Comprehensive (encryption, access controls, ransomware protection) | Basic | Moderate |
| Compliance Support | Extensive regulatory alignment | Limited | Focused on continuity requirements |
| Management Overhead | Minimal (fully managed) | Moderate | Moderate to high |
| Cost Model | Subscription with unified billing | Pay-per-use or capacity-based | Often includes standby infrastructure costs |
BaaS essentially focuses on creating and storing copies of your data that can be restored when needed. While valuable, it typically lacks the comprehensive security measures, orchestrated recovery workflows, and compliance capabilities that define true data protection as a service.
This distinction is particularly important for businesses in regulated industries like healthcare providers in Trenton or financial services firms in Elizabeth. These organizations need more than just backup copies—they need verifiable compliance with industry standards and the ability to demonstrate proper data handling during audits.
Data Protection as a Service vs Disaster Recovery as a Service
Disaster Recovery as a Service (DRaaS) represents another specialized subset that’s often confused with comprehensive data protection as a service. Here’s how they differ:
Focus and Scope: DRaaS is laser-focused on maintaining business continuity through rapid system recovery after disasters. It typically creates standby copies of your entire production environment that can be activated when primary systems fail. Data protection as a service includes this capability but extends further to cover everyday backup operations, data security, and ongoing compliance management.
Recovery Methodology: DRaaS uses continuous replication to maintain near-real-time copies of systems for quick failover. DPaaS incorporates this capability but also provides more flexible recovery options for different scenarios—from restoring a single accidentally deleted file to rebuilding complete systems after a catastrophic event.
Infrastructure Requirements: Traditional DRaaS often requires dedicated standby infrastructure that sits idle until needed, increasing costs. Modern data protection as a service leverages cloud elasticity to provision recovery resources only when necessary, optimizing expenses while maintaining readiness.
Compliance Integration: While DRaaS addresses the business continuity aspects of compliance frameworks, comprehensive DPaaS solutions integrate broader compliance capabilities including retention management, access controls, and audit logging across all protected data.
Shared Responsibility Model: DPaaS typically offers clearer lines between provider and customer responsibilities, with more management tasks handled by the service provider than in traditional DRaaS arrangements. This clarity helps prevent critical protection tasks from falling through the cracks.
For businesses across New Jersey, from manufacturers in New Brunswick to professional services firms in Red Bank, understanding these distinctions helps in selecting the right level of protection for different workloads based on their business importance and compliance requirements.
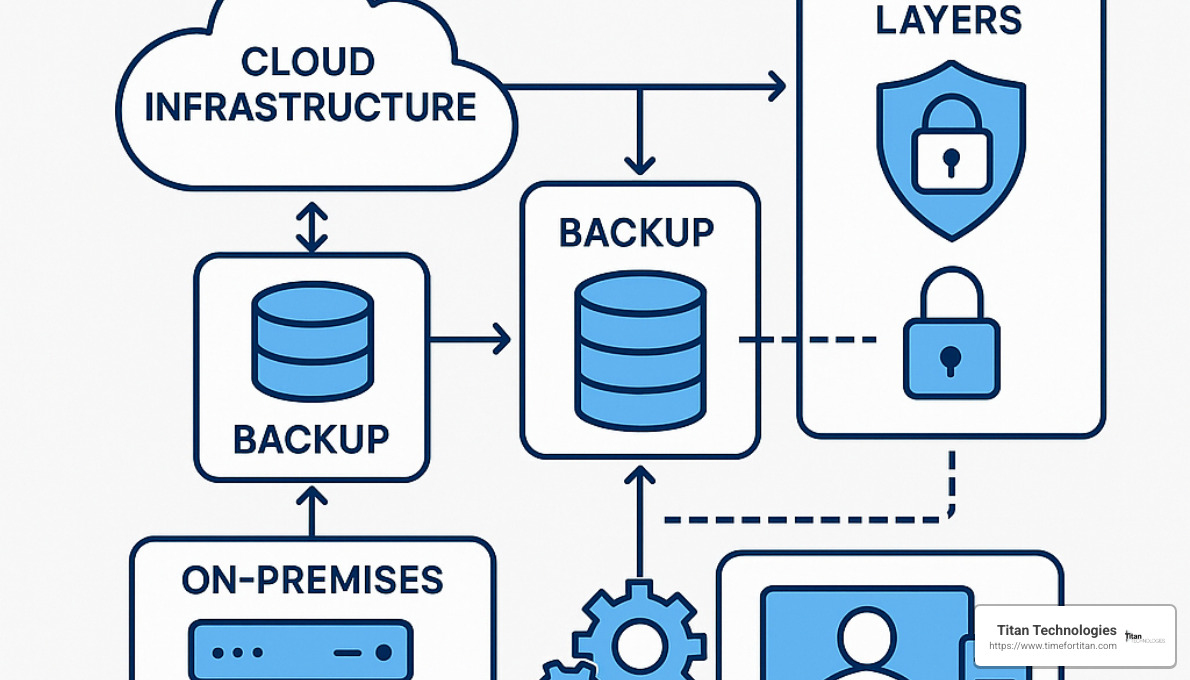
How DPaaS Works: Cloud Architecture, Automation & Security
The technical foundation of data protection as a service is like a well-orchestrated symphony where cloud architecture, intelligent automation, and multi-layered security play together in perfect harmony. Understanding this behind-the-scenes magic helps explain why so many New Jersey businesses are embracing this approach.
When you implement DPaaS, several coordinated processes work together to keep your data safe. The system first analyzes your environment to identify what needs protection and how critical each piece is. This ensures nothing falls through the cracks.
Before any data leaves your network, source-side deduplication kicks in – a fancy way of saying the system is smart enough to only send new or changed information. This is particularly helpful for our clients in places like Lakewood and Matawan, where internet bandwidth isn’t always abundant.
Your data then gets replicated to multiple data centers in different geographic locations. Think of it as not keeping all your eggs in one basket – if something happens to one facility, your information remains safe elsewhere.
Recovery becomes remarkably straightforward through API-driven processes that automate complex restoration workflows. Whether you need a single file or an entire application stack, the system handles the heavy lifting.
For ultimate protection against ransomware, critical backups are stored in air-gapped environments – completely isolated from your production networks. It’s like keeping your valuables in a vault that criminals can’t reach electronically.
Your data stays encrypted from the moment it leaves your systems until you need to restore it, using bank-grade encryption standards. Meanwhile, AI-powered monitoring constantly watches for unusual patterns that might signal trouble brewing.
For a deeper dive into cloud-based protection approaches, our guide on Data Protection: Cloud-Based Services provides additional insights.
Automation & Orchestration Inside Data Protection as a Service
The real magic of data protection as a service lies in how it eliminates tedious manual tasks and human error through intelligent automation.
Rather than managing individual backup jobs, you simply define protection policies based on what makes sense for different types of data. The system handles all the scheduling details automatically. For many of our Freehold and Edison clients, this means their teams can focus on strategic work instead of babysitting backups.
Modern DPaaS solutions can capture data changes as they happen – not just during nightly backup windows – achieving protection that’s almost real-time without slowing down your systems.
The user-friendly self-service portals are particularly popular with our clients. Authorized staff can recover their own files without calling IT, which means faster recovery and fewer support tickets for already busy IT teams.
Behind the scenes, the system regularly tests recovery procedures by automatically restoring systems in isolated environments and checking that everything works correctly. It’s like having a dedicated tester constantly verifying your safety net is ready when needed.
When recovery is necessary, orchestrated recovery sequences ensure systems come back online in the right order. The system understands that your database needs to be up before the applications that use it, preventing frustrating dependency issues during restores.
This level of automation delivers particular value for small and medium businesses throughout New Jersey that don’t have the luxury of dedicated backup administrators or round-the-clock IT staffing.
Security Hardening & Ransomware Resilience
With ransomware attacks becoming increasingly sophisticated, data protection as a service incorporates multiple security layers specifically designed to keep your data safe.
The foundation is a zero-trust architecture that treats every access attempt with healthy skepticism. Rather than assuming users or systems are trustworthy based on their network location, every request must be verified – regardless of who’s asking.
Critical backup information is stored in immutable databases that cannot be modified or deleted, even by administrative users. This prevents attackers from corrupting the backup system’s ability to locate and restore your data – a common tactic in sophisticated attacks.
Access to management functions requires multi-factor authentication, combining something you know (password) with something you have (like a security token). For our most security-conscious clients in Newark and Trenton, this provides peace of mind that only authorized personnel can access backup systems.
The most critical backups are maintained in completely isolated environments with no network connectivity to production systems, making them inaccessible to ransomware. We often explain this to clients as creating a digital firebreak that malware simply cannot cross.
AI systems constantly monitor backup operations for unusual patterns that might indicate ransomware activity. For example, if the system suddenly sees high volumes of file modifications or deletions, it can raise alerts before damage spreads too far.
As Peter Mackenzie from Sophos Rapid Response wisely notes: “Identifying that you are under a ransomware attack is easy; identifying that the attacker is on your network a week before the attack takes place is what counts.” Modern data protection as a service platforms are designed to spot these early warning signs, helping to stop attackers before they can compromise both your production and backup environments.
For businesses throughout Central New Jersey, these security measures provide essential protection against threats that could otherwise lead to devastating data loss and business disruption.
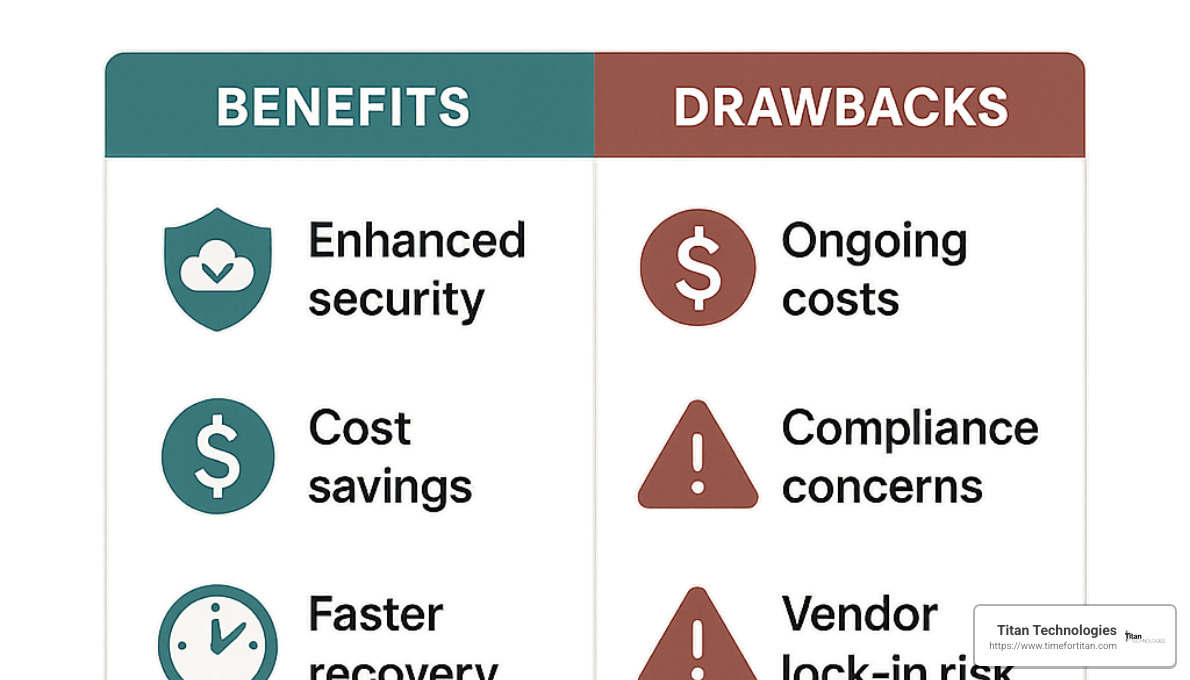
Why It Matters: Benefits, Drawbacks, Compliance & Use Cases
The decision to adopt data protection as a service isn’t just a technical choice—it’s a strategic business move that touches everything from your bottom line to your compliance posture. Let’s explore why this matters to your organization and how it plays out in the real world.
When our clients in Princeton and New Brunswick made the switch to DPaaS, many reported cost reductions of 30-50% compared to their previous on-premises solutions. This dramatic savings comes from eliminating hardware purchases, maintenance contracts, and those painful upgrade cycles that seem to come around faster each year.
Beyond the financial benefits, the rapid recovery capabilities of modern DPaaS platforms can be truly transformative. Instead of spending days restoring critical systems after an incident, your team can have everything back up and running in minutes. For a business where every hour of downtime means lost revenue, this difference isn’t just convenient—it’s essential.
Your IT staff probably didn’t join your company because they love babysitting backup jobs at 2 AM. Data protection as a service frees your technical talent from these mundane administrative tasks, letting them focus on initiatives that actually move your business forward. As one of our clients in Freehold put it: “My team finally has time to innovate instead of just keeping the lights on.”
Of course, no solution is perfect. Cloud-based protection does create some dependency on your internet connection for both backup and recovery operations. If your business is in an area with limited bandwidth, large-scale data transfers might present challenges. We’ve helped several clients in rural New Jersey address this by implementing bandwidth optimization techniques and scheduling their most intensive backups during off-hours.
Some cloud providers also charge additional fees when you retrieve your data during recovery operations—a bit like charging you to take your own money out of the bank. These “egress fees” can add up during major incidents, so it’s important to understand the full cost picture upfront.
There’s also the question of vendor lock-in to consider. Moving terabytes of backup data between providers isn’t a weekend project, which can create a long-term dependency on your chosen vendor. At Titan Technologies, we help our clients develop multi-cloud strategies that preserve flexibility while maximizing protection.
Regulatory Compliance Powered by Data Protection as a Service
For many of our clients, especially those in healthcare and financial services, compliance requirements are what initially drive them toward data protection as a service. The built-in compliance features make maintaining regulatory alignment dramatically simpler.
Modern DPaaS platforms automatically generate comprehensive audit trails that track every interaction with your protected data. Who accessed what information, when they accessed it, what changes they made—it’s all captured and preserved for when auditors come knocking. One healthcare provider in Trenton told us this feature alone saved their compliance team over 20 hours per month in manual documentation.
Configurable retention policies ensure your data is kept exactly as long as regulations require—no more, no less. This balance helps you meet compliance obligations without wasting storage on information you’re no longer legally required to maintain.
The encryption standards built into quality DPaaS solutions align with industry frameworks like FIPS 140-2 and NIST guidelines, satisfying requirements across multiple regulatory environments. This is particularly valuable for organizations that must comply with several overlapping regulations.
For businesses concerned about data sovereignty, most DPaaS platforms now offer geographic controls that keep your information within specific regions. This feature has been essential for our financial services clients in Newark who must ensure customer data remains within approved jurisdictions.
For a deeper dive into these compliance aspects, check out our guide on Data Protection, Governance, Risk Management, and Compliance.
Real-World Use Cases
The true value of data protection as a service becomes clear when we look at how it performs in real-world scenarios.
A medical practice in Princeton experienced every modern business’s nightmare: a sophisticated ransomware attack that encrypted their entire patient management system. Because they had implemented DPaaS with immutable backups, they restored all systems within hours without paying the ransom. Their patients never even knew there had been a problem.
For a professional services firm in Matawan with employees scattered across New Jersey, protecting Microsoft 365 data was a major concern. Their DPaaS solution automatically backs up all SharePoint, Exchange, and OneDrive data, protecting against both accidental deletions and malicious actions. When an employee accidentally deleted a folder containing six months of project documentation, they restored it in minutes with three clicks.
A manufacturing company in New Brunswick faced a different challenge—they needed consistent protection across both their on-premises systems and cloud platforms. Their unified DPaaS solution provided seamless protection across this hybrid environment, eliminating the complexity of managing multiple protection systems.
For a banking institution in Elizabeth, meeting strict regulatory requirements was non-negotiable. Their DPaaS implementation automatically enforced retention policies, encrypted sensitive data, and provided the detailed audit trails necessary for examiner reviews. During their most recent audit, the examiner specifically commented on the completeness of their data protection documentation.
A retail chain with stores throughout New Jersey implemented DPaaS to protect their point-of-sale systems. When hardware failed at their Woodbridge location during the holiday shopping season, the system automatically restored operations to a virtual environment within minutes. Customers continued making purchases without interruption, and the store avoided what would have been thousands in lost sales.
For more insights on disaster recovery approaches like these, explore our resources on Disaster Recovery.
Potential Drawbacks & Mitigation
While the benefits of data protection as a service are substantial, being honest about potential challenges helps ensure successful implementation.
Bandwidth planning is essential, especially for businesses in locations with limited internet connectivity. We’ve helped clients in smaller New Jersey communities implement solutions like source-side deduplication that dramatically reduce the amount of data being transferred. For very large initial backups, some providers offer “seeding” options where your data is physically transported to the data center—think of it as the digital equivalent of moving house with a moving truck instead of making hundreds of small trips.
SLA validation should be a priority before signing any contract. What recovery times are actually guaranteed? What happens if those guarantees aren’t met? We help our clients in Red Bank and throughout Central New Jersey negotiate appropriate SLAs that align with their specific business requirements rather than accepting generic terms.
To address concerns about vendor lock-in, some organizations implement multi-cloud backup strategies. This approach increases resilience by ensuring your data isn’t all in one place, while preserving flexibility for the future.
Cost forecasting becomes more manageable when you implement proper data lifecycle management. By establishing clear policies for archiving and deletion, you prevent your storage costs from growing indefinitely. We recommend quarterly reviews of protection policies to ensure you’re not over-protecting low-value data.
By thoughtfully addressing these considerations, businesses throughout New Jersey can maximize the value of their data protection as a service investments while minimizing potential downsides. At Titan Technologies, we’ve guided dozens of companies through this process, helping them find the perfect balance for their specific needs.
Vendor Selection & Future Trends
Selecting the right data protection as a service provider is a critical decision that impacts your organization’s resilience, compliance posture, and operational efficiency. As the market evolves rapidly, understanding both current best practices and emerging trends helps ensure your data protection strategy remains effective.
As one industry expert puts it, “Data protection as a service must be the most resilient infrastructure service because it is a customer’s last line of defense.” This perspective really hits home when you consider what’s at stake – your business’s most valuable asset: its data.
When we work with clients across Central New Jersey, from Princeton to Newark, we emphasize several key factors in the selection process. Service Level Agreements should clearly define recovery objectives with actual financial penalties if they’re not met – after all, promises without consequences aren’t really guarantees. You’ll also want 24/7 support capabilities because, let’s face it, data disasters don’t politely wait for business hours.
Don’t overlook security certifications like SOC 2 Type II or ISO 27001. These aren’t just fancy acronyms – they’re independent verification that a provider follows strict security protocols. Your provider should also offer scalability that grows with your business without breaking the bank or degrading performance.
For many of our New Jersey clients, especially those in regulated industries, data residency options are non-negotiable. You need to know exactly where your data lives to meet compliance requirements. And finally, look for flexible consumption models that align with how you actually use the service – nobody likes paying for capacity they don’t need.
For organizations exploring flexible protection approaches, resources like Data Protection on Demand can provide valuable insights into consumption-based models.
Frequently Asked Questions about Data Protection as a Service
When businesses across Central New Jersey sit down with us to discuss data protection as a service, certain questions consistently arise. Let’s address the most common ones.
“How much will this cost?” is usually first on everyone’s mind. Most providers use consumption-based pricing where you pay for the amount of data protected, often with volume discounts. Some bundle all features together, while others charge separately for advanced capabilities. We always help our clients understand the total cost of ownership – because surprise bills are never welcome.
Implementation timelines vary widely. Basic setups can be completed in days, but protecting complex environments properly takes several weeks. The process includes findy, defining protection policies, initial data seeding, and validation testing. Cloud workloads typically deploy faster than on-premises systems.
Data ownership concerns are completely valid. You should always retain full ownership of your data – period. Reputable providers make this crystal clear in their agreements, positioning themselves as data processors rather than controllers. We always recommend having your legal team review these terms before signing.
Ransomware recovery guarantees have become increasingly important. Leading providers now offer specific assurances, including regular recovery testing and defined recovery timeframes. Some even provide financial guarantees if recovery objectives aren’t met, though these typically require that you follow their recommended protection policies.
Compliance with industry regulations is another crucial consideration. Good solutions include configurable frameworks for common regulations like HIPAA, GDPR, and PCI-DSS, automatically applying appropriate retention policies and security controls based on data classification.
Key Criteria When Choosing a Data Protection as a Service Provider
Beyond basic features, several critical factors should influence your selection of a data protection as a service provider.
SLA metrics and enforcement deserve careful scrutiny. Don’t just accept vague promises about “fast recovery” – look for specific, measurable recovery time and point objectives, along with clear remediation processes if these aren’t met. The most trustworthy agreements include financial penalties that give the provider real skin in the game.
When we help clients in Woodbridge or Freehold evaluate providers, we always verify security certifications. Current third-party validations like SOC 2 Type II demonstrate that a provider doesn’t just talk about security – they’ve proven it to independent auditors.
Compliance mapping is particularly crucial for businesses in regulated industries. Your provider should clearly document how their capabilities address specific regulatory requirements relevant to your industry – general assurances aren’t enough when auditors come calling.
Don’t just take a provider’s word about support responsiveness – test it yourself during evaluation by submitting sample issues at different times. Pay attention to both response times and the technical expertise of the people handling your inquiries. After all, in a crisis, you need knowledgeable help, not just a quick “we received your ticket” response.
Ecosystem integration can make or break your experience. The solution should work seamlessly with your existing applications and infrastructure through native connectors, reducing complexity and improving reliability.
Finally, consider the provider’s financial stability. Your data protection partner should demonstrate long-term viability – the last thing you need is service disruptions because they couldn’t keep their own business afloat.
For businesses seeking to implement enterprise-grade data protection, our guide on Enterprise Data Protection Services provides additional selection criteria and implementation best practices.
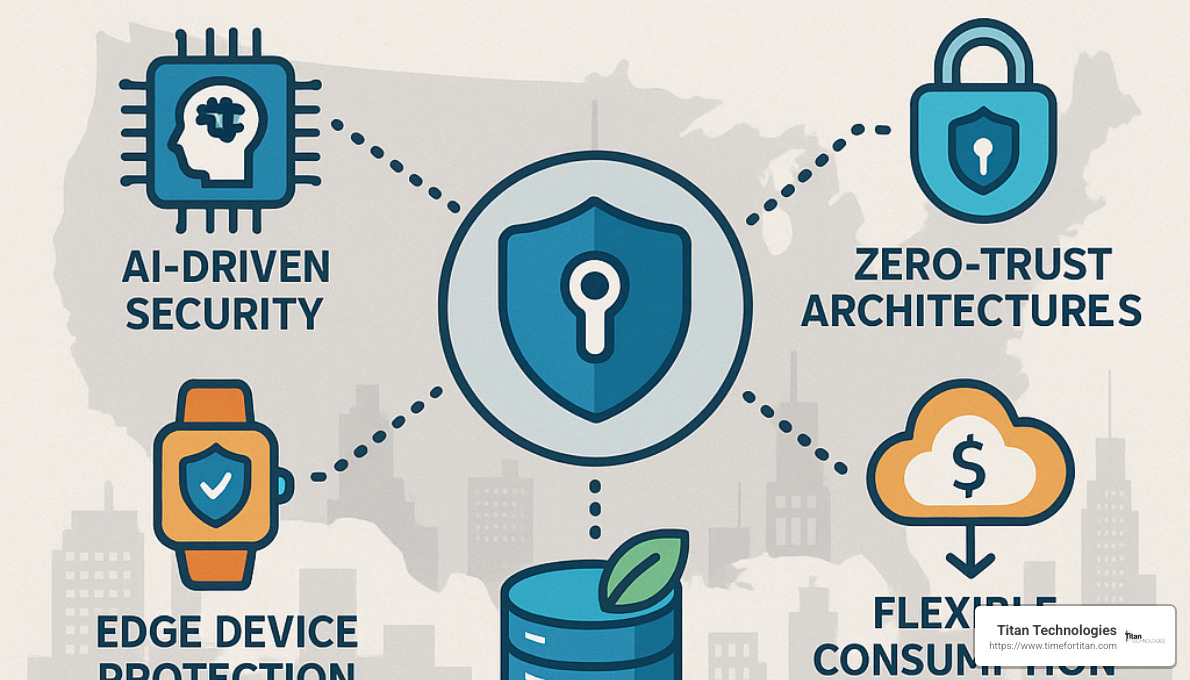
Emerging Trends & Future Outlook for Data Protection as a Service
The data protection as a service landscape continues to evolve rapidly, with several exciting developments on the horizon.
AI-driven anomaly detection is revolutionizing how we identify potential threats. Rather than relying on signature-based detection (which can miss new threats), these systems establish baseline activity patterns and flag unusual behaviors that might indicate ransomware or insider threats before they compromise your backups.
The concept of zero-trust backup architectures is gaining traction, applying the “never trust, always verify” principle to backup infrastructure. This approach requires multi-factor authentication for all access and treats internal systems with the same security scrutiny as external ones – because in today’s threat landscape, perimeter security alone isn’t enough.
As more data is generated at the edge – in remote offices, field locations, and IoT devices – providers are developing specialized edge protection capabilities to efficiently protect these distributed environments despite bandwidth constraints. This trend is particularly relevant for our clients with multiple locations throughout New Jersey.
Sustainable storage practices are becoming increasingly important as organizations consider their environmental impact. Energy-efficient storage, intelligent data tiering to reduce carbon footprint, and responsible hardware lifecycle management are now factors in provider selection for environmentally conscious businesses.
Finally, flexible marketplace consumption models are emerging that allow organizations to select and deploy specific protection capabilities on demand. These app-store-like interfaces simplify procurement and eliminate long-term commitments, giving businesses in Edison, Elizabeth, and throughout Central New Jersey more control over their data protection strategy.
At Titan Technologies, we help our clients stay ahead of these trends, ensuring their data protection approach evolves alongside industry developments rather than playing catch-up when it’s already too late.
Conclusion
The evolution from traditional backup solutions to comprehensive data protection as a service represents a fundamental shift in how organizations approach data resilience. This change couldn’t come at a more critical time, as the volume and value of business data continue to grow exponentially while threats like ransomware become increasingly sophisticated.
When we talk with our clients across New Jersey, we find that most are surprised by just how transformative this approach can be. It’s not just about backing up files anymore—it’s about creating a complete shield around your organization’s most valuable asset: your data.
The benefits of adopting a DPaaS approach are genuinely compelling. You’ll see reduced capital expenditure through subscription-based pricing that eliminates those painful hardware refresh cycles. Your security posture improves dramatically with purpose-built protections against modern threats like ransomware. Compliance becomes simpler with automated policy enforcement that keeps you on the right side of regulations without constant manual oversight.
Many of our clients in Princeton and Newark particularly appreciate the simplified management that comes from unifying protection across their diverse environments. No more juggling three or four different backup solutions! And when disaster does strike, the accelerated recovery with orchestrated restoration processes means you’re back in business faster than ever before.
For businesses throughout Central New Jersey—from healthcare providers in Princeton to manufacturers in New Brunswick and retailers in Woodbridge—data protection as a service offers a path to improved resilience without the complexity and cost of traditional solutions.
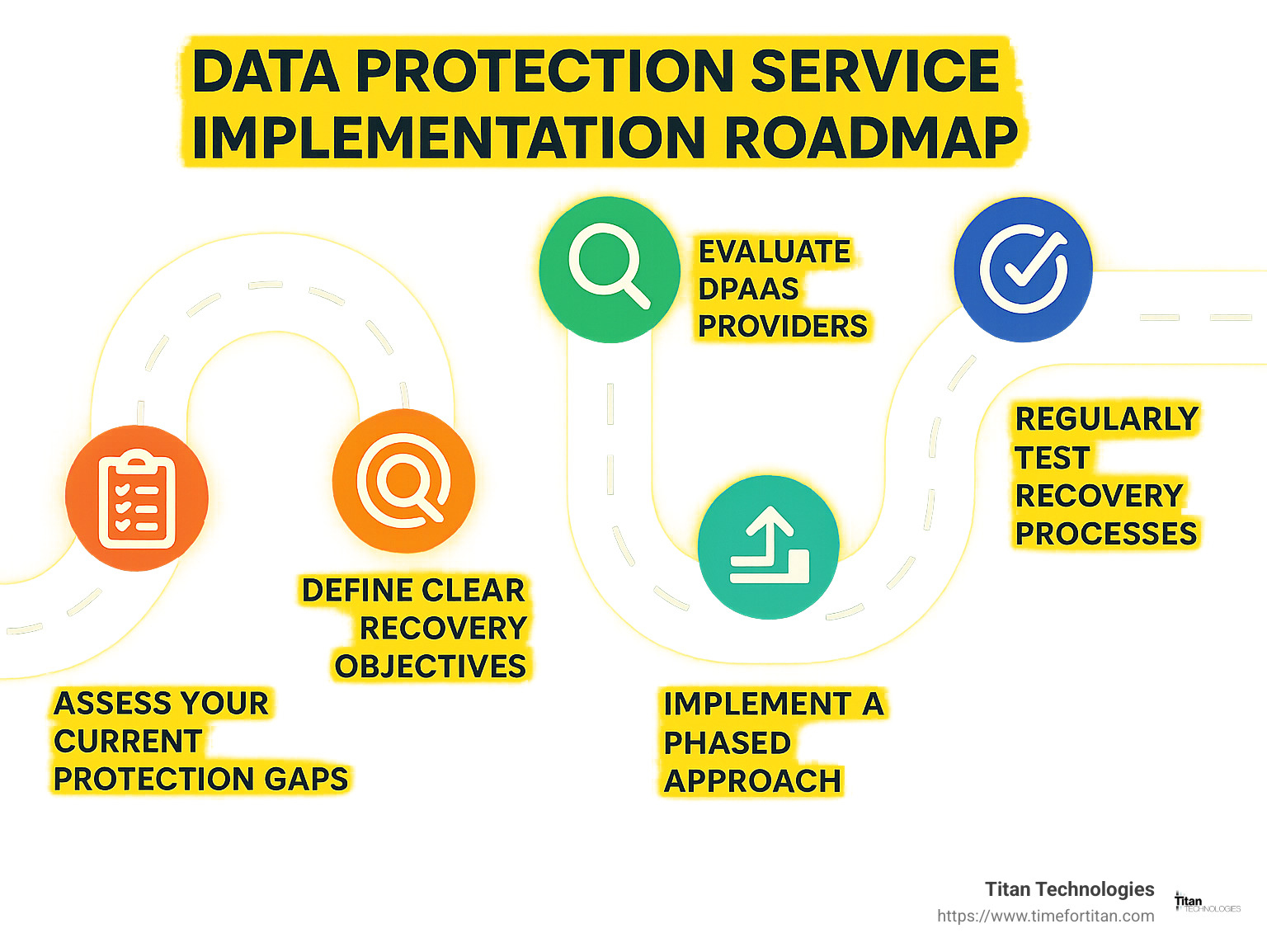
As you consider your organization’s data protection strategy, we recommend these action steps:
- Assess your current protection gaps by evaluating recovery capabilities against potential threats
- Define clear recovery objectives for different data types based on business impact
- Evaluate DPaaS providers using the criteria outlined in this guide
- Implement a phased approach starting with your most critical systems
- Regularly test recovery processes to validate protection effectiveness
At Titan Technologies, we’ve seen how the right data protection approach can transform a business’s resilience. One client in Freehold told us they used to worry about backups every single day—now they haven’t thought about them in months because they know everything is protected.
We specialize in helping businesses across Central New Jersey implement effective data protection as a service solutions custom to their specific needs. Our team brings decades of experience in data security, backup technologies, and disaster recovery to ensure your critical information remains protected against both current and emerging threats.
With offices serving Edison, Elizabeth, Lakewood, Newark, Trenton, Princeton, New Brunswick, Matawan, Woodbridge, Freehold, and Red Bank, we provide local, responsive support backed by deep technical expertise. Our 100% satisfaction guarantee ensures that your data protection implementation meets the highest standards of reliability and performance.
To learn more about how Titan Technologies can help safeguard your business data through comprehensive protection services, visit our Services & Solutions page or contact our team for a personalized consultation.
In today’s digital business environment, effective data protection isn’t just an IT concern—it’s a fundamental business requirement. With the right data protection as a service strategy, you can transform this requirement from a burden into a competitive advantage through improved resilience, compliance, and operational efficiency. Your data deserves nothing less.